Detection method and processing system based on online abnormal network message propagation
A technology of network information and detection methods, applied in network data retrieval, website content management, electronic digital data processing, etc., can solve problems such as economic loss, social panic, crowd panic, etc., to ensure safety and health, reasonable processing methods, The effect of reducing the number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
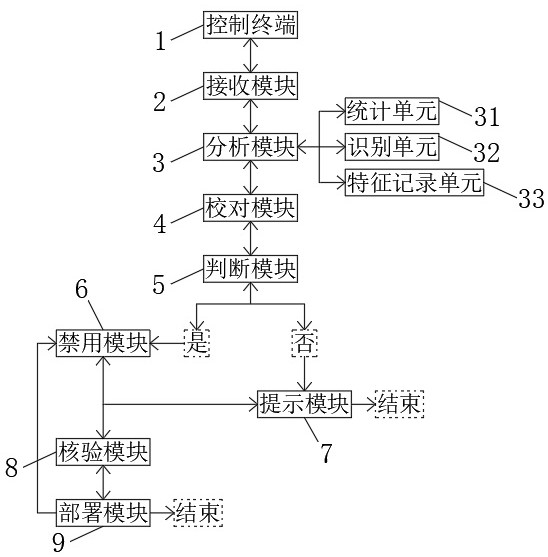
Image
Examples
Embodiment 1
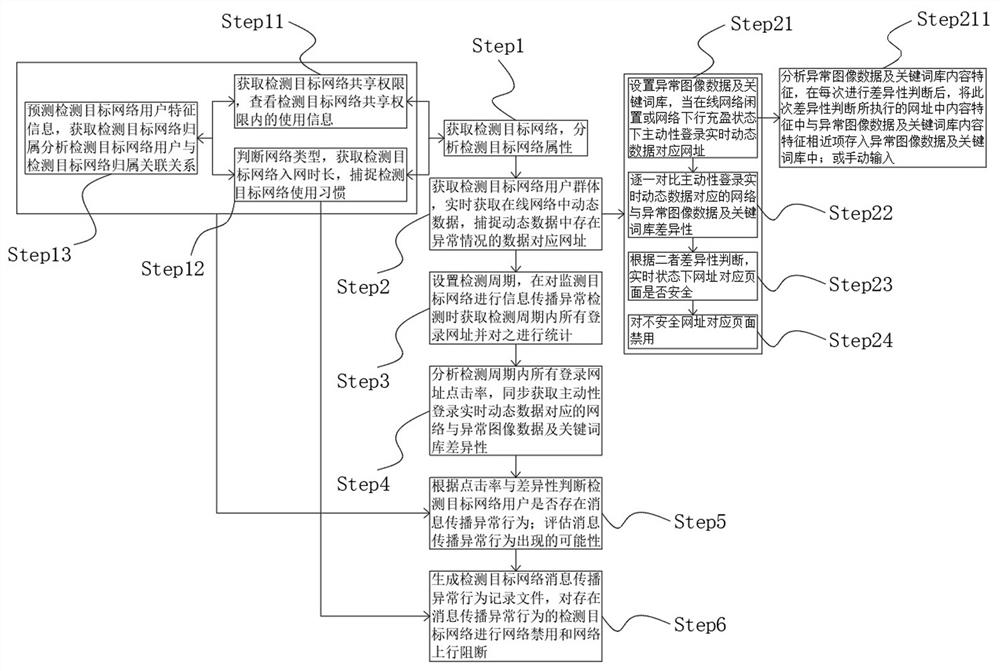
[0057] The detection method based on online abnormal network message propagation in this embodiment, such as figure 1 shown, including the following steps:
[0058] Step1: Obtain the detection target network and analyze the properties of the detection target network;
[0059] Step2: Obtain and detect the target network user groups, obtain dynamic data in the online network in real time, and capture the corresponding URLs of the abnormal data in the dynamic data;
[0060] Step3: Set the detection period, and obtain all login URLs within the detection period and make statistics on them when detecting the abnormal information dissemination of the monitoring target network;
[0061] Step4: Analyze the click-through rate of all login URLs within the detection period, and simultaneously obtain the difference between the network and abnormal image data and keyword database corresponding to the real-time dynamic data of active login;
[0062] Step5: According to the click-through ra...
Embodiment 2
[0065] At the specific implementation level, on the basis of Embodiment 1, this embodiment refers to figure 1 The detection method of the online abnormal network message propagation in the embodiment 1 is shown in further detail, such as figure 1 As shown, step Step1 includes the following sub-steps:
[0066] Step11: Obtain the network share permission of the detection target, and view the usage information within the network share permission of the detection target;
[0067] Step12: Determine the network type, obtain the network access time of the detection target network, and capture the usage habits of the detection target network;
[0068] Among them, the network type judgment and distinction include the following two methods: local area network, metropolitan area network, wide area network, and personal network; star network, ring network, and bus network.
[0069] Step13: Predict the characteristic information of the detection target network users, obtain the detection...
Embodiment 3
[0072] At the specific implementation level, on the basis of Embodiment 1, this embodiment refers to figure 1 The detection method of the online abnormal network message propagation in the embodiment 1 is shown in further detail, such as figure 1 As shown, the following sub-steps are included in step Step2:
[0073] Step21: Set up abnormal image data and keyword database, and actively log in to the website corresponding to the real-time dynamic data when the online network is idle or the network is full of downlink;
[0074] Step22: Compare the difference between the network and abnormal image data and keyword database corresponding to the active login real-time dynamic data one by one;
[0075] Step23: According to the difference between the two, judge whether the corresponding page of the URL is safe in the real-time state;
[0076] Step24: Disable the pages corresponding to insecure URLs.
[0077] Such as figure 1 As shown, the step-by-step extension in step Step21 has ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com