Network security policy AI autonomous defense method and system based on security ontology modeling
A strategy and security technology, applied in the field of network information security, can solve the problems of inefficient early warning, difficult to guarantee the effectiveness of security defense, difficult to adapt to the rapid evolution of attack methods and behaviors, etc., to achieve the effect of improving network security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
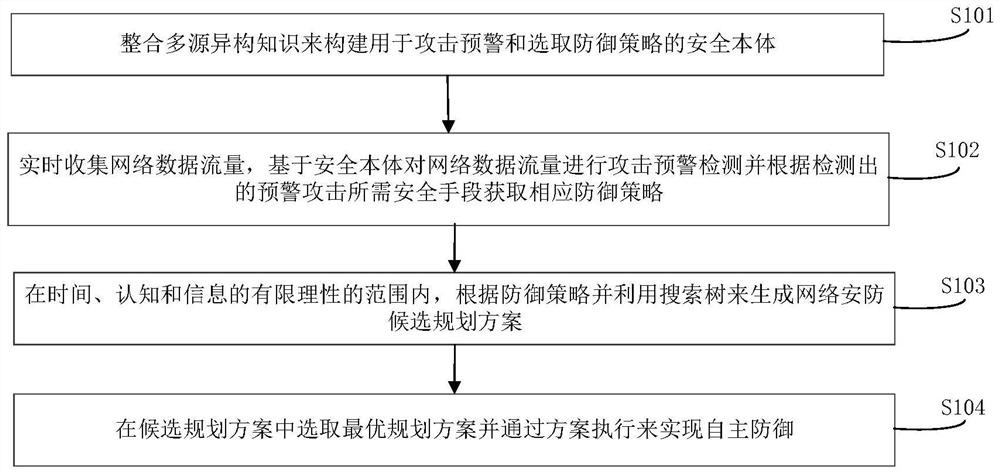
[0042] An embodiment of the present invention provides an AI autonomous defense method for network security strategies based on security ontology modeling, see figure 1 As shown, it contains the following content:
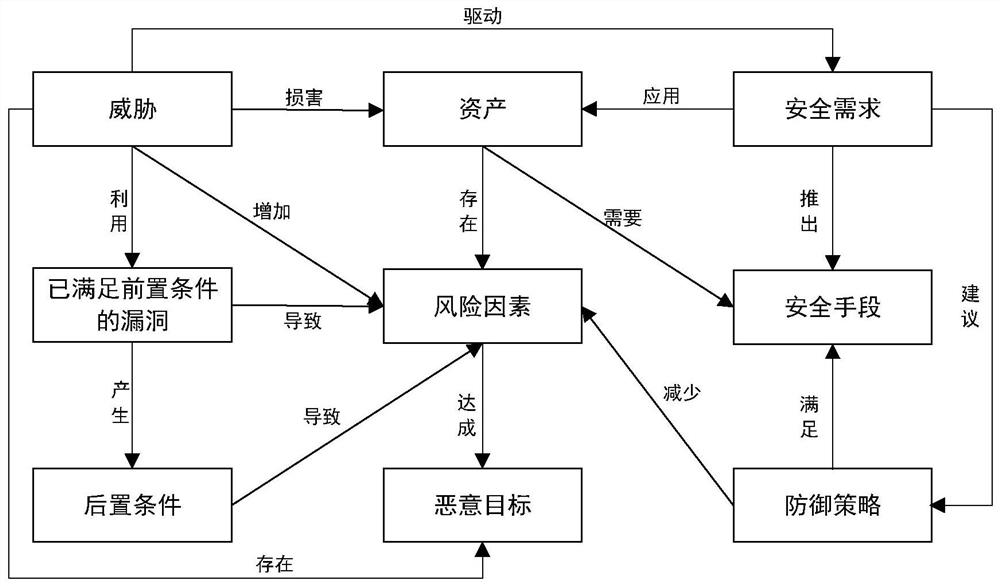
[0043] S101. Integrate multi-source heterogeneous knowledge to construct a security ontology for early warning of attacks and selection of defense strategies;
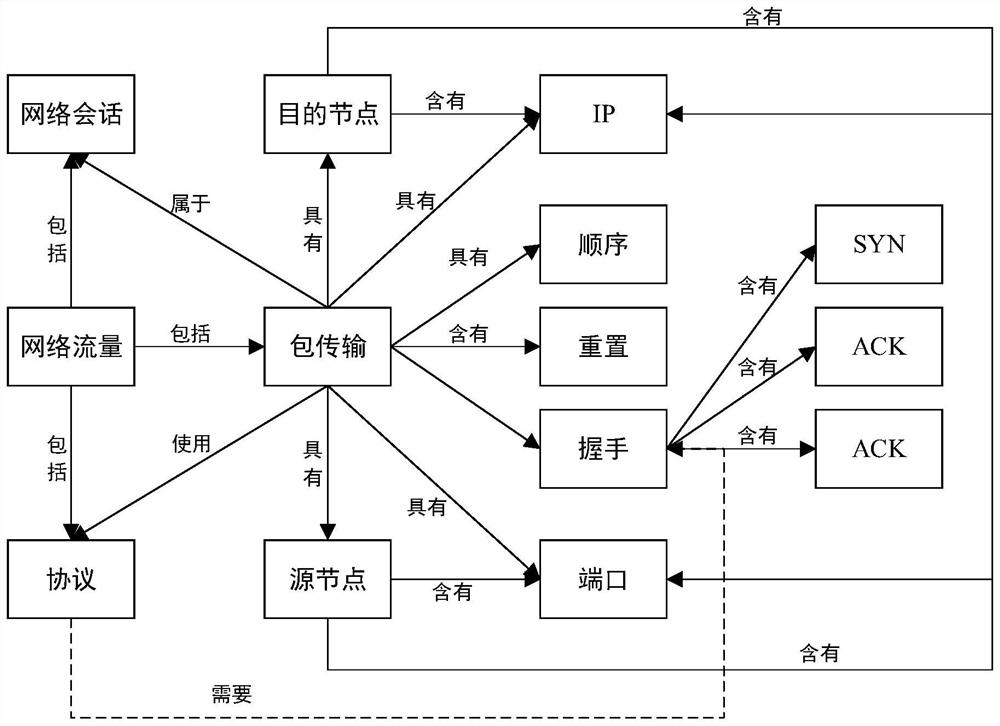
[0044] S102. Collect network data traffic in real time, perform attack warning detection on network data traffic based on the security ontology, and obtain corresponding defense strategies according to the detected security means required for early warning attacks;
[0045] S103. Within the bounded rationality of time, cognition and information, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com