Power monitoring system network security policy arrangement and disposal method and system
A power monitoring and system network technology, applied in circuit devices, information technology support systems, genetic rules, etc., can solve the problems of effective alarm flooding, low efficiency, lack of standardized response, and processing procedures, etc., to improve clarity and real-time performance , to ensure the effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
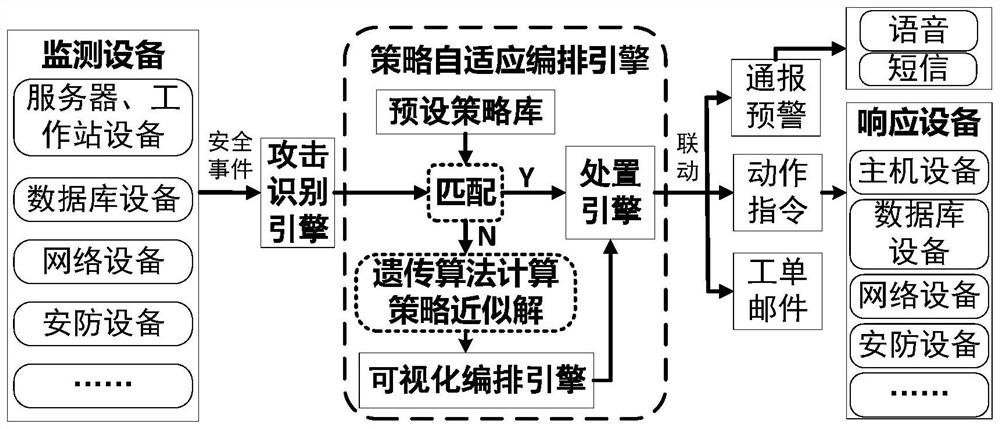
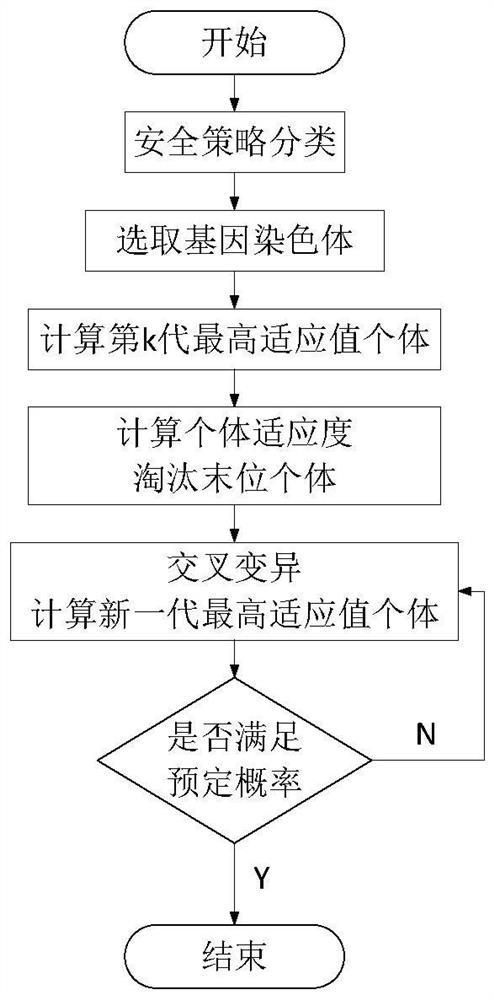
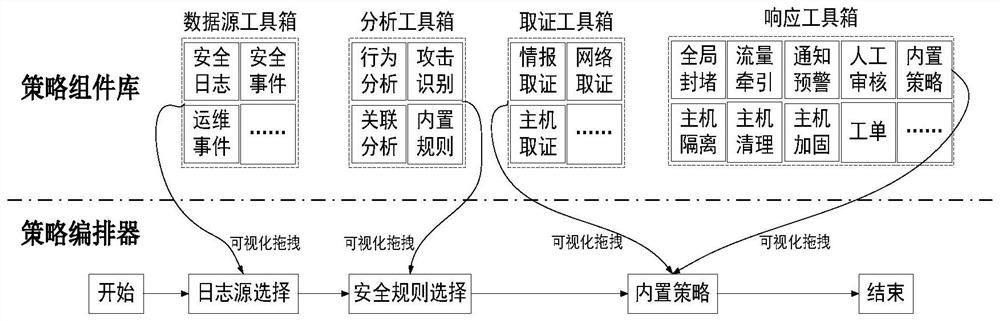
[0044] Embodiment 1: An electric power monitoring system network security policy arrangement and disposal system, including an attack identification engine (i.e. an attack identification module), a policy adaptive arrangement engine (i.e. a strategy adaptive arrangement module), a visual arrangement engine (i.e. a visual arrangement module) and A disposition engine (i.e. a disposition module) that performs tasks such as figure 1 The self-adaptive orchestration and disposal process of the security policy shown includes:
[0045] Step 1. The attack identification engine monitors the internal equipment security events of the power monitoring system.
[0046] Monitor the security events of each device in the power monitoring system collected by the network security monitoring device, realize the analysis of security events, and clarify the data source and data type.
[0047]The types of collection objects and the content of security events mainly include: server and workstation e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com