Power consumption data anomaly detection method and system based on big data analysis
A technology of electricity consumption data and anomaly detection, applied in data processing applications, electrical digital data processing, information technology support systems, etc., can solve problems such as breaking the normal order of electricity consumption, affecting the safety of power grid operation, and damage to power equipment such as transformers. Achieve the effects of reducing the number and the scope of electric stealing detection, reducing the difficulty of investigation, and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
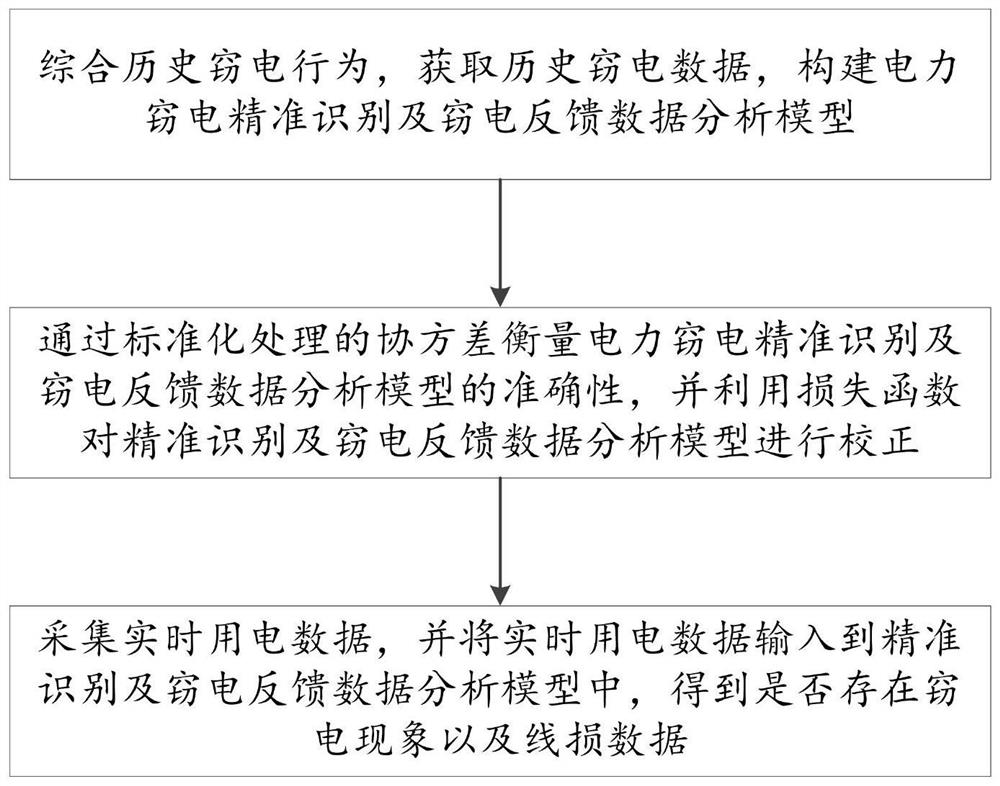
[0037] The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, rather than all the embodiments. Based on the embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present invention.
[0038] Electricity theft and fraudulent use of electricity have caused great economic losses to electric power enterprises. Although electric power enterprises have invested a lot of manpower and material resources to carry out detection and positioning, due to the various means of electric theft and the continuous updating of technical means, electric power enterprises can locate and detect electricity theft. brings great difficultie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com