Track privacy protection method based on false track technology
A privacy protection and trajectory technology, applied in the field of privacy protection, can solve the problems of large differences, achieve the effect of protecting location privacy and ensuring trajectory privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] A method for protecting trajectory privacy based on fake trajectory technology in this embodiment, such as Figure 1-Figure 3 shown, including the following steps:
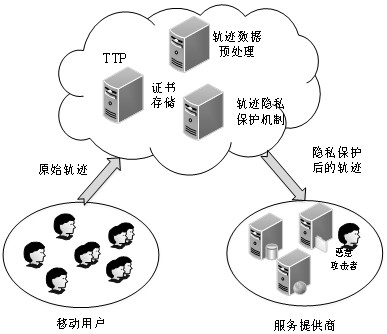
[0047] Step S1. The mobile user interacts with the service provider through a trusted third party;
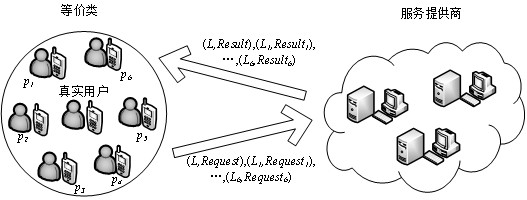
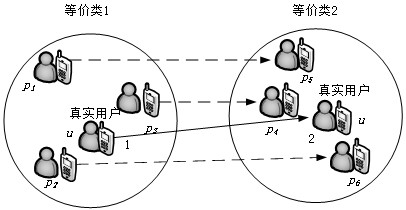
[0048] Step S2. Within the unit time interval T, the mobile user moves from the position X to the position Y, and selects k user partners to form two equivalence classes, so as to ensure that the attacker can identify the real user position points from the user position points in the equivalence class. The probability of 1 / k is 1 / k, which realizes the user's location privacy protection;
[0049] Step S3. When the user selects the equivalence class, calculate the distance between the surrounding users and the real user through the Euclidean distance, and select the k users closest to the user to form an equivalence class;
[0050] Step S4. In the time interval T, calculate the distance between the user part...
Embodiment 2
[0054] This embodiment is further optimized on the basis of Embodiment 1, and step S1 includes:
[0055] Step S1.1. The mobile user carries a mobile device with a positioning function, accurately locates and completes the task of collecting various types of data according to the mobile device, and then interacts with the LBS application; the mobile users do not trust each other;
[0056] Step S1.2. The trusted third party includes a certificate storage module, a trajectory data preprocessing module, and a privacy protection processing module; as an independent organization, the trusted third party will not disclose relevant information of users, and users in the equivalence class trust certificates from trusted third parties;
[0057] Step S1.3. The mobile user sends the information with the location information and the query request to the service provider, and the service provider returns the query result to the mobile user after calculation, and the service provider is not ...
Embodiment 3
[0060] This embodiment is further optimized on the basis of the above-mentioned Embodiment 1 or 2, and this embodiment discloses:
[0061] Communication between mobile users does not include their real location information.
[0062] The other parts of this embodiment are the same as the above-mentioned Embodiment 1 or 2, and thus are not repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com