Internet of Things operating system and method based on MQTT
An operating method and operating system technology, which is applied in the field of MQTT-based IoT operating systems, and can solve problems such as undefined communication methods for IoT devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
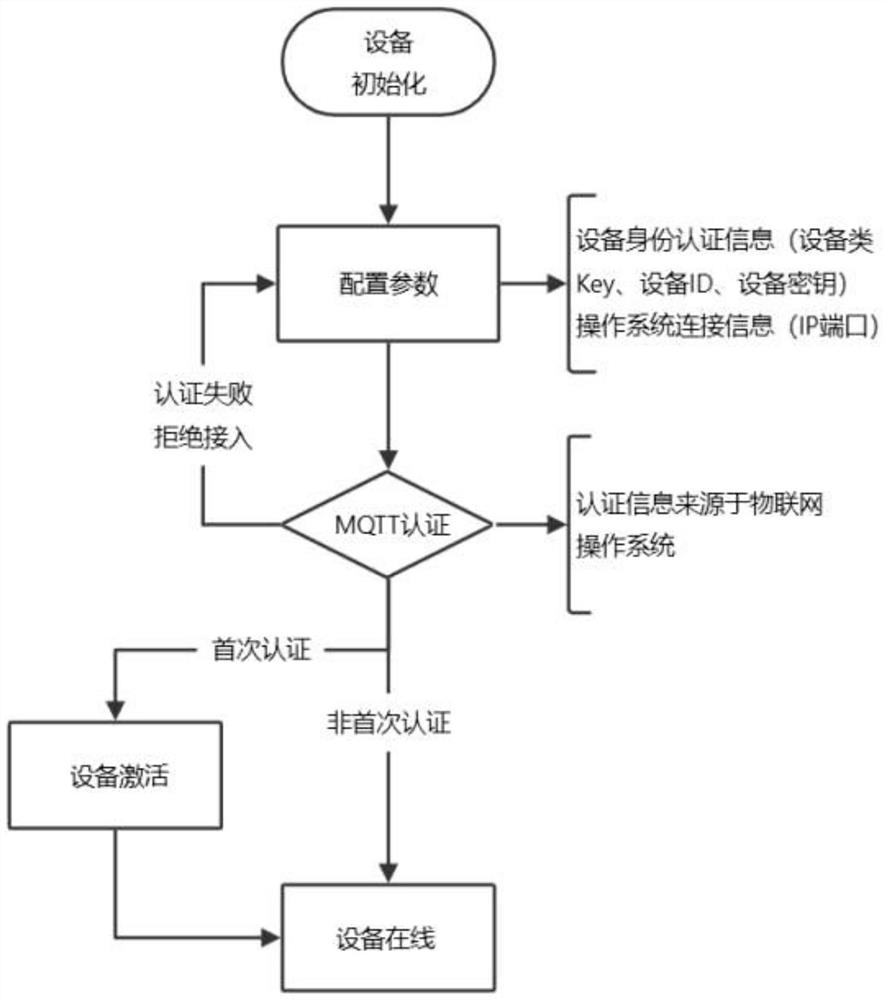
[0035] This embodiment provides an MQTT-based IoT operation method, including the following steps:
[0036] S1 publisher device initialization, configuring device identity authentication information and operating system connection information;
[0037] S2 obtains the authentication information from the IoT operating system and performs MQTT authentication. If the authentication fails, the access is rejected and returns to S1; if the authentication is successful, it enters S3;
[0038] S3 judges whether the authentication passed information is the first authentication, if so, the device is activated, if not, it goes to S4;
[0039] S4 is connected to the proxy server by MQTT to realize the device online, and online keep alive through the keep alive logic of MQTT, and then carry out data interaction.
[0040] In this embodiment, after the device is initialized and configured, if the authentication is not successful and the authentication is not passed for the first time, the de...
Embodiment 2
[0045] On the basis of Embodiment 1, this embodiment is further refined, as follows:
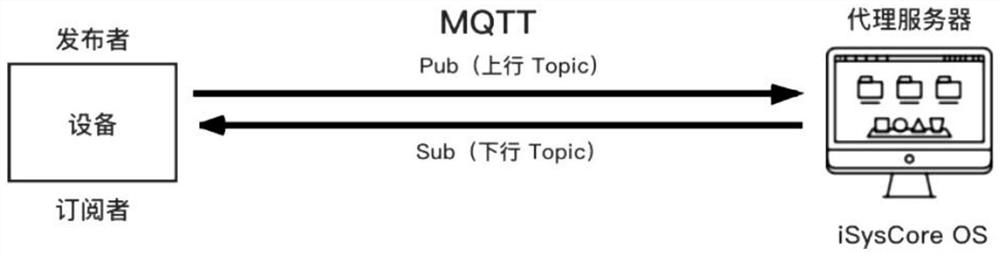
[0046] There are three roles in the MQTT protocol in this embodiment: a proxy server, a publisher, and a subscriber. In iSysCoreOS, the device is both a publisher and a subscriber of messages. MQTT sends data upward to iSysCoreOS (proxy server) through the "upstream topic", that is, the device (publisher); and then through the "downstream topic", that is, iSysCoreOS (proxy server) sends data to each subscription that subscribes to the "Topic" , including the device.
[0047] Topic in this embodiment is a transmission medium for devices to publish (Pub) and subscribe (Sub) messages.
[0048] In this embodiment, the upstream topic format is up / dev / {pk} / {devId};
[0049] In this embodiment, the downlink topic format is down / dev / {pk} / {devId};
[0050] In the topic format of this embodiment, the upstream up / dev and downstream down / dev of the first and second levels of the topic are the prefix...
Embodiment 3
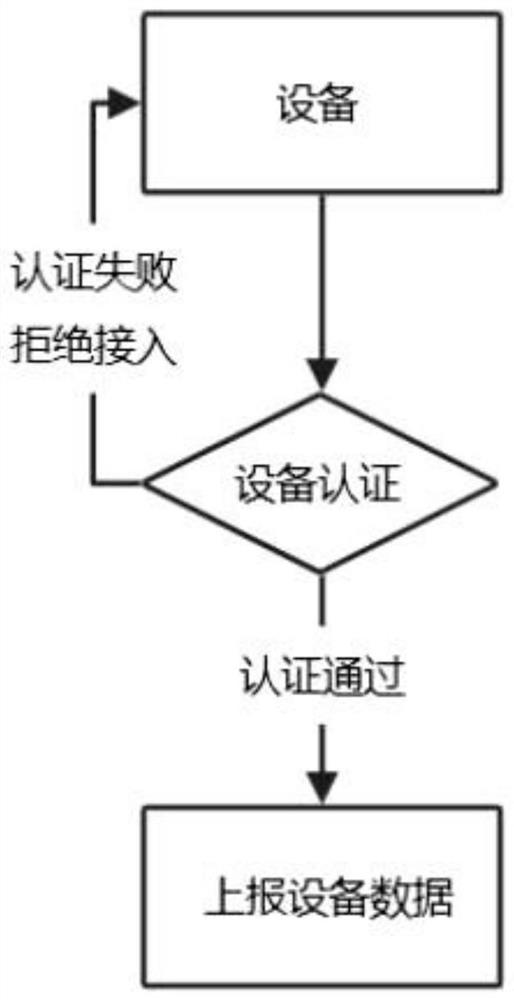
[0056]On the basis of Embodiment 1, in this embodiment, in the IoT operating system, different types of states are defined for each device according to the characteristics of the MQTT protocol itself, which are activated state and online state respectively. figure 1 shown.
[0057] The inactive state in the activation state in this embodiment means that after the device is created and has not been authenticated successfully, the default is the inactive state.
[0058] The activation state in the activation state of this embodiment is that the device authentication is performed by authority authentication through the connection parameters (username, password) of MQTT. Therefore, as long as the MQTT connection is successful, the device passes the authentication. Passing the authentication means that the platform activates the device, the device and the system. Data can only be transmitted, and the activation state of the device is irreversible.
[0059] The online status of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com