Data encryption method and device, electronic equipment and readable storage medium
A data encryption and data technology, which is applied in the direction of secure communication devices, electrical components, digital transmission systems, etc., can solve the problems of low data transmission security and easy leakage of data encryption keys, etc., to solve the problems of easy leakage and guaranteed complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
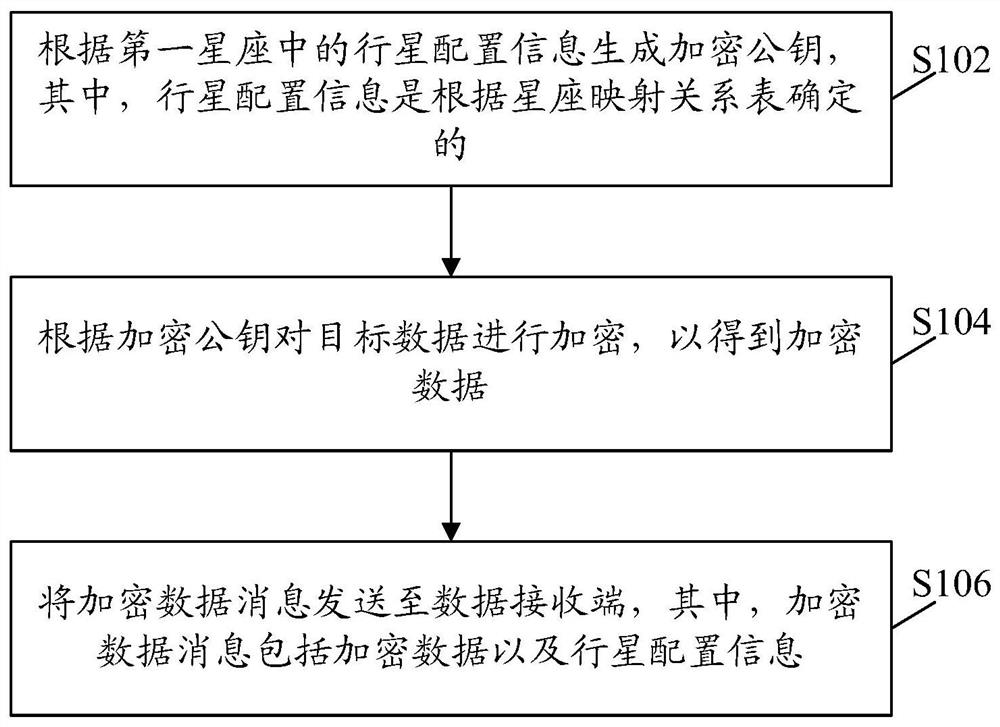
[0024] According to an embodiment of the present invention, a data encryption method is provided, such as figure 1 As shown, the method may specifically include the following steps:
[0025] S102, generating an encryption public key according to the planet configuration information in the first constellation, wherein the planet configuration information is determined according to the constellation mapping relationship table;
[0026] S104, encrypting the target data according to the encryption public key to obtain encrypted data;
[0027] The data sending end and the data receiving end in this embodiment include but are not limited to servers, terminals, etc. The data sending end and the data receiving end can perform data processing and data transmission. In this embodiment, the data sending end and the data receiving end do not perform limit.
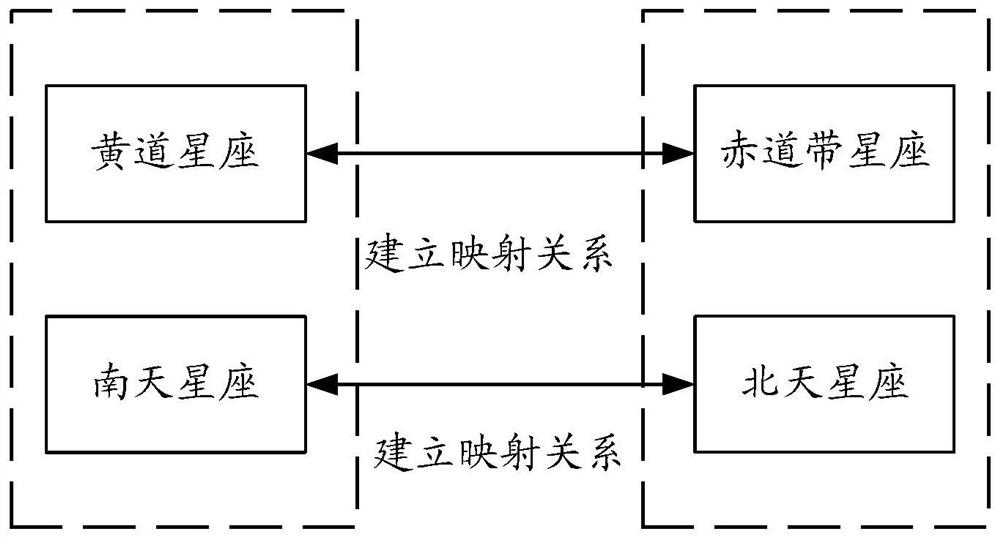
[0028] In this embodiment, the constellation mapping relationship table is pre-established and stored in the database of the data ...
Embodiment 2
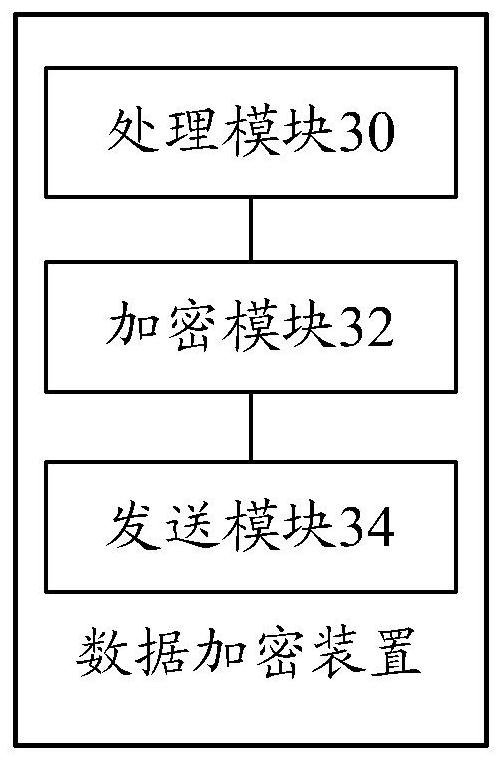
[0058] A data encryption device provided by an embodiment of the present invention is introduced in detail.
[0059] refer to image 3 , showing a schematic structural diagram of a data encryption apparatus in an embodiment of the present invention.
[0060] The application program loading apparatus in the embodiment of the present invention includes: a processing module 30 , an encryption module 32 and a sending module 34 .
[0061] The functions of each module and the interaction between the modules are described in detail below.
[0062] A processing module 30, configured to generate an encryption public key according to planet configuration information in the first constellation, wherein the planet configuration information is determined according to a constellation mapping relationship table;
[0063] an encryption module 32, configured to encrypt the target data according to the encryption public key to obtain encrypted data;
[0064] The sending module 34 is configur...
Embodiment 3
[0077] Preferably, an embodiment of the present invention further provides an electronic device, comprising: a memory, a processor, and a computer program stored in the memory and running on the processor, the computer program being executed by the processor Steps to implement the data encryption method as described above when executed.
[0078] Optionally, in this embodiment, the memory is configured to store program codes for performing the following steps:
[0079]S1, generating the encryption public key according to the planet configuration information in the first constellation, wherein the planet configuration information is determined according to the constellation mapping relationship table;
[0080] S2, encrypting the target data according to the encryption public key to obtain encrypted data;
[0081] S3: Send an encrypted data message to a data receiving end, where the encrypted data message includes the encrypted data and the planet configuration information.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com