Secure multicast method for overlay network at low expenses
A secure multicast and overlay network technology, applied in the field of data communication, can solve the problems of NICE protocol not considering data security transmission, high node forwarding complexity, affecting multicast performance, etc., so as to reduce data forwarding load and improve data distribution efficiency , Improve the effect of data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
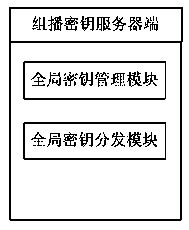
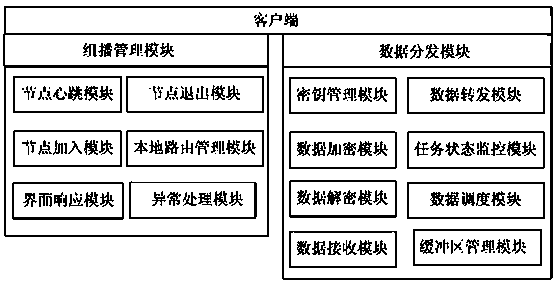
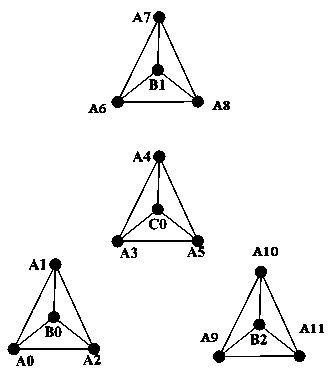
[0037] The invention adopts a layered clustering multicast tree construction method, releases the sub-node overhead of the cluster head node, and adopts a data differentiated encryption transmission mode to ensure safe data transmission and improve the robustness of the system at the same time. In terms of deployment, the system can be divided into multicast management server, key management server and client; in terms of function, it can be divided into multicast management module, data distribution module and key management module. The basic principle is as follows: a bottom-up hierarchical clustering strategy is used to construct a multicast tree, and by cutting the number of child nodes of the cluster head, the complexity of maintaining and controlling the topology of all nodes is constant, ensuring that the node overhead does not increase with the group size and aggravated; the self-balancing binary tree algorithm is used in the cluster to build a multicast distribution pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com