Random number used communication safety identification method
A technology of communication security and authentication method, which is applied in the field of communication security authentication using random numbers, and can solve problems such as loss of security in information transmission and cracking of encryption algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Specific embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
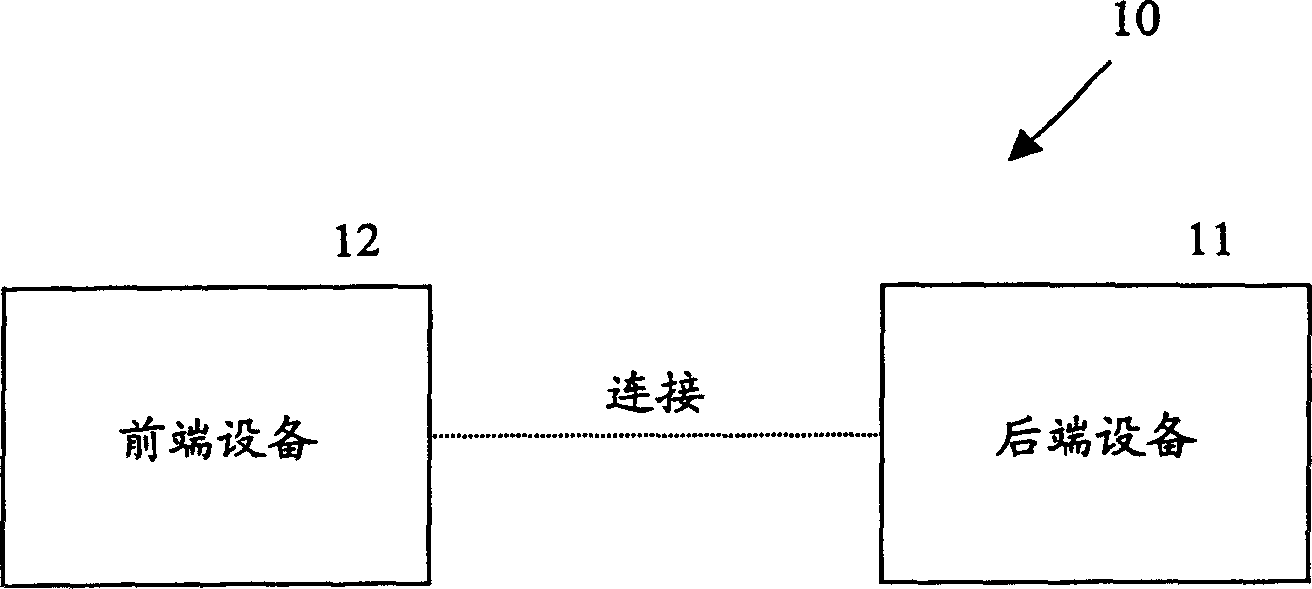
[0033] figure 1 It is an authentication system 10, which includes a front-end device 12 and a back-end device 14, and information can be exchanged between the two through a wired or wireless connection. In practice, front-end and back-end devices can be any pair of devices capable of communicating information. For example, ATMs and bank account systems, two network terminals, electronic keys and access control.
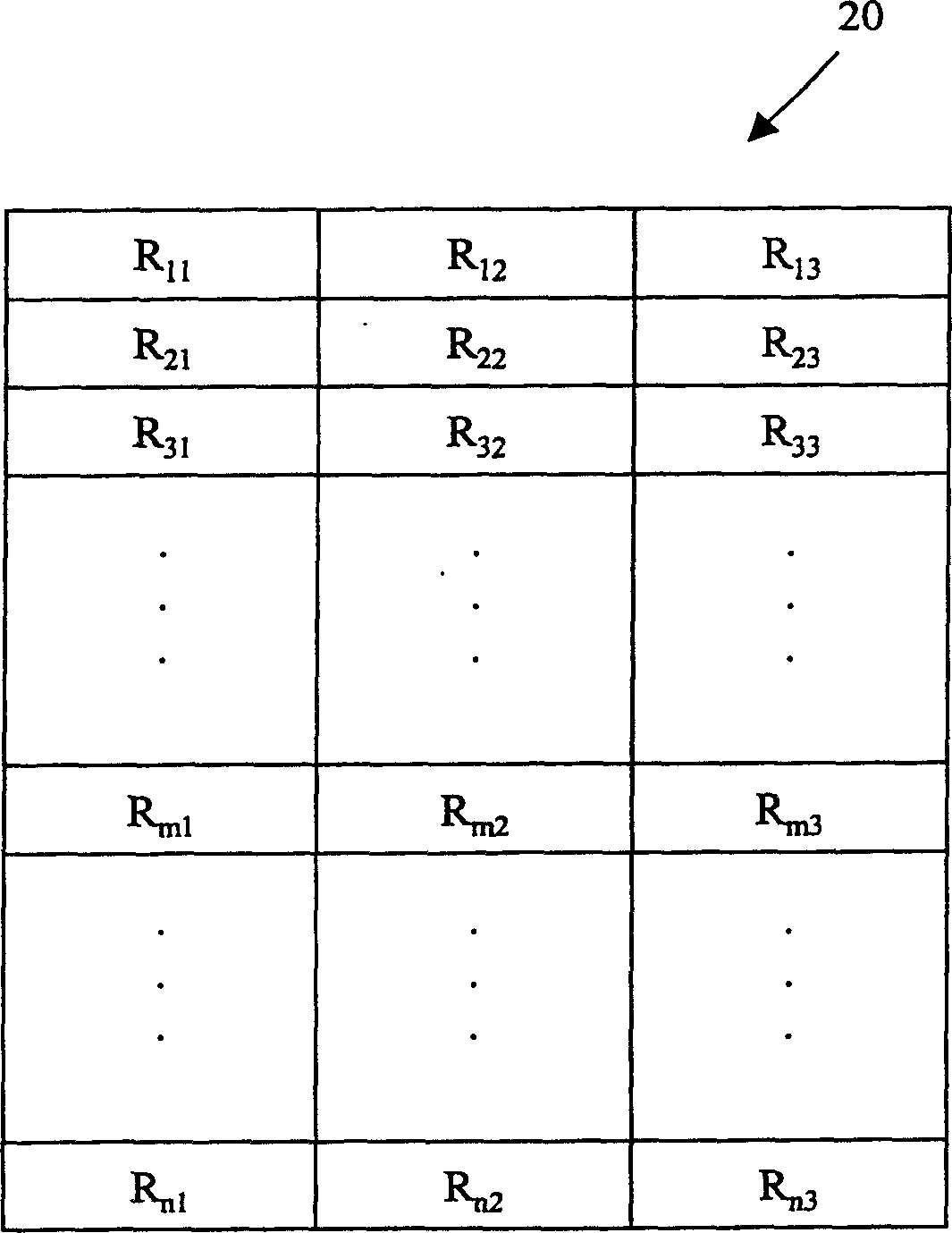
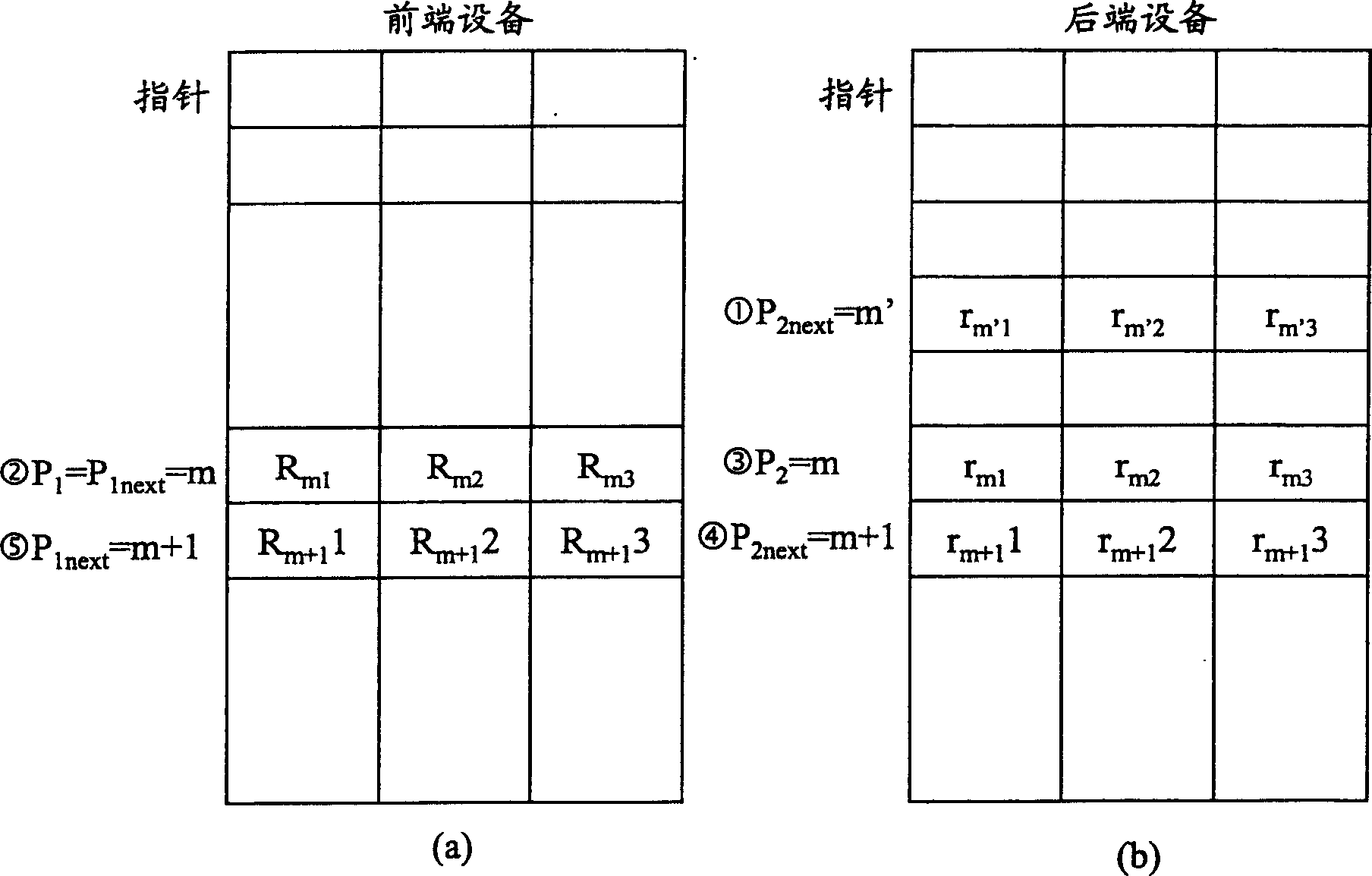
[0034] In the security authentication method of the present invention, a random number table is generated by the management institution. Here, for the above-mentioned paired devices, the management agencies may be banks, network providers, or enterprise management departments. In some cases, the governing body can also be either of the two paired devices. The management agency assigns the generated random number table and the identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com