Method for locking network equipment
A technology of network equipment and equipment, which is applied in the field of communication, can solve problems such as easy theft, central equipment is easy to disguise, increase network overhead, etc., and achieve the effects of reducing accidental losses, preventing theft, and reducing communication traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
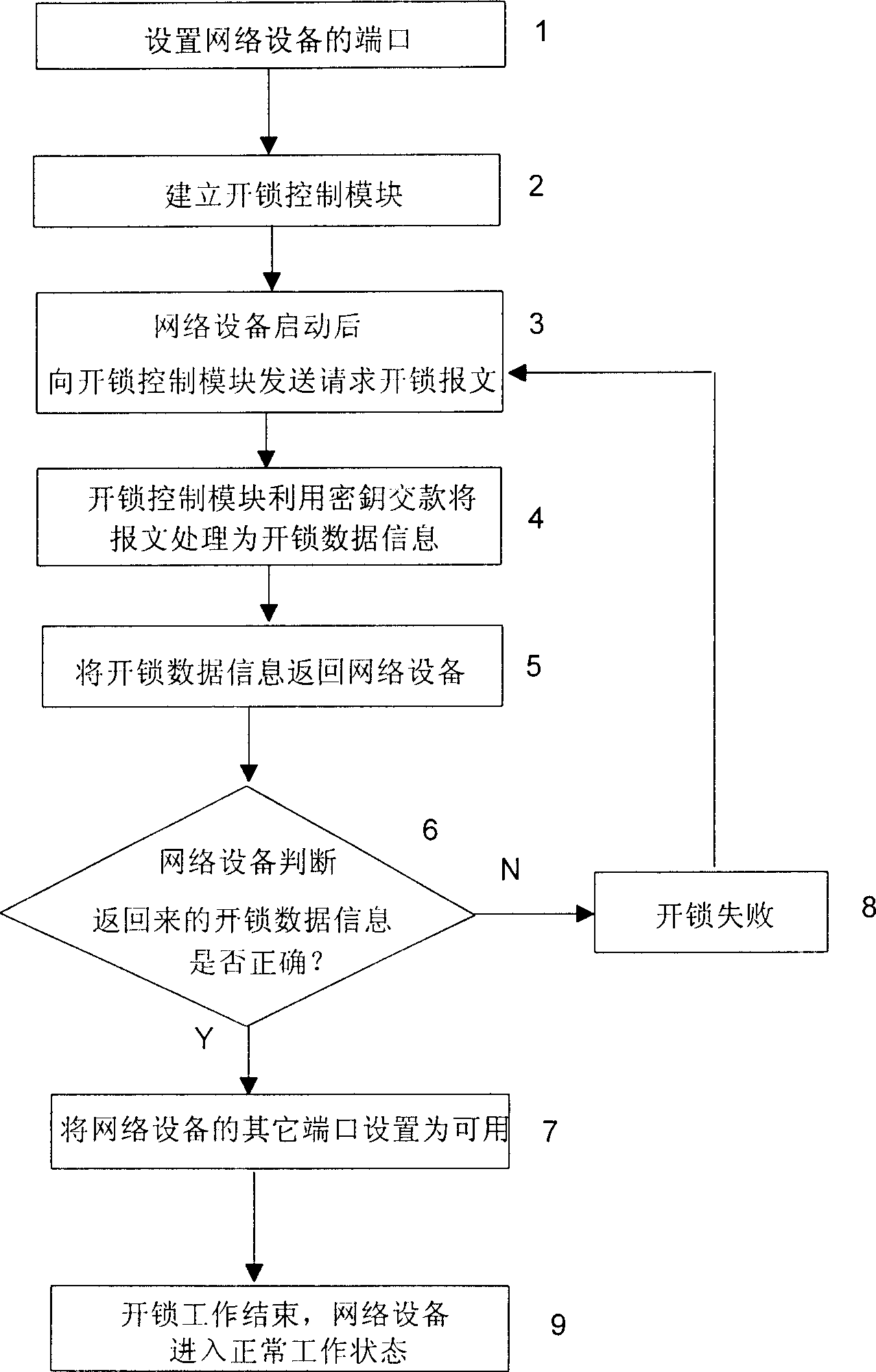
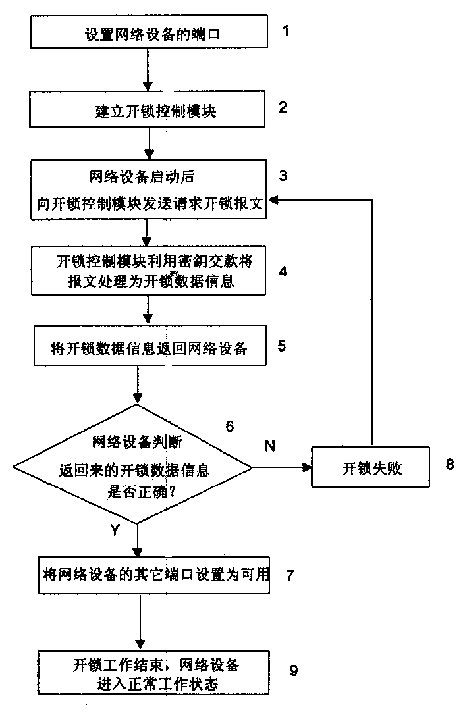
[0016] The specific embodiment of the present invention is described as follows in conjunction with accompanying drawing: the method for locking network equipment comprises:
[0017] Step 1: Set up the ports of the network device: set some ports of the network device to be available after startup, and some ports to be available after startup and unlocking. The port used by the control module for communication is set to be available after startup;
[0018] Step 2: Establish an unlocking control module in the network for processing the unlocking request sent by the network device and controlling the unlocking of the network device; the unlocking control module manages the network device identification of each network device in the network and the key corresponding to the network device At the same time, it can process the unlocking request sent by the network device to realize effective control of whether the network device is unlocked. The unlocking of the network device means ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com