Method of guarding network attack
A network attack and network equipment technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of source address spoofing attacks, occupation of resources, crashes, etc., to achieve simple implementation, low resource occupation, and high efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
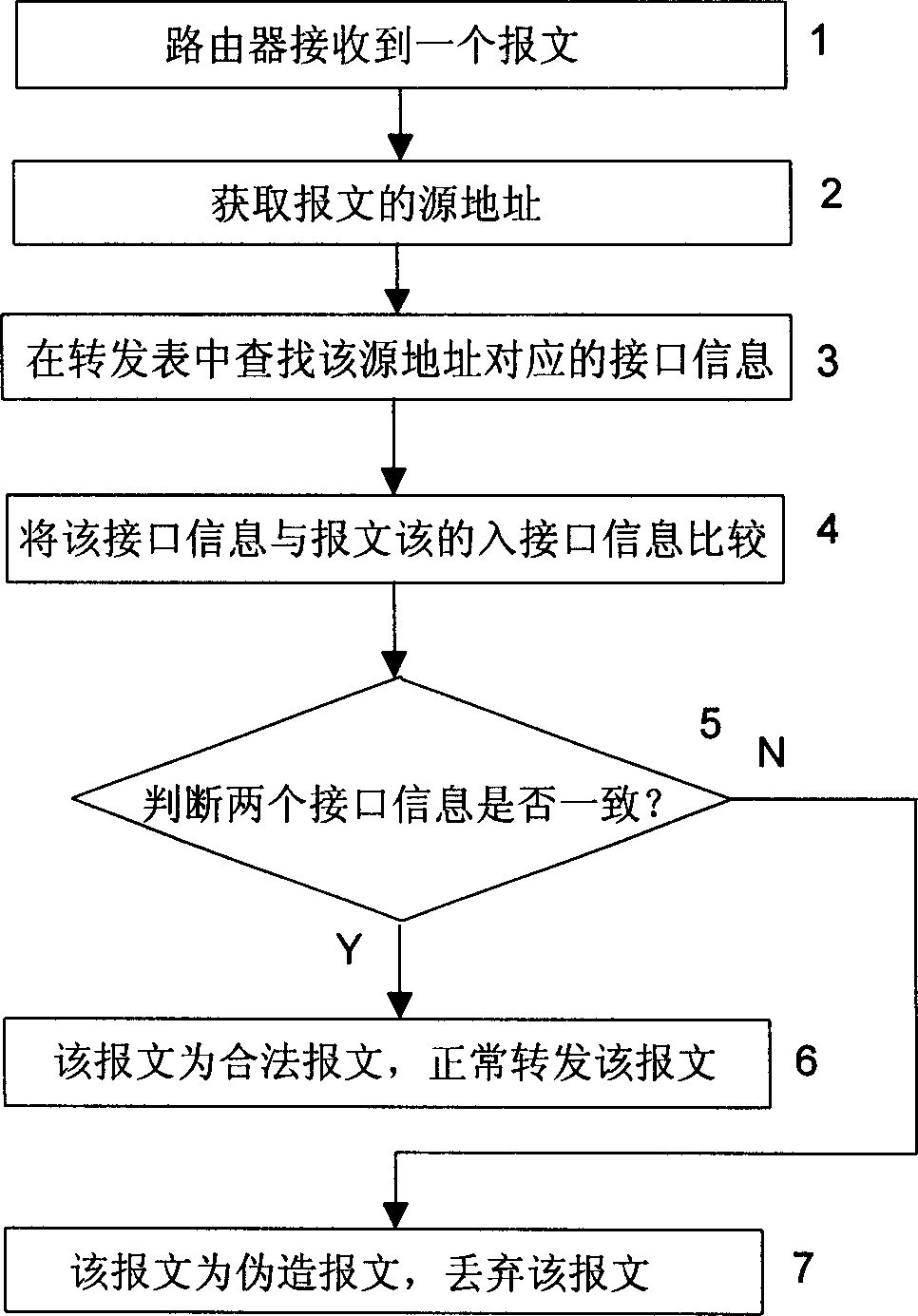
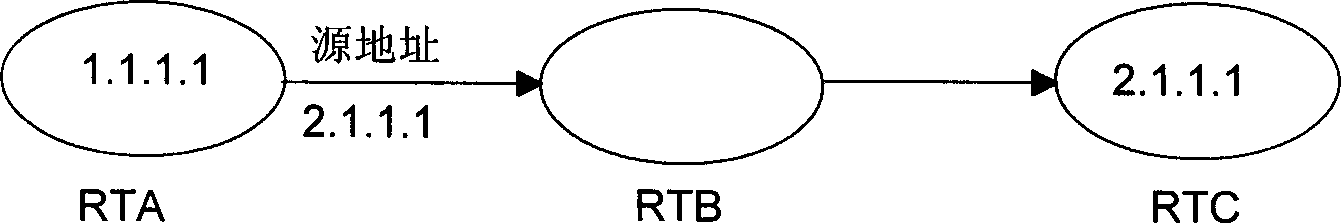
[0023] Normally, after receiving a message, a router on a network device will look up the routing table according to the destination address of the message. If it finds the outbound interface of the router corresponding to the destination address, it will forward the message through the corresponding interface. If If the destination address is the router itself, the message will be handed over to the upper layer for further processing. The routing and forwarding table in the router includes the corresponding relationship information between the network address and the interface. The routing and forwarding table can be generated for user configuration or automatically learned by the router. . In combination with the above-mentioned existing technical conditions, the specific implementation of the method for preventing network attacks described in the present invention is as follows, see figure 1 :
[0024] Step 1: The router receives an IP message, which carries information su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com