Methods and arrangements in a telecommunications system
A communication system and equipment technology, applied in transmission systems, digital transmission systems, wireless communications, etc., can solve problems such as data virus damage, damage to host operating systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
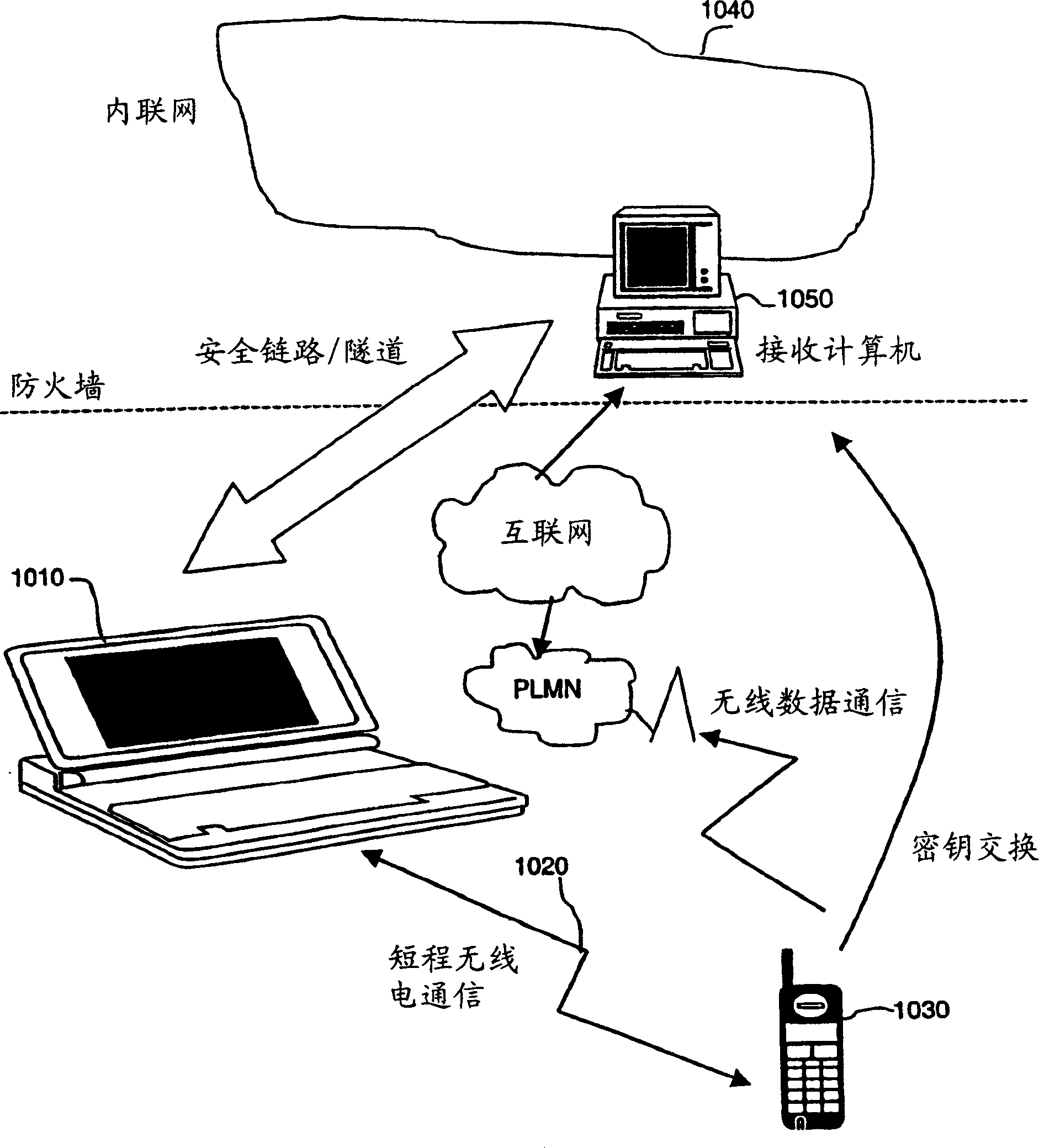
[0049] figure 1 The use of the method and apparatus according to the invention is described. Mr Smith is visiting Tokyo as an employee of an international company such as Ericsson. Mr. Smith owns a mobile phone 1030 with a SIM card installed with secure firmware according to the invention. Mr. Smith wishes to communicate with the Intranet 1040 of Ericsson Corporation located in Stockholm, Sweden. Mr. Smith borrows a laptop computer 1010 from the hotel where he is staying while visiting Tokyo. He uses short-range radio communication 1020 to connect the laptop 1010 to his mobile phone. In other applications, cables can be used instead of short-range radio communications. In another embodiment of the present invention, laptop 1010 may be replaced by a stand-alone computer. Infrared light can be utilized to provide communication between the laptop 1010 and the mobile phone 1030 . In another embodiment, a SIM card with security firmware installed may be inserted into the lap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com