Secure data transmission links
A technology of secure communication and prime numbers, applied in the field of data communication links of secure links, can solve the problem of not providing non-rejection or anonymous software downloads, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
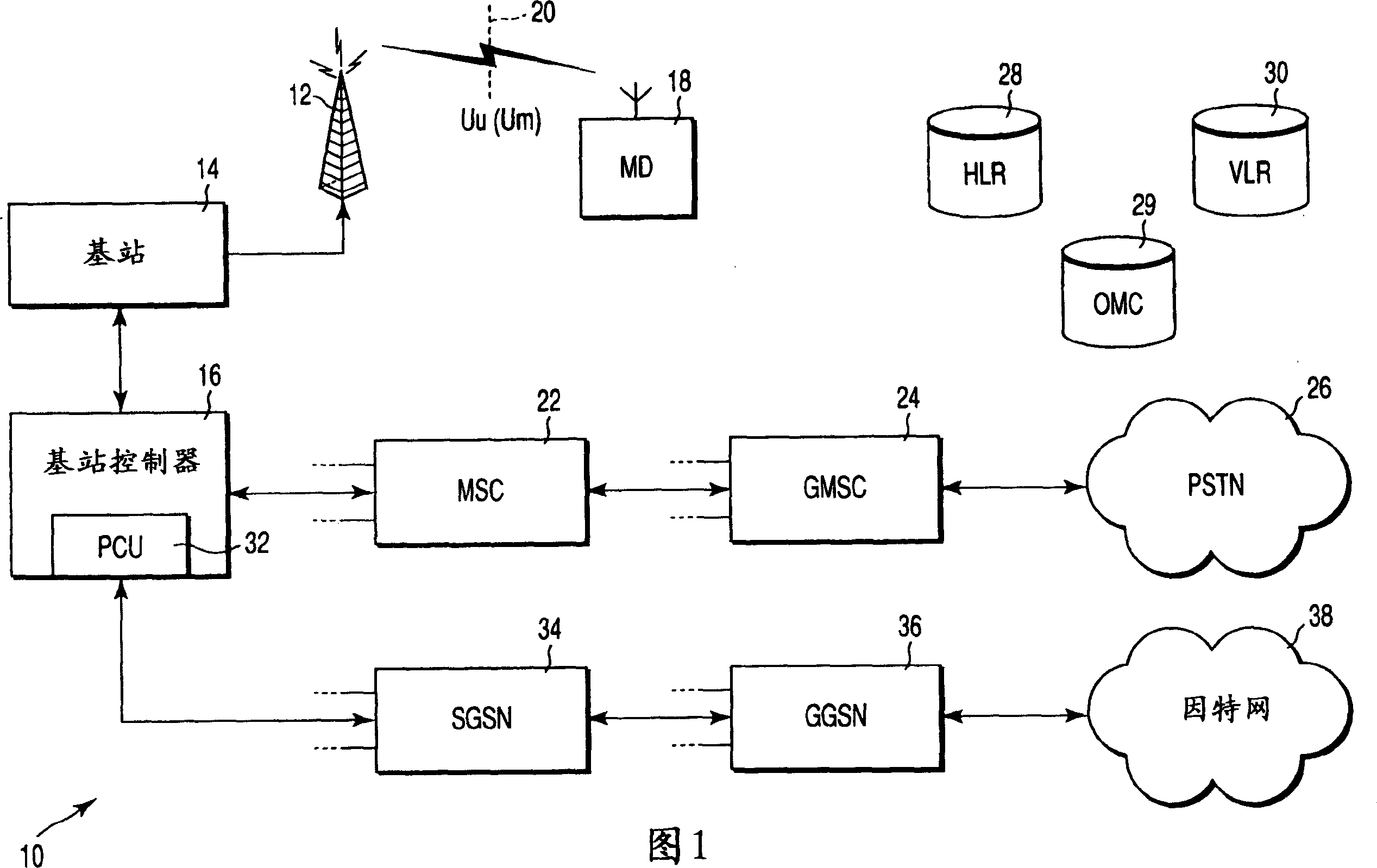
[0026] FIG. 1 shows at 10 the general structure of the third generation digital mobile telephone system. In FIG. 1 , a radio mast 12 is connected to a base station 14 , which in turn is controlled by a base station controller 16 . The mobile communication device 18 shown communicates bidirectionally with the base station 14 via a radio or air interface 20, which is the Um interface in GSM (Global System for Mobile Communications) networks and GPRS (General Packet Radio Service) networks, and in CDMA2000 and W -Un interface in CDMA network. Generally, at any one time multiple mobile devices 18 are associated with a given base station that includes multiple radio transceivers to serve these devices.
[0027] Base station controller 16 is coupled to a mobile switching center (MSC) 22 along with a number of other base station controllers (not shown). A plurality of such MSCs are coupled to a gateway MSC (GMSC) 24 which connects the mobile telephone network with a public switched...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com