Identification method for user apparatus
A user equipment and technology to be authenticated, applied in the field of network communication, can solve problems such as authentication cannot be completed, achieve the effect of convenient network operation and management, lower requirements, and protect existing investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
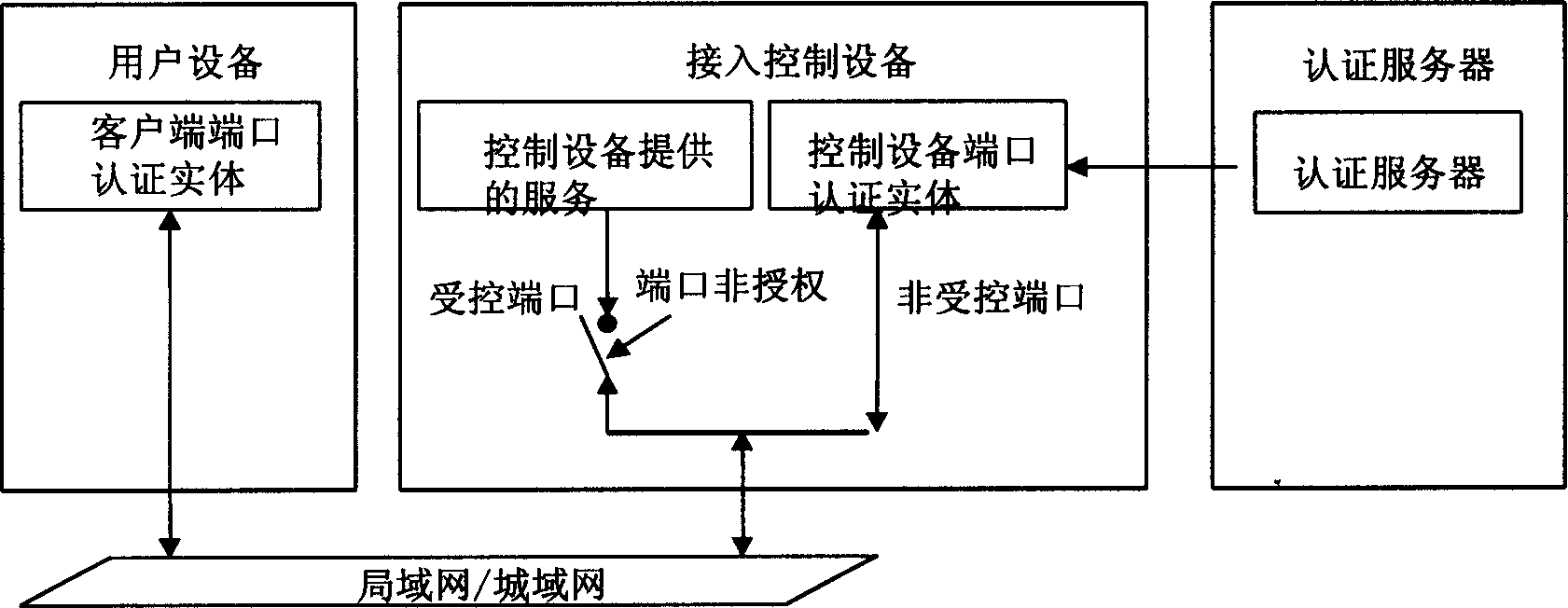
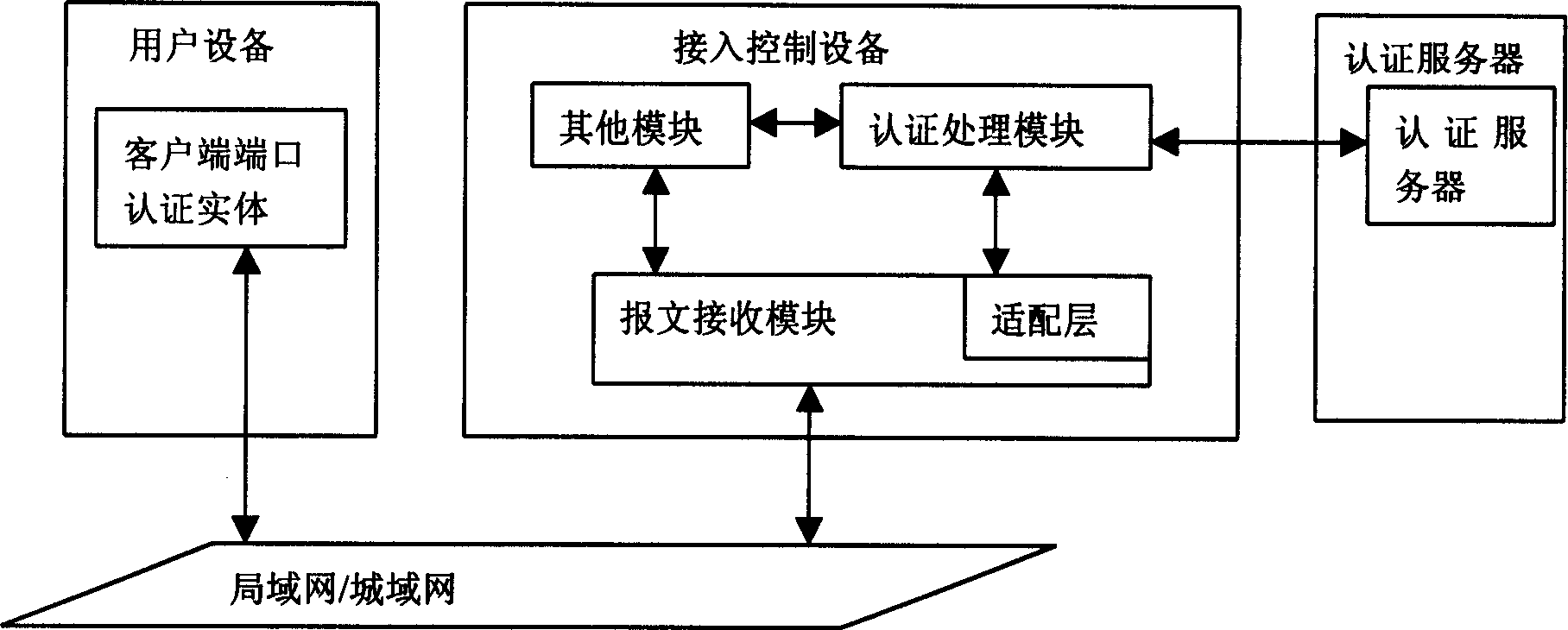
[0018] The present invention proposes a method for authenticating user equipment, and its authentication structural block diagram is as follows image 3 As shown, the authentication structural block diagram includes three parts: user equipment, access control equipment, and authentication server. The method for authenticating user equipment includes the following steps:
[0019] (1) First, the user equipment to be authenticated initiates an authentication message with a destination address of "FF-FF-FF-FF-FF-FF" to the access control device;
[0020] (2) After the message receiving module in the access control device receives the above-mentioned authentication message, the adaptation layer in the message receiving module sends the destination address "FF-FF-FF-FF-FF-FF" in the message to " into "01-80-C2-00-00-03";
[0021] (3) The message receiving module sends the authentication message whose destination address is "01-80-C2-00-00-03" to the authentication processing module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com