Network protective method based on multiple volume preset protective ring
A network protection and protection circle technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problem of resource redundancy and achieve the effect of improving the utilization rate of network resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
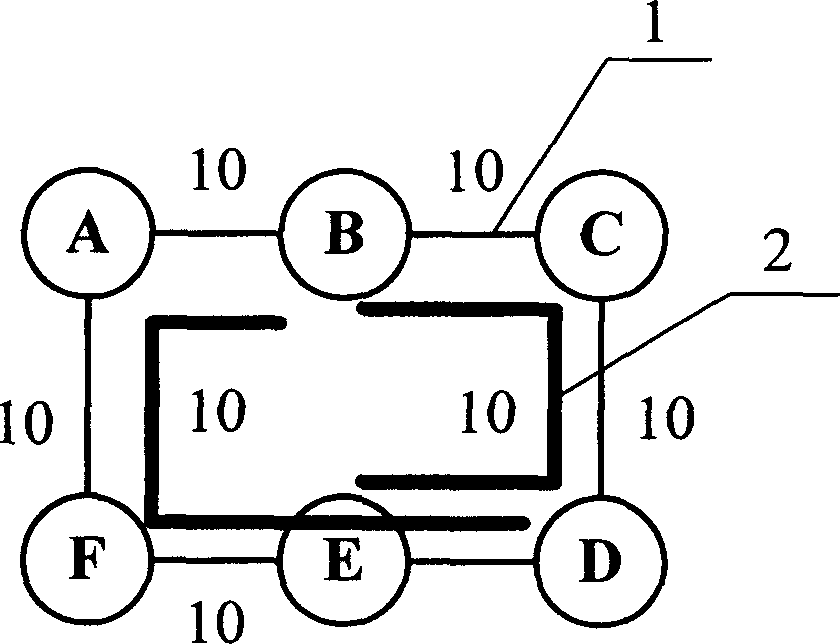
[0038] Below, a six-node ring network is used as an example to compare the difference between the preset protection circle of the present invention and the traditional preset protection circle, as figure 1 shown. figure 1 Middle 1 is the circle link of the preset protection circle; figure 1 Middle 2 is work business. Suppose there are two services in the ring network, one is B-A-F-E-D and the other is B-C-D-E, and the bandwidth of both services is 10.
[0039] The preset protection circle in the traditional preset protection circle method is A-B-C-D-E-F-A. The backup resources of all links on the preset protection circle are the same, 20.
[0040] exist figure 1 In , if the recovery path adopts B-C-D when the service flow B-A-F-E-D fails, it means that the link k (ie B-C or C-D) in circle j is used to protect the failed link i (ie B-A, or A-F, or F-E, or E-D), that is, when k is B-C or C-D, δ i,j,k r is 1, and is 0 when k is other sides. Similarly, if the service flow ...
example 2
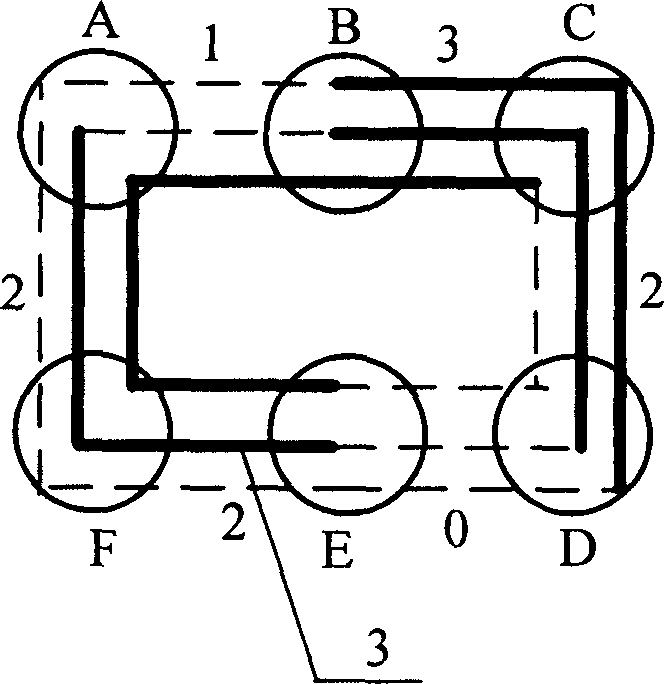
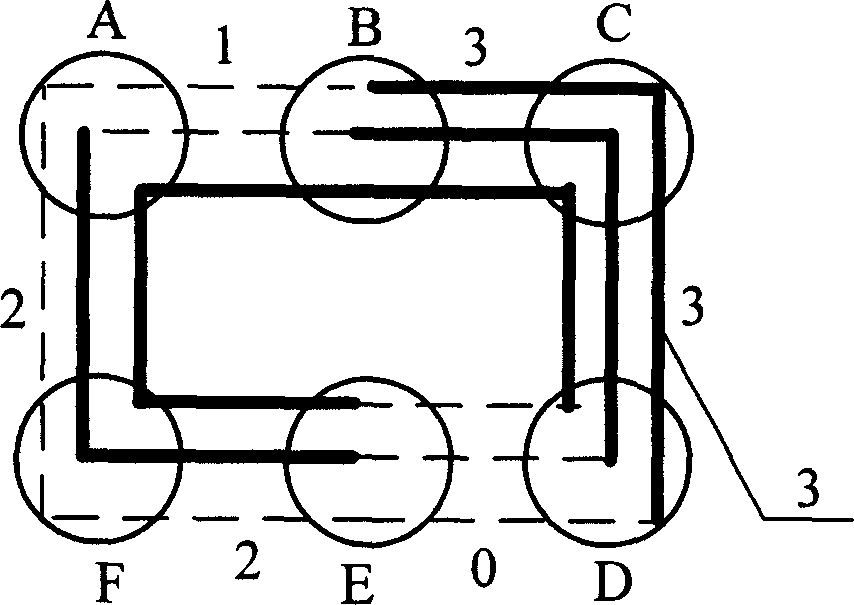
[0042] Assume that the backup resource capacity of each circle link in the preset protection circle has been obtained by the linear programming method, such as figure 2 shown. figure 2 3 in is the preset protection path in the preset protection circle. exist figure 2In , circle link D-E is a virtual link, while circle link A-B is a link with the minimum capacity. In order to ensure the preset characteristics of the preset protection circle, the backup resource capacity on the circle link needs to be adjusted using a correction algorithm. That is, all circle links between the preset protection circle segments A-F-E are configured with a backup resource capacity of 2 units, and all circle links between the preset protection circle segments B-C-D are configured with a backup resource capacity of 3 units. The backup resource configuration of the finally obtained multi-capacity preset protection ring is as follows: image 3 As shown, compared with the traditional network pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com