WEB identification method
An authentication method and authentication request technology, applied in the field of WEB authentication, can solve the problems of user worry, low security, and impact on billing accuracy, and achieve the effect of increasing security and improving billing accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
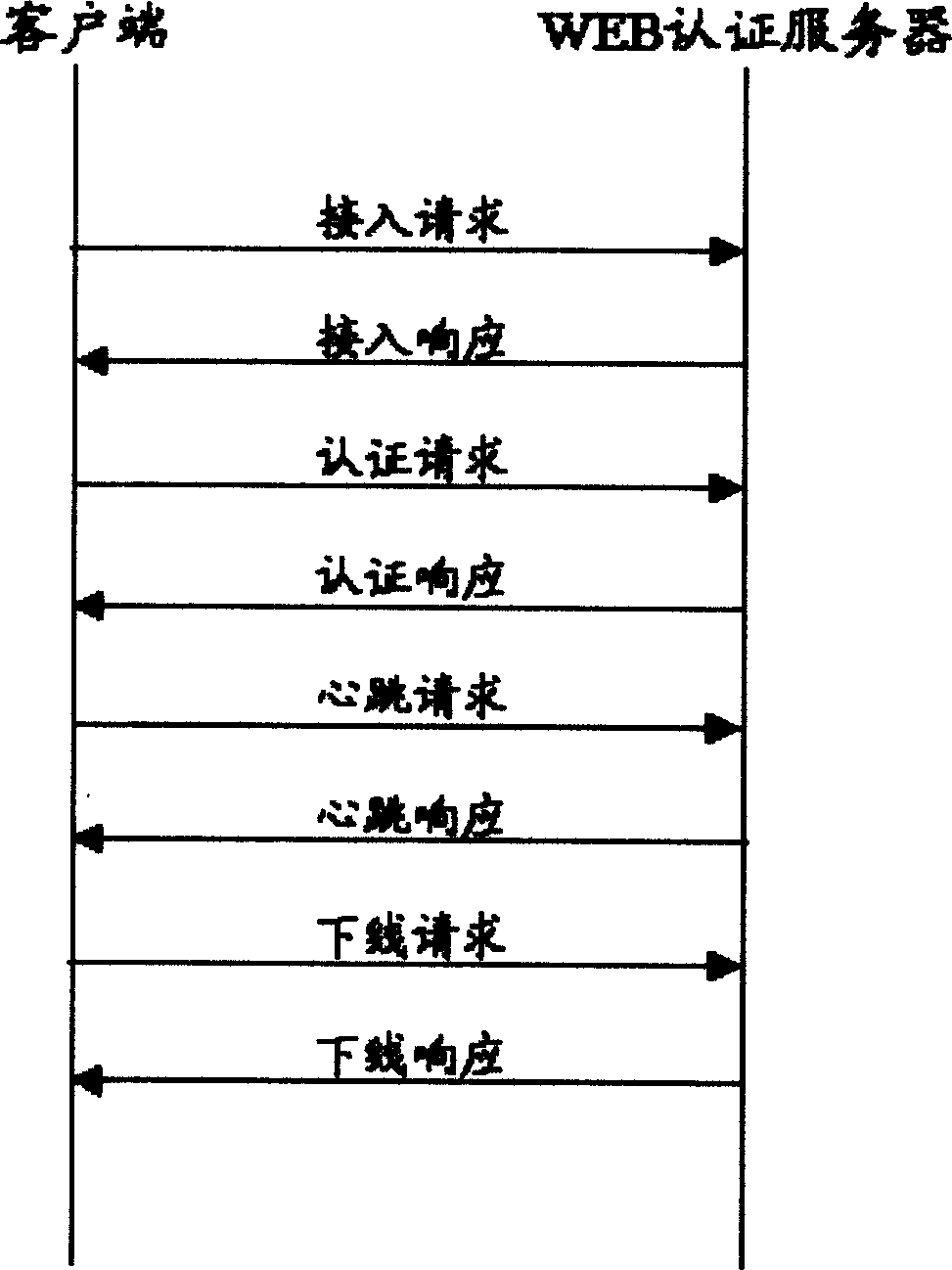
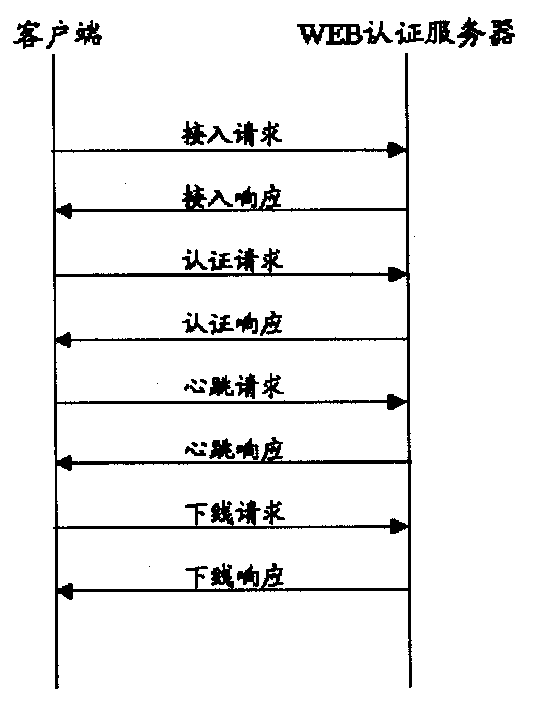
[0023] see figure 1 , the WEB authentication method of the present invention, it is based on HTTP agreement, and it comprises the following steps:
[0024] a. The user downloads the webpage from the WEB authentication server through the browser, enters the user name and password, clicks the online button, the client program runs, and sends an access request to the WEB authentication server, wherein the client uses JavaScript or JavaApplet program.
[0025] b. The WEB authentication server assigns a key and online ID to the client, and notifies the client through an access response.
[0026] c. The client encrypts the user name and password with the key, and sends an authentication request to the WEB authentication server.
[0027] d. The WEB authentication server processes the authentication request. If the authentication fails, the client will be notified of the failure with the authentication response; otherwise, the client will be notified of the successful online authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com