Hierarchical cooperated network virus and malice code recognition method
A technology of malicious code and identification method, applied in the field of computer network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] 1. Use several general-purpose micro-personal computers to connect to a network environment through switches
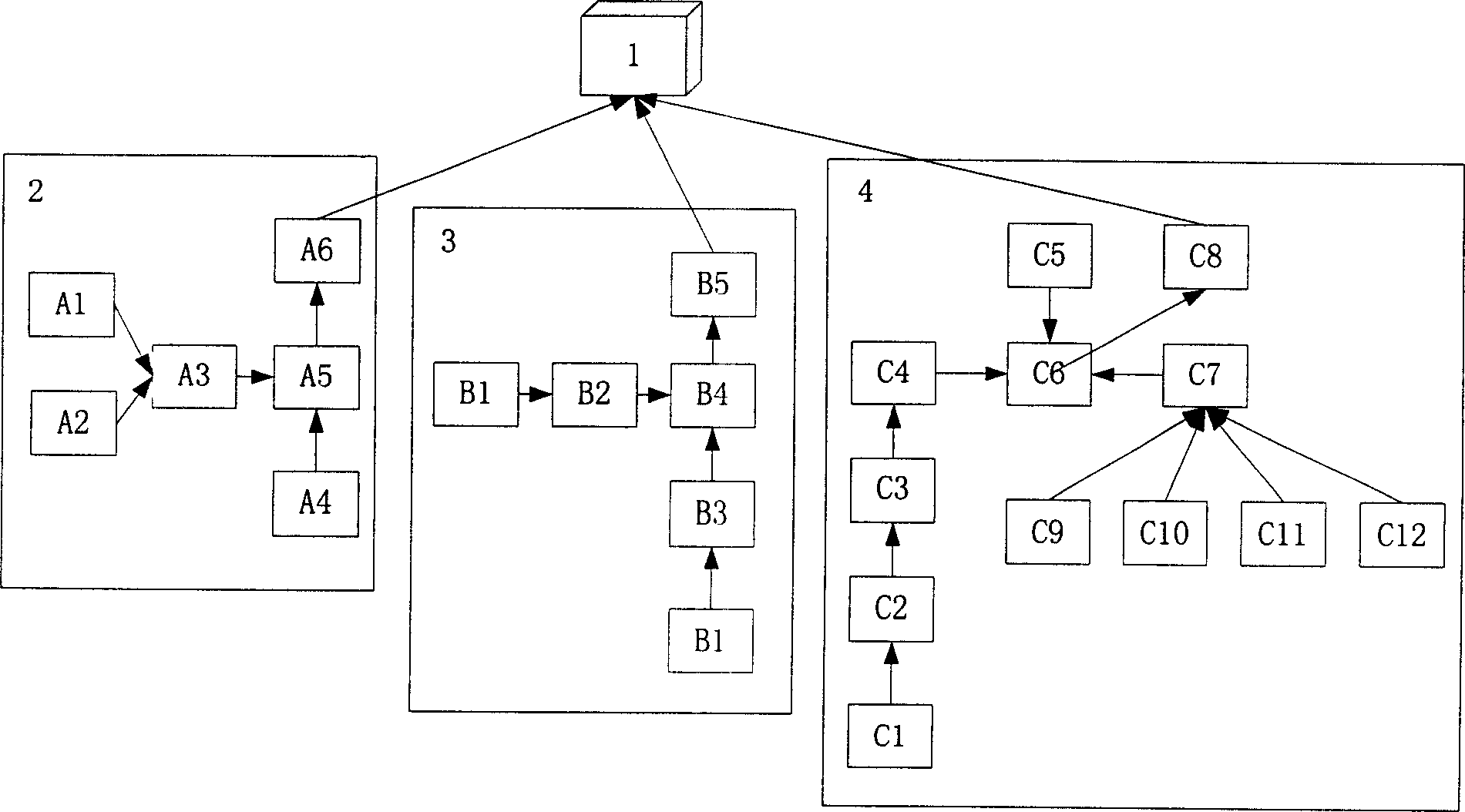
[0053] Specifically adopted in this embodiment are three Pentium IV microcomputers, and a Dell notebook, and an enterprise server, plus a Great Wall 24-port 10M / 100M adaptive Ethernet switch GES-1125 switchboard, through which several microcomputers Three Pentium IV microcomputers, a Dell notebook and an enterprise server are connected into a network.
[0054] figure 1 The workflow for identifying network viruses and malicious codes for layered collaboration in this embodiment is given. The direction of the arrow indicates the sequence of the work flow, the tail of the arrow is the input of the next step, and the end of the arrow is the operation of the next step. One of the Pentium series microcomputers is used to run the network console 1, and the remaining two Pentium IV microcomputers, a Dell notebook, and an enterprise server are all used to execute the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com