Device, method, and program for encryption and decryption and recording medium
An encryption method and technology of an encryption device, which are applied to encryption devices with shift registers/memory, secure communication devices, synchronous transmission/reception encryption devices, etc., can solve problems such as difficult video data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The best way to implement the invention
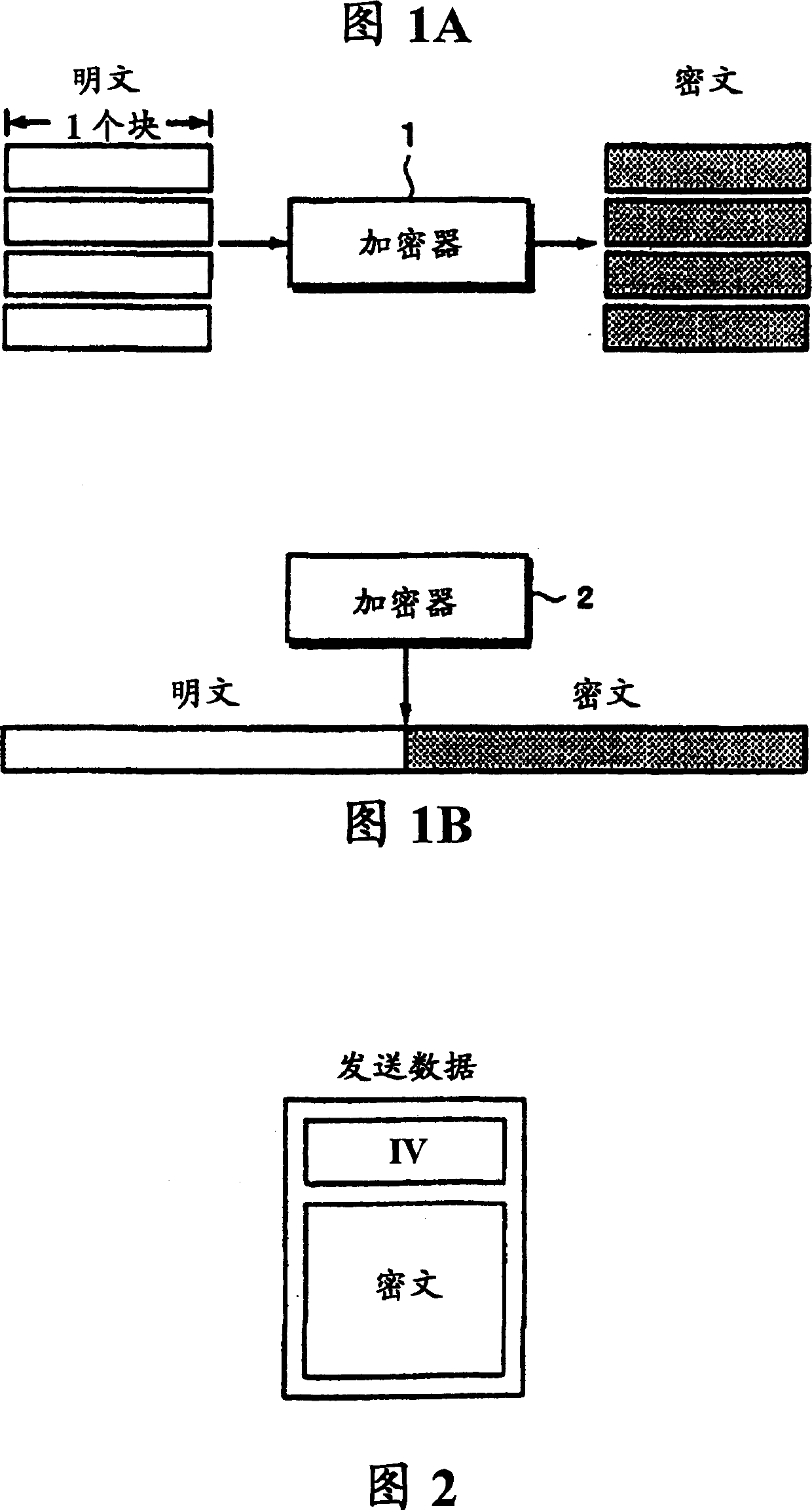
[0041] Fig. 3 schematically shows the encryption device of the present invention. Reference numeral 11a denotes an "exclusive OR" gate (hereinafter, abbreviated as EX-OR gate) for inputting an IV having the same bit length as the encryption key of the stream cipher extracted from the encrypted file. Enter the common key 12a for the EX-OR gate 11a. The common key 12a is a secret key shared by the transmitting side and the receiving side.
[0042] How to extract the IV from the ciphertext can be decided in advance on the sending side and the receiving side. For example, when encrypting video data, it may be determined in advance from a designated position within one frame, for example, from the top of the effective video data of one frame to use the designated number of bits as the IV. In this case, the time interval is the frame period.
[0043] The encryption key 13a is obtained from the output of the EX-OR gate 11a, and the data to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com