Network encryption system based on picture keyboard and operating method thereof
An operation method and encryption system technology, which is applied in the direction of user identity/authority verification, etc., can solve the problems of inability to protect user names, passwords, low efficiency of user names and passwords, and are not generally accepted by people, so as to overcome easy theft and deciphering , reduce the burden, improve the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
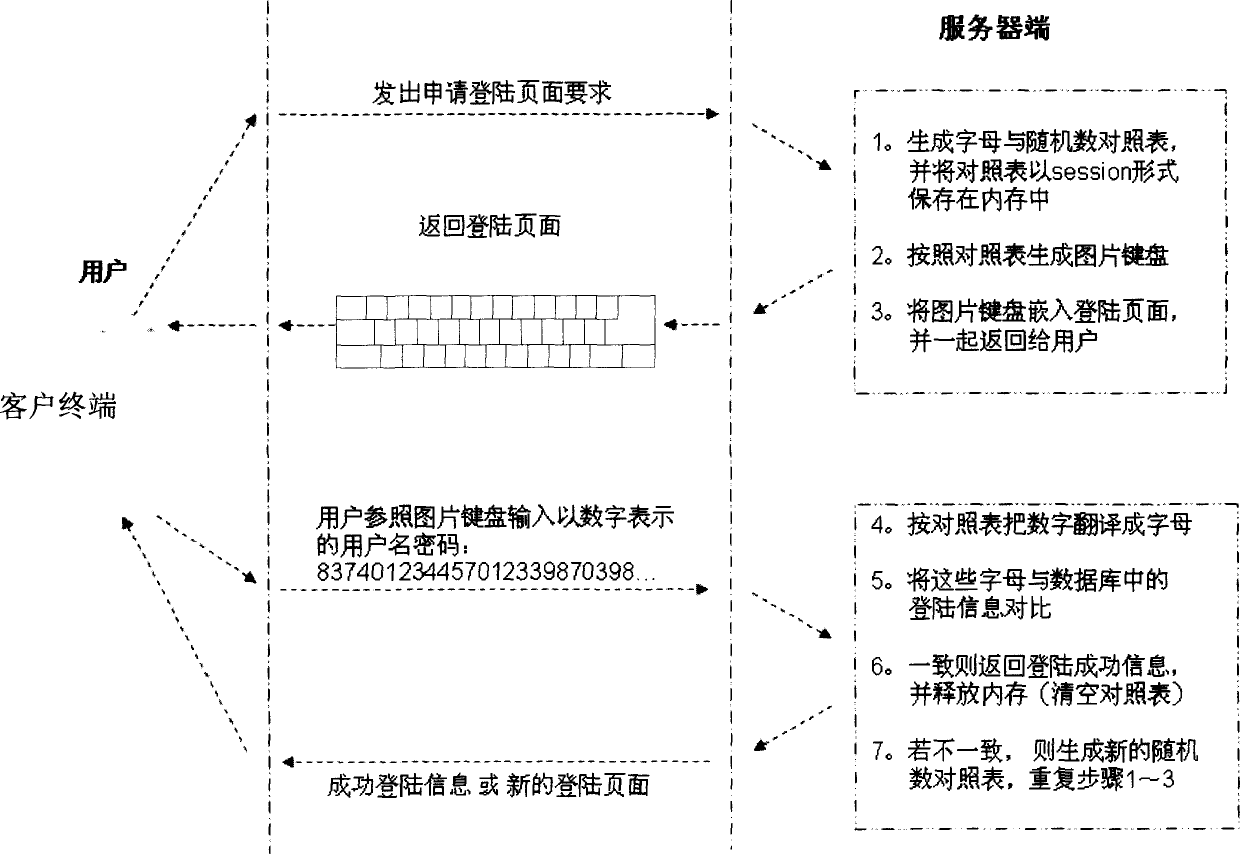
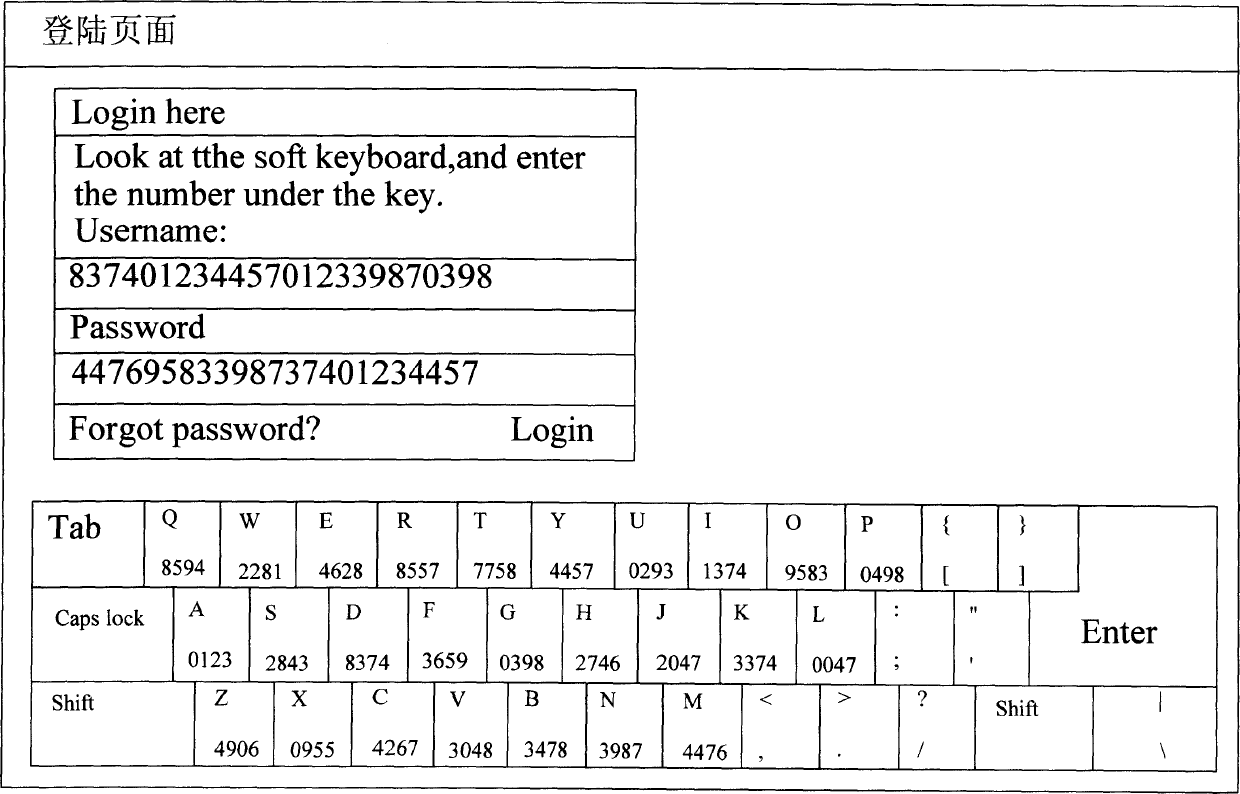
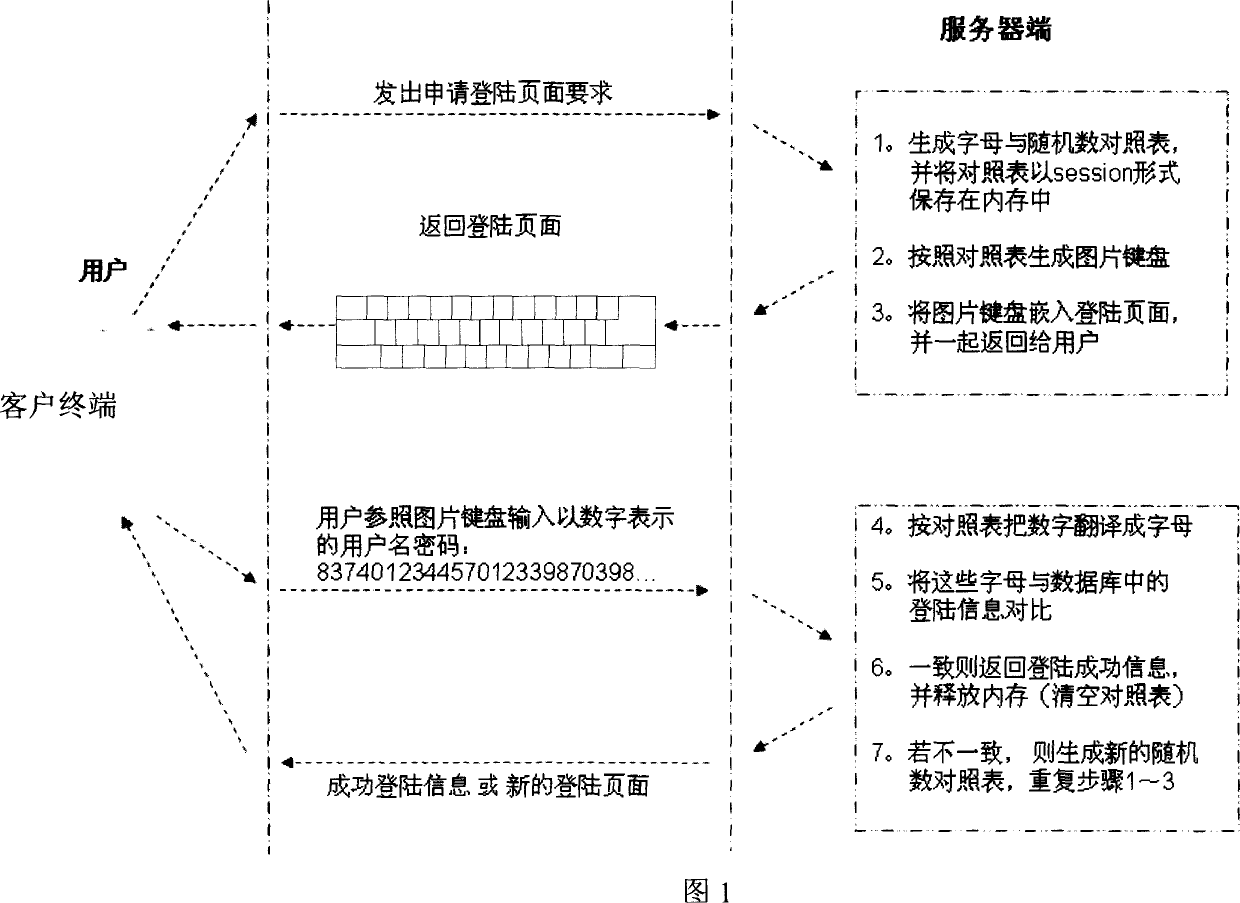
[0023] The network encryption system based on the picture keyboard of the present invention, in terms of physical structure, includes a network interconnected server and a client terminal, and the client terminal is at least provided with a display, a keyboard, a central processing unit, and a memory module. Usually, the system of the present invention can be realized based on the existing Internet, and the client terminal is a personal computer. The processor of the client terminal is a central processing module that can execute registration and login procedures. Its function is to send a request for registration or login page to the server through the network, display the registration or login page on the monitor, and convert the registration or login page to the server. The verification information is sent to the server; and the above-mentioned registration or login page requires the user to input registration or login verification information including user name and passwor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com