Method for implementing black sheet
A blacklist and purpose technology, applied in the field of port-based blacklist implementation, to achieve the effect of enhancing flexibility and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Preferred embodiments of the present invention are described in detail below.
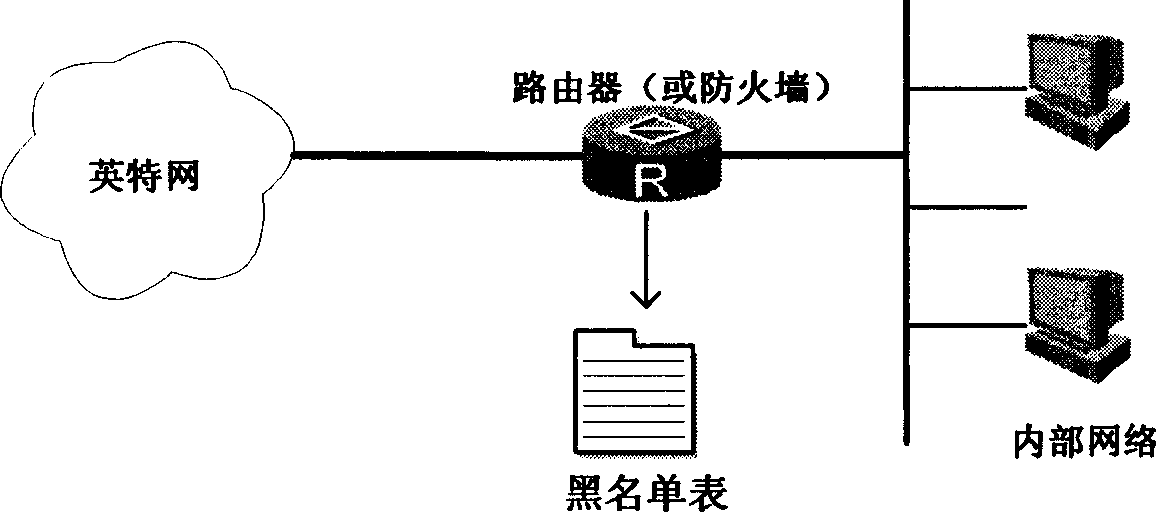
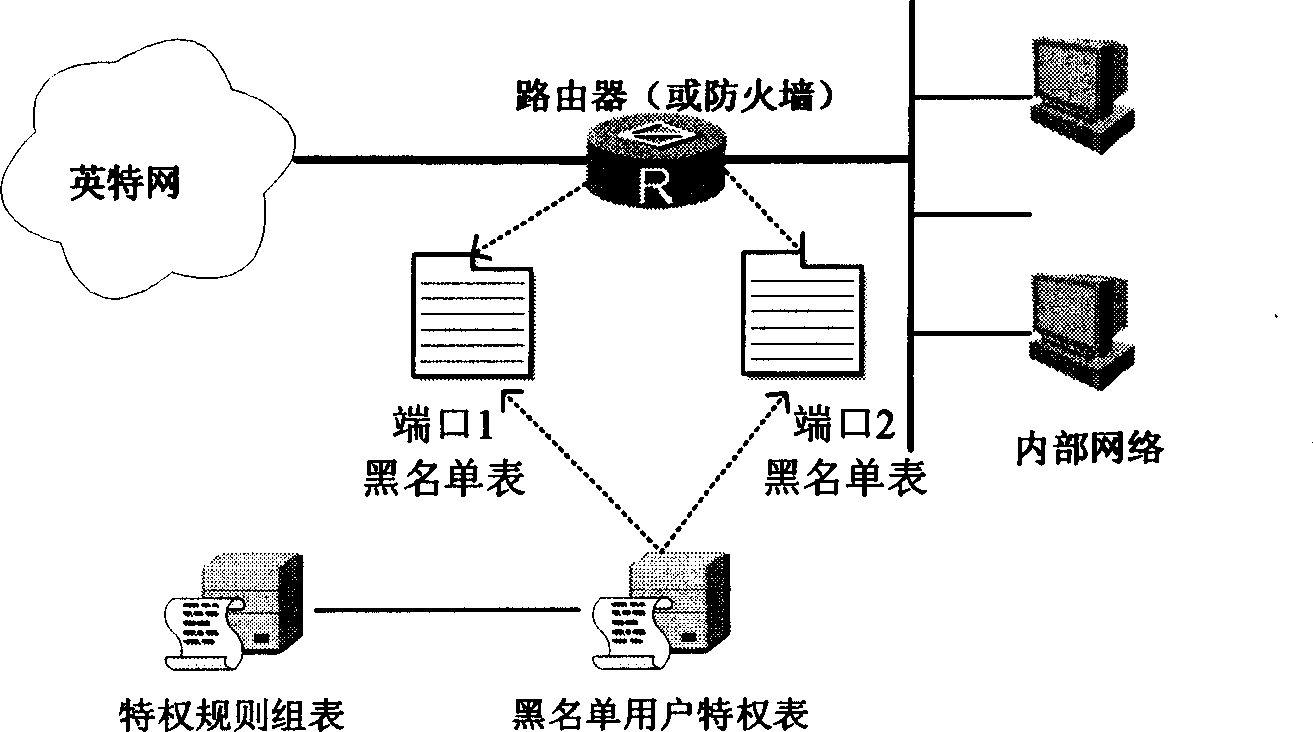
[0028] as attached figure 2 As shown, the present invention provides a port-level blacklist implementation technology, so that the addition of the dynamic blacklist takes the port as the unit, and the port is the scope of the blacklist, which can avoid the blacklist scope caused by address spoofing or other attacks. Expansion, affecting the use of normal users.
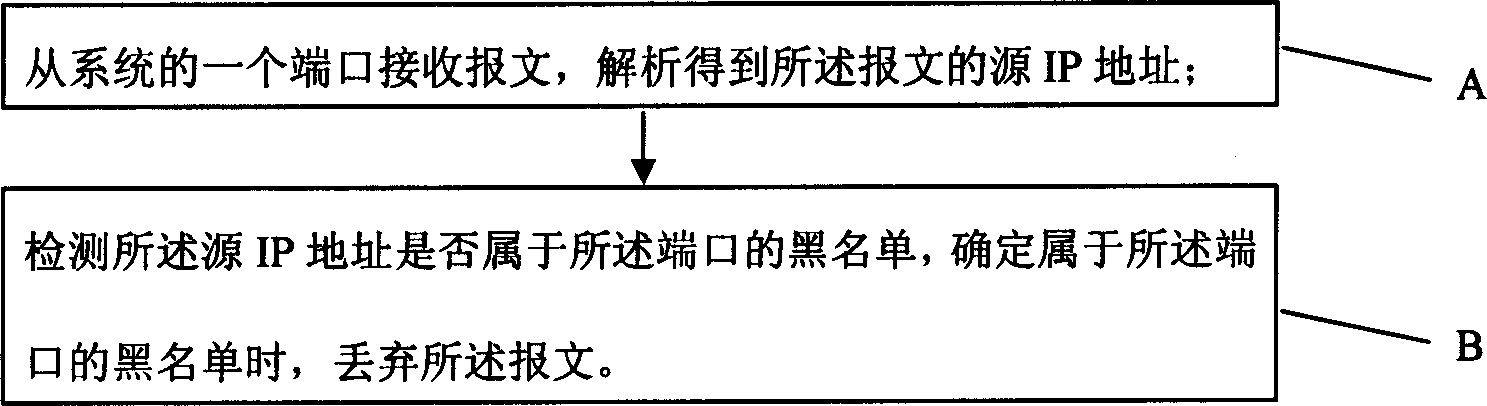
[0029] as attached image 3 As shown, the present invention provides a method for implementing a blacklist, which includes the steps of: A, receiving a message from a port of the system, parsing and obtaining the source IP address of the message; B, detecting whether the source IP address belongs to The blacklist of the port. When it is determined that the port belongs to the blacklist of the port, the message is discarded.
[0030] Blacklist can have multiple establishment methods, for example, also includes step before describ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com