Web page wooden horse detecting method based on behavior characteristic
A technology of web page Trojan horse and detection method, applied in the field of computer security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
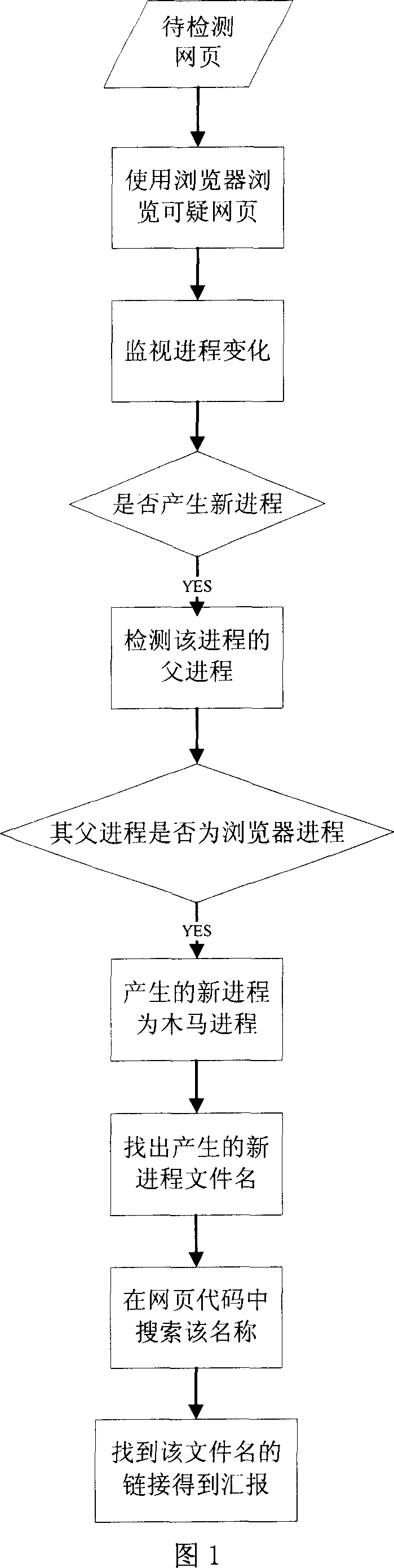
[0023] The overall process of the web page Trojan detection method based on behavioral features proposed by the present invention is shown in FIG. 1 . Firstly, a browser program needs to be used to browse the webpage to be detected, that is, the browser program is used to run the code of the webpage to be detected. A Trojan horse program is also a kind of virus, so a Trojan horse program must also be a program that can run, and the Trojan horse program hidden in the web page code can only be activated and run after the web page is run with a browser. Only when the Trojan horse program hidden in the web page code is run, can the process change be observed by the process monitoring program.
[0024] After using the browser program to open the webpage to be detected, immediately run the process monitoring program to monitor the changes of the process, and observe whether there is a new process in the process list. Whether there is a new process can be notified by passing a messa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com