Distributed access control method in multistage securities
A secure access control and distributed technology, applied in the field of network security, can solve the problems that have not found the same or similar literature reports
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
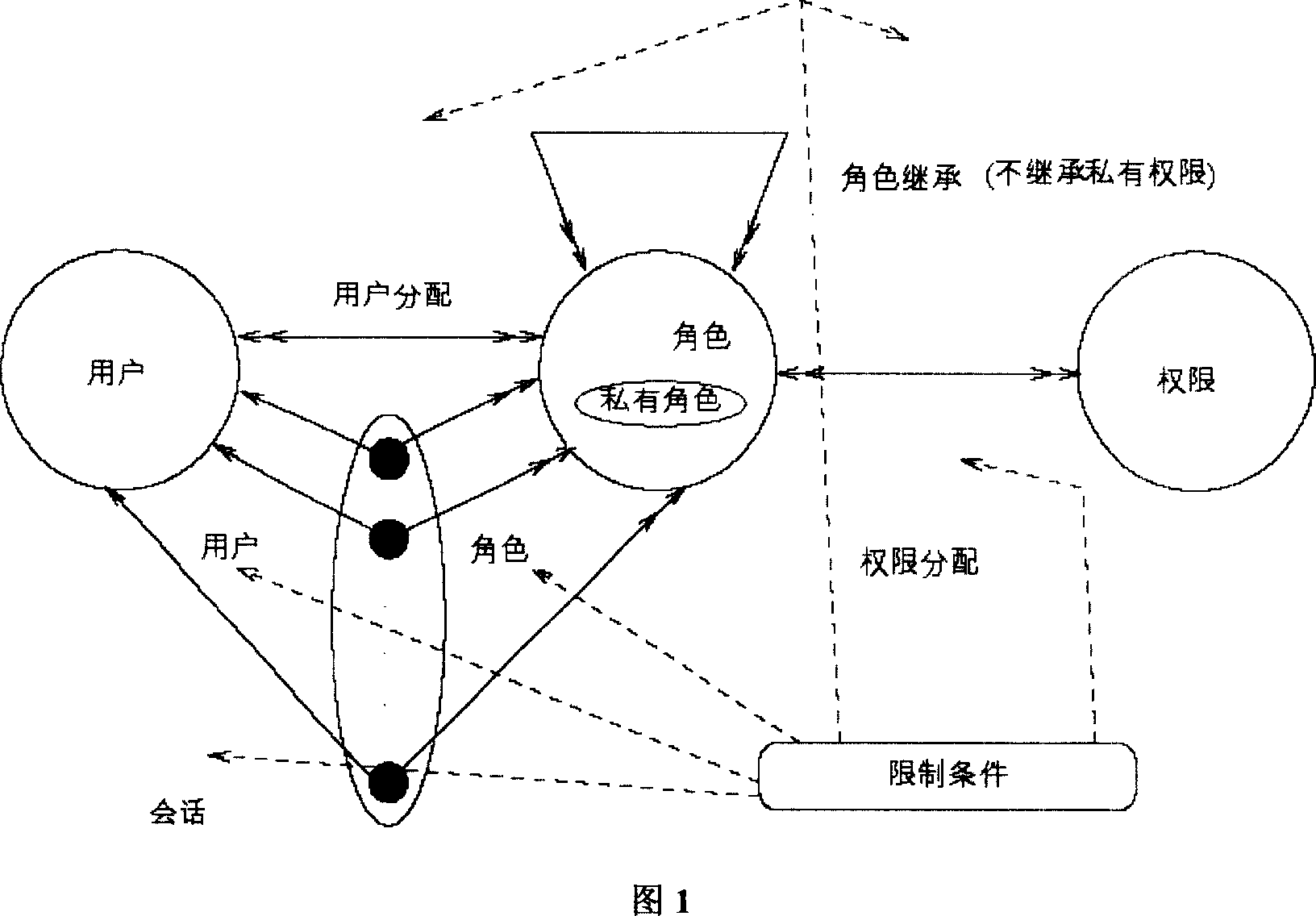
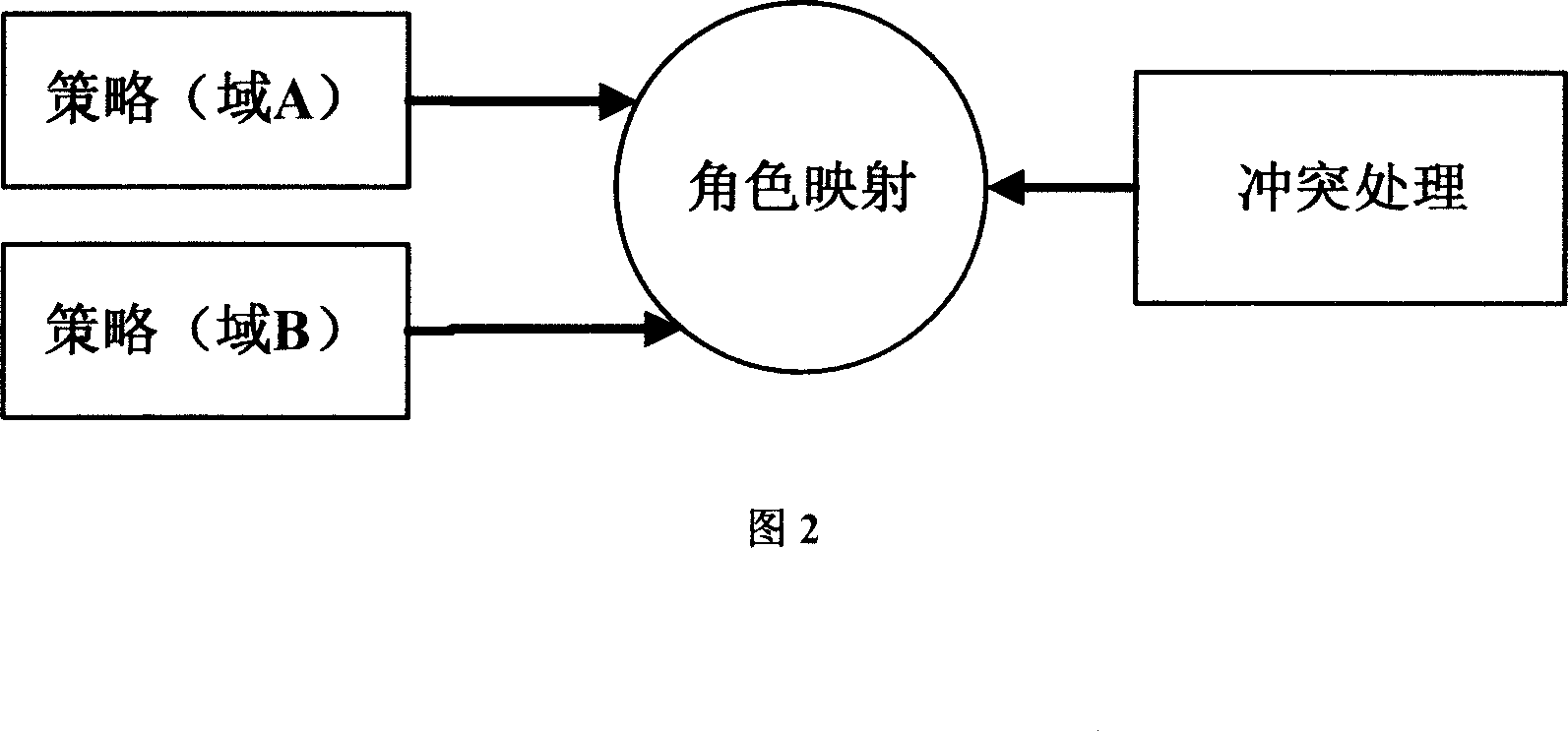
Image
Examples
Embodiment Construction
[0023] The software and hardware environment that present embodiment implements adopting: server: more than Tomcat 5.0, JAVA environment, support JAAS, client hardware requirement: Windows 2000 / XP, above Pentium 2400Mhz, 256M internal memory, connect with the network of server; Client software: IE browser.
[0024] deploy:
[0025] ①. Build the identity authentication server of this trust domain in each trust domain, deploy it on Tomcat, and deploy an LDAP server in each trust domain, including the following databases:
[0026] a. User identity information database (PKI certificate information table, etc.)
[0027] b. Attribute certificate database (PMI certificate information table, intra-domain policy mapping table, inter-domain policy mapping table, role certificate table, role mapping table, etc.)
[0028] c. Resource information database (configurable resource information and corresponding permissions provided in this trust domain)
[0029] ②. Configure the two-way aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com