A method and system to realize network shield in packet network
A packet network system and network shielding technology, applied in the field of communication, can solve the problems of network shielding limitation and low security of network shielding, and achieve the effect of improving security and operability, good security and strong adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
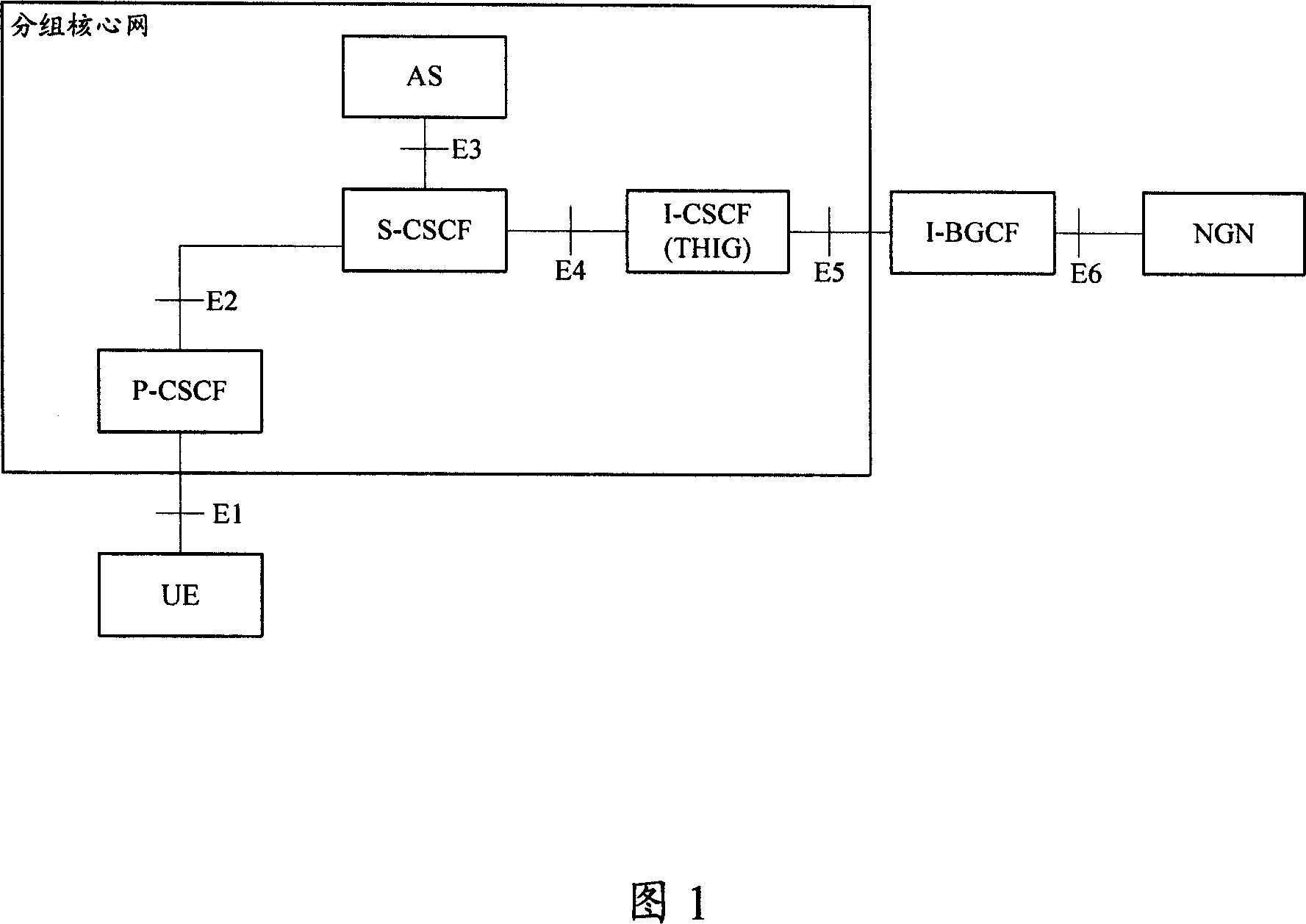
[0061] The network logic structure of the packet core network using SIP protocol as call control signaling is shown in Figure 1, where the packet core network can be either IMS or IMS-based PSTN / ISDN Emulation Subsystem (PES). Among them: interfaces E1-E6 are all SIP protocol interfaces, and each functional entity is only functionally independent, and can be combined in one physical entity arbitrarily, and the interface between the combined functional entities can be an internal interface; the application server (AS ) may be a third party or a special AS with security requirements. In an IMS-based PES network, the Access Gateway Control Function (AGCF) is also one of the network access points; in addition, when interworking with other heterogeneous IP networks, the Interworking Border Gateway Control Function (I-BGCF) is also a network shielding point one.
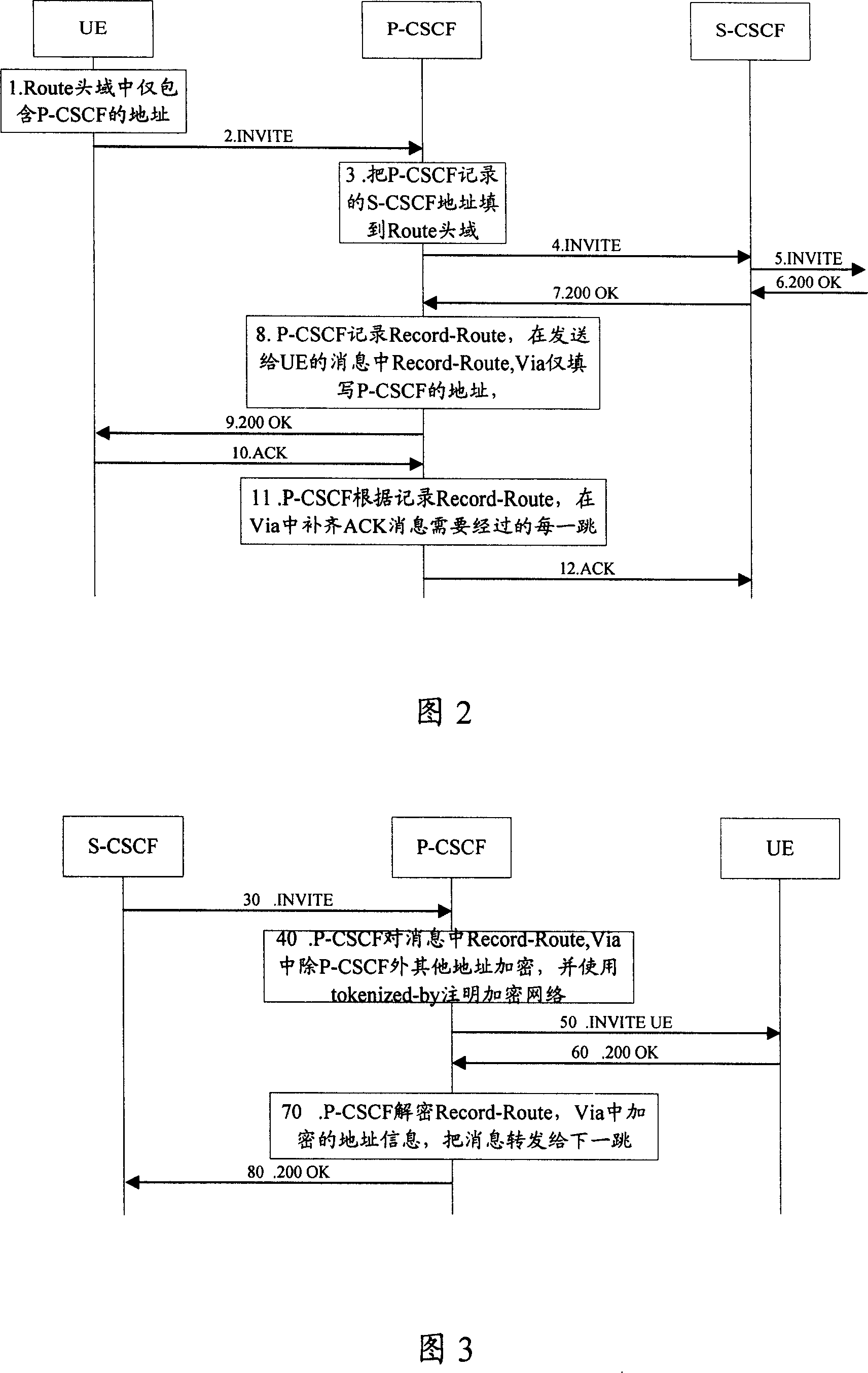
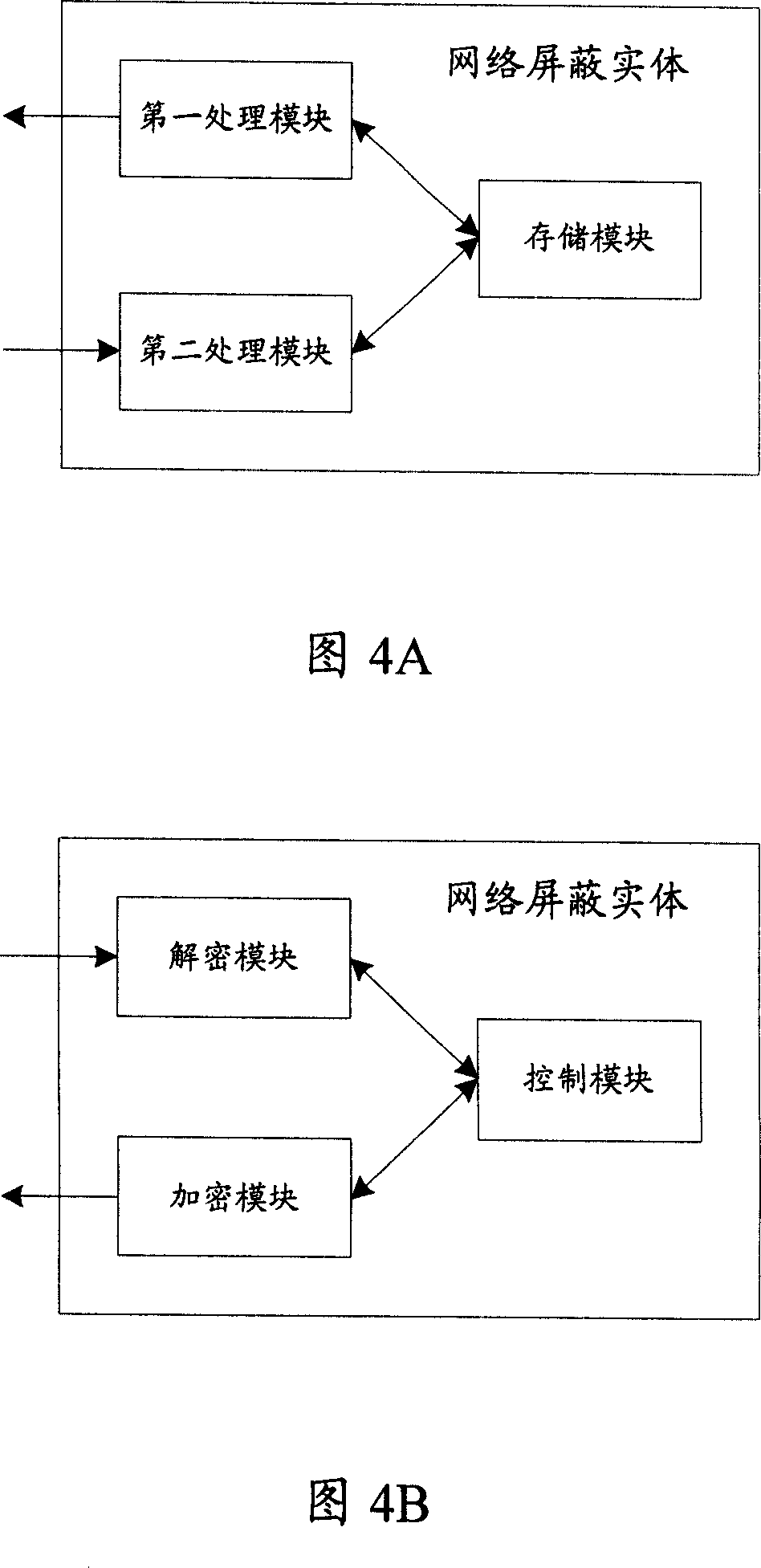
[0062] In order to improve security in the process of network shielding in the packet network, the present invention se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com