Method for automatic identifying and configurating terminal
An automatic identification and terminal technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve problems such as increasing the complexity of business acceptance and increasing the complexity of factory production, achieving low cost, flexible use, and simple configuration. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
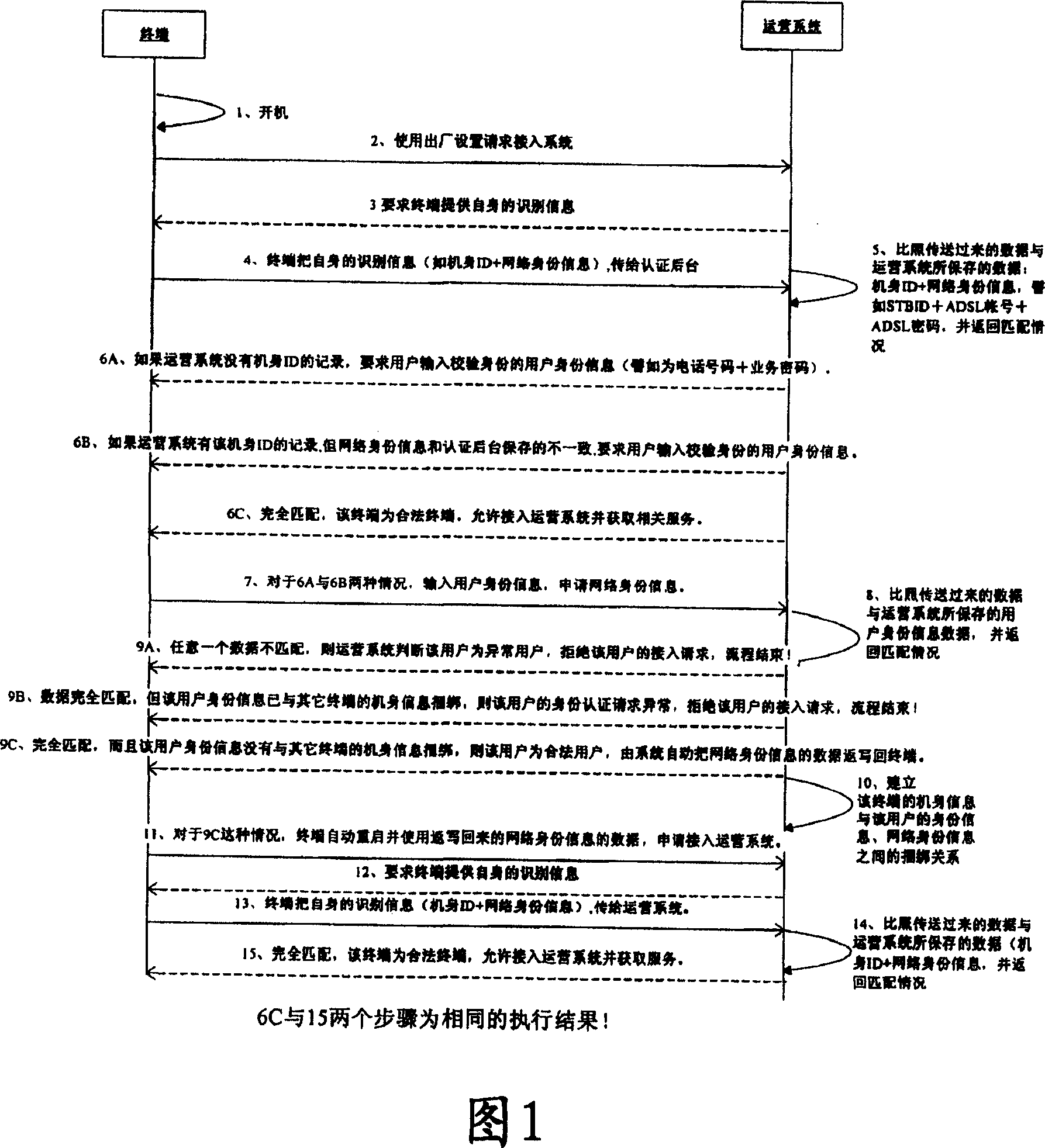
[0039] With reference to FIG. 1 , the flow of a method for automatically identifying and configuring a terminal according to the present invention is described in detail.
[0040] After a certain terminal is turned on (step 1), use the factory settings to request access to the operating system (step 2).
[0041] Step 3, the operating system receives the request from the terminal, and then requires the terminal to provide its own identification information.
[0042] Step 4, the terminal transmits its own identification information, including, for example, the body ID+network identity information, to the operation system. The network identity information is, for example, an ADSL account+ADSL password.
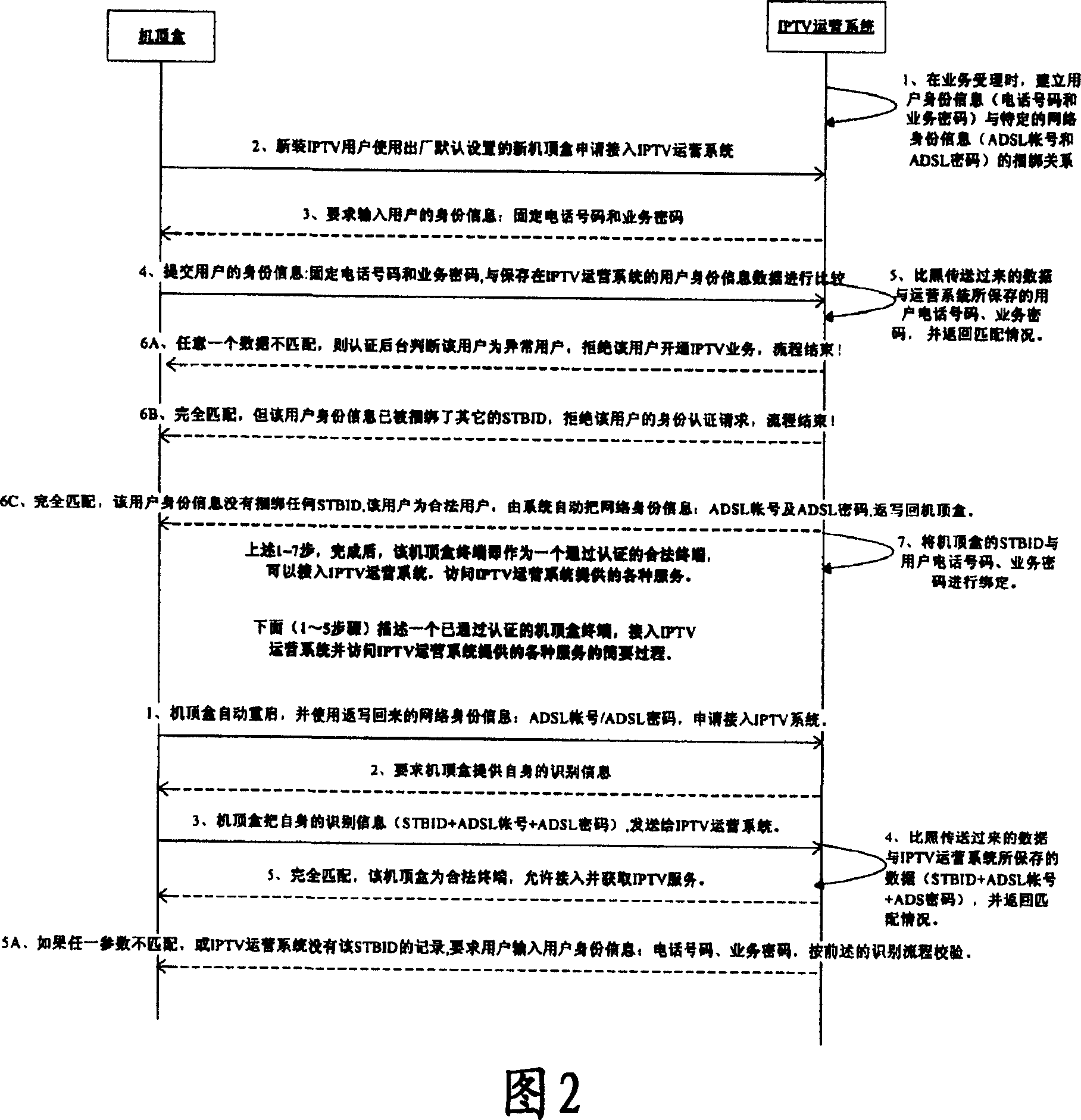
[0043] Wherein, if the terminal has not learned its network identity information, the terminal will send its body information and a default network identity information data. The default data is uniformly configured at the factory to represent the default network identity infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com