Variable size key cipher and method and device using the same
a key cipher and variable size technology, applied in the field of compression and cryptography, can solve the problems of difficult design of a secure model and key control for the wnc encryption scheme, and the security issues of the wnc schem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
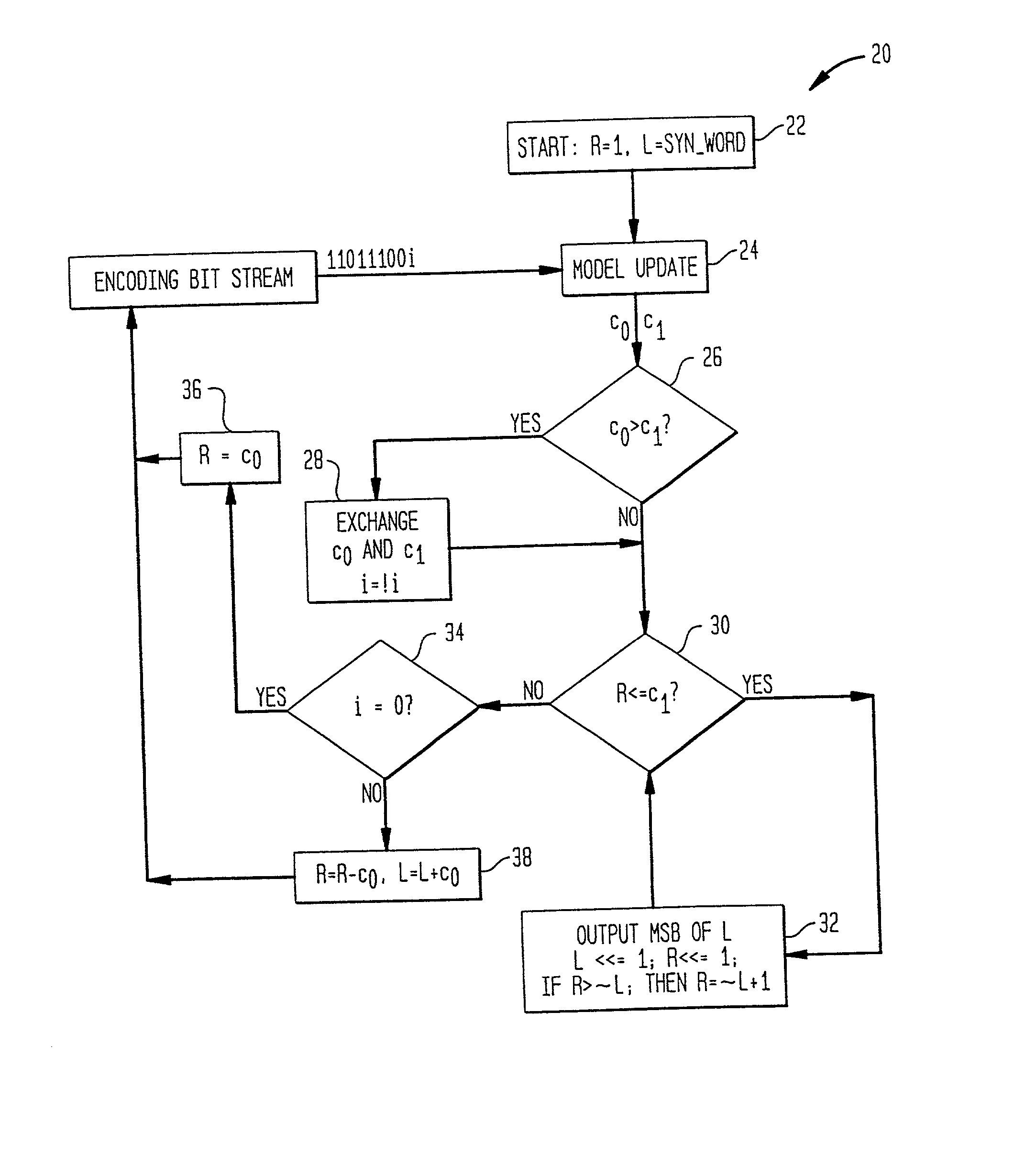
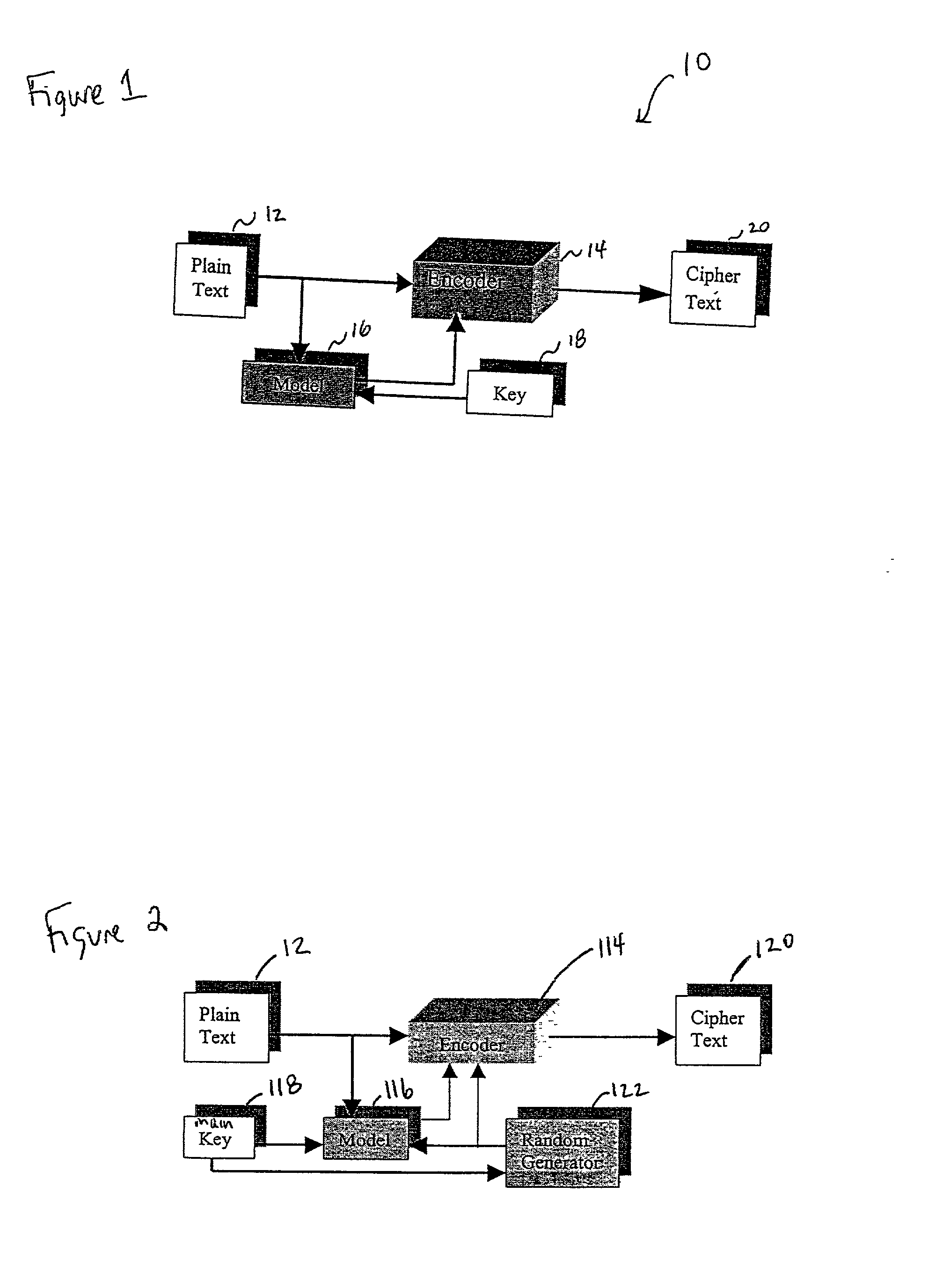
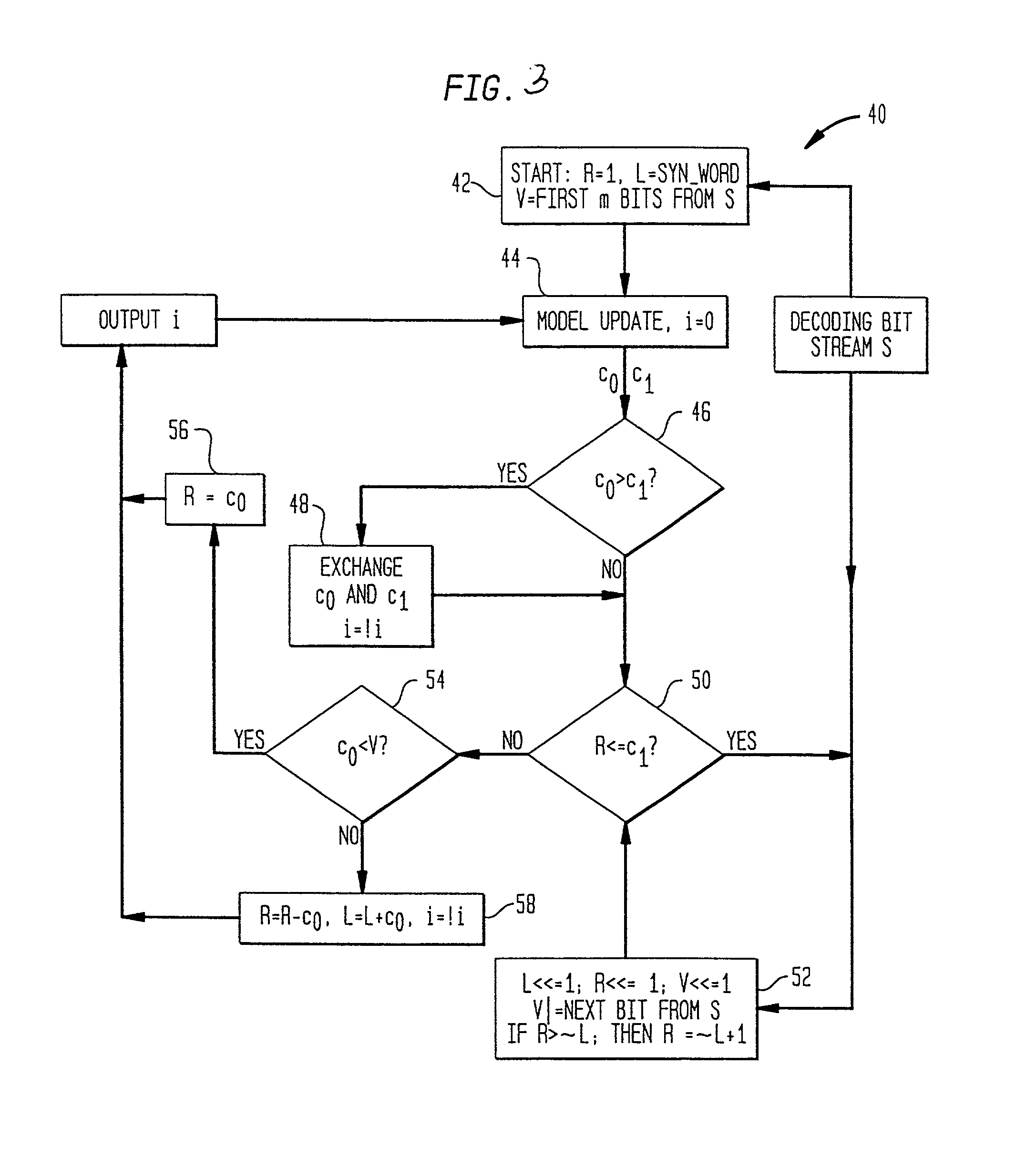
Image
Examples
Embodiment Construction
[0078] The parameters used for testing in this example are as follows:
[0079] L--Low end of the encoding interval: 32 bits, initially 0
[0080] H--High end of the encoding interval: 32 bits, initially 1
[0081] R--Range of the encoding interval: 32 bits, initially 1
[0082] V--Register for decoding bit stream
[0083] 2.sup.t--size of the frequency table 130: 64K for both 0 and 1, t=15
[0084] r--Address pointer register for table: 15 bits
3TABLE 2 Plain text "AAAAAAAAAAAAAAAAAAAAAAAA" Ex-peri-ments Keys Cipher Text (HEX) 1 A B9 50 C8 C9 1B F8 44 10 2 A FA A1 91 91 3C 81 14 80 3 A 83 D3 C3 C7 28 1F 35 4 AbCD8910 56 DF B4 56 894867 9E 82 28 28 28 66 45 21 40 5 AbCD8910 B9 72 D9 5D A0 F1 62 68 99 7D 7D 70 98 EE F8
[0085]
4TABLE 3 Plain text "It is incredible for us" Ex-peri-ments Keys Cipher Text (HEX) 1 Zfg E7 95 CE 8C A3 B7 7E 1D 98 9E 1E 6F 0D 77 32 14 C5 58 24 4b FF 40 69 43 1C 45 29 80 2 Zfg 2B CF 08 FD 5F 54 87 E1 D9 89 E1 E6 F0 D7 73 21 4C 55 82 44 BF F4 06 94 31 C4 52 98 3 123 C4 99 9E F4 97...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com