Apparatus, method and computer readable storage medium with recorded program for managing files with alteration preventing/detecting functions
a technology of computer readable storage and program, applied in the field of system for managing files, can solve the problems of difficult to modify the size of both a secure area and a normal area, and computerized data involves a risk of being altered by a third party
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
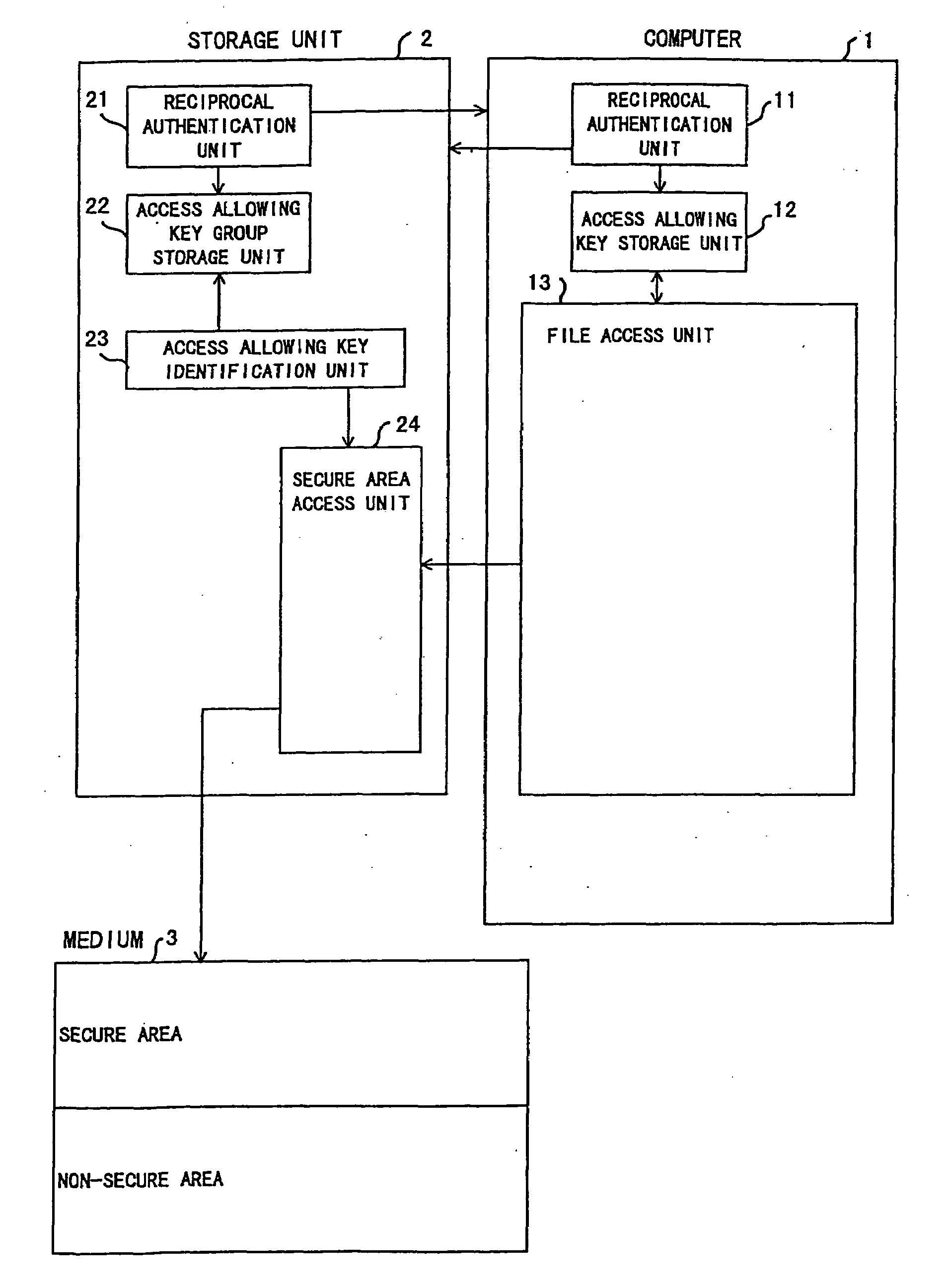
[0119]The reciprocal authentication described in this invention is carried out in advance.
[0120]In step S130 a medium ID reading unit 16 reads a medium ID 36 from the secure area 31 in the medium 3, and transfers the medium ID 36 to the authentication information creation unit 14.
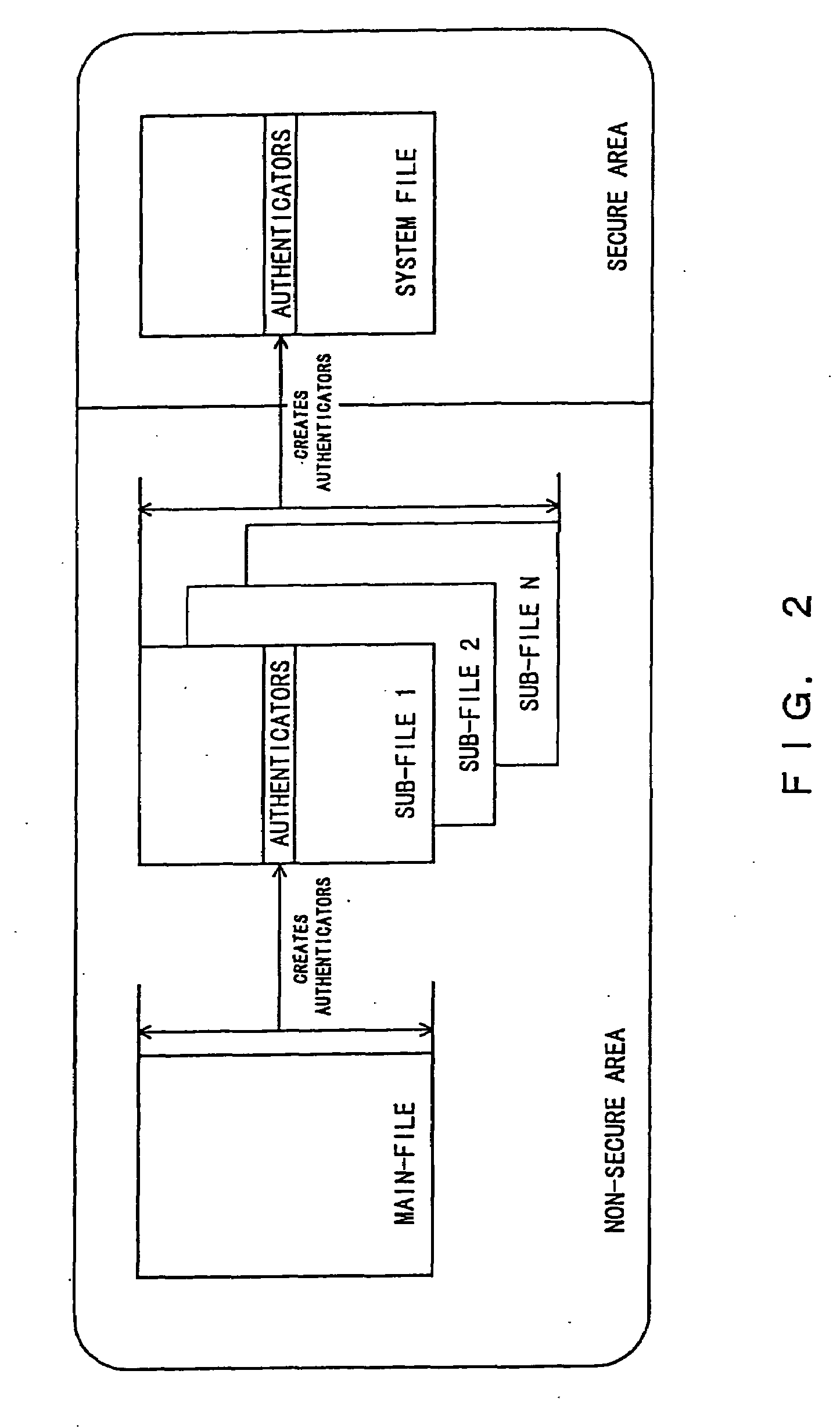
[0121]In step S131 the main-file storage unit 136 stores the main-file 33 in the medium 3 in units of blocks, and also transfers the main-file 33 to the authentication information creation unit 14.
[0122]In step S132, when receiving the main-file 33, the authentication information creation unit 14 creates an authenticator being authentication information from the main-file 33 using the medium ID 36 as a key, and transfers the authenticator to the sub-file storage unit 138. It is assumed here that the authenticator is created using a data encryption standard-message authentication code (DES-MAC).
[0123]In step S133 it is checked whether or not all the blocks of the main-file 33 are processed. If there is still...
sixth embodiment
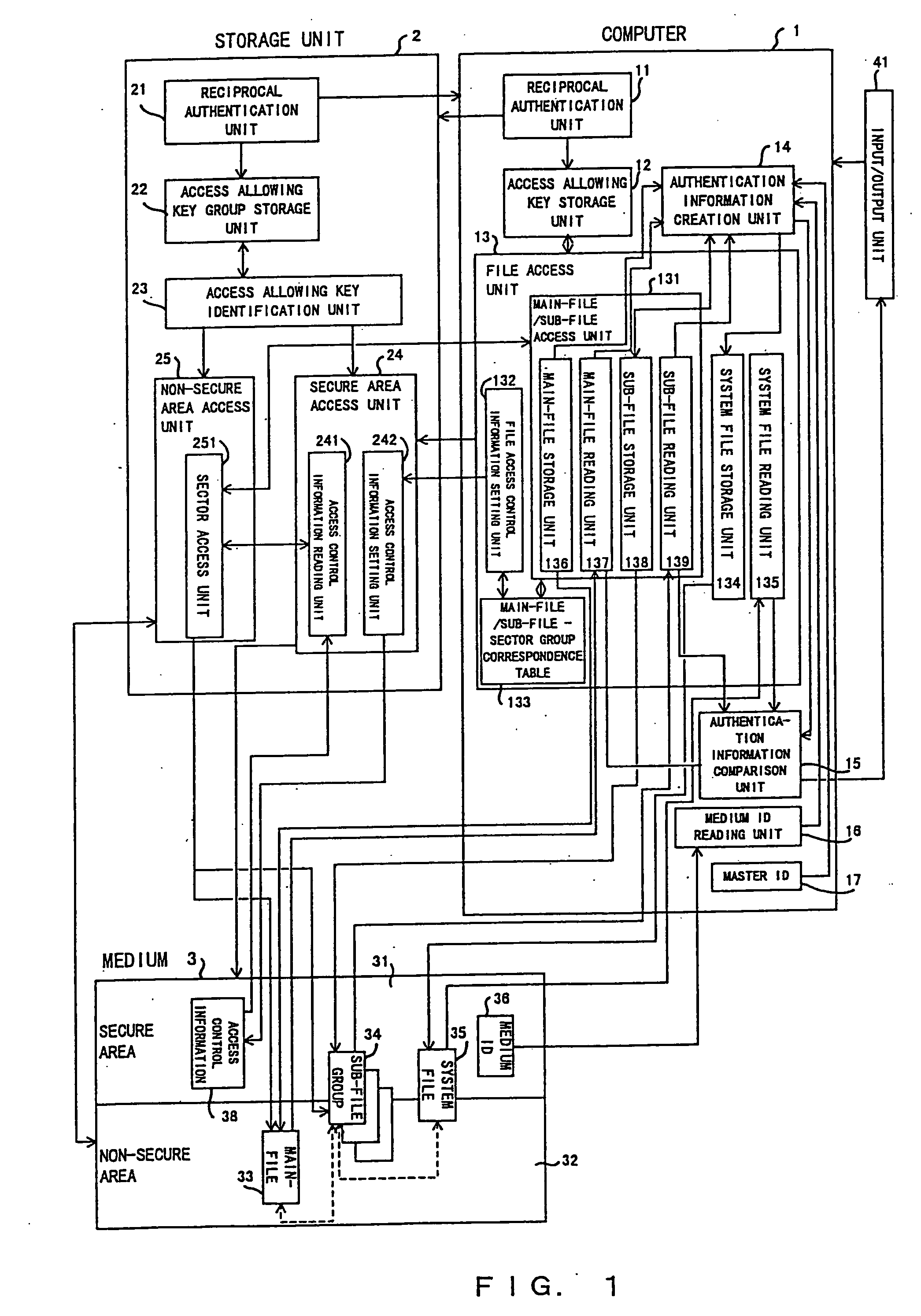
[0132]FIG. 14 shows the configuration of the file management system having the alteration preventing / detecting functions of this invention.
[0133]The configuration and basic operation of the sixth embodiment of this invention are the same as the configuration and basic operation of the fifth embodiment of this invention, except that the medium ID 36 read by the medium ID reading unit 16 in the fifth embodiment of this invention described with reference to FIG. 12, is replaced with a card ID 18 in the sixth embodiment of this invention.
seventh embodiment
[0134]FIG. 15 shows the configuration of the file management system having the alteration preventing / detecting functions of this invention.
[0135]The configuration and basic operation of the seventh embodiment of this invention are the same as the configuration and basic operation of the fifth embodiment of this invention, except that the medium ID 36 read by the medium ID reading unit 16 in the fifth embodiment of this invention described with reference to FIG. 12 is replaced with a master ID 17 in the seventh embodiment of this invention.
[0136]FIG. 16 shows the configuration of the file management system having the alteration preventing / detecting functions of the eighth embodiment of this invention. FIG. 17 is a flowchart showing the operation of the eighth embodiment of this invention.
[0137]In step S171, when a verification request is issued by a higher-order layer (a user, etc.) via input / output unit 41, the system file reading unit 135 reads an authenticator being corresponding ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com