Boot Validation in Imaging Devices
a technology of imaging device and boot validation, which is applied in the field of secure booting of computer systems, can solve the problems of limiting the overall security of the system, and the weakest link may be the vulnerability of embedded firmware to tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
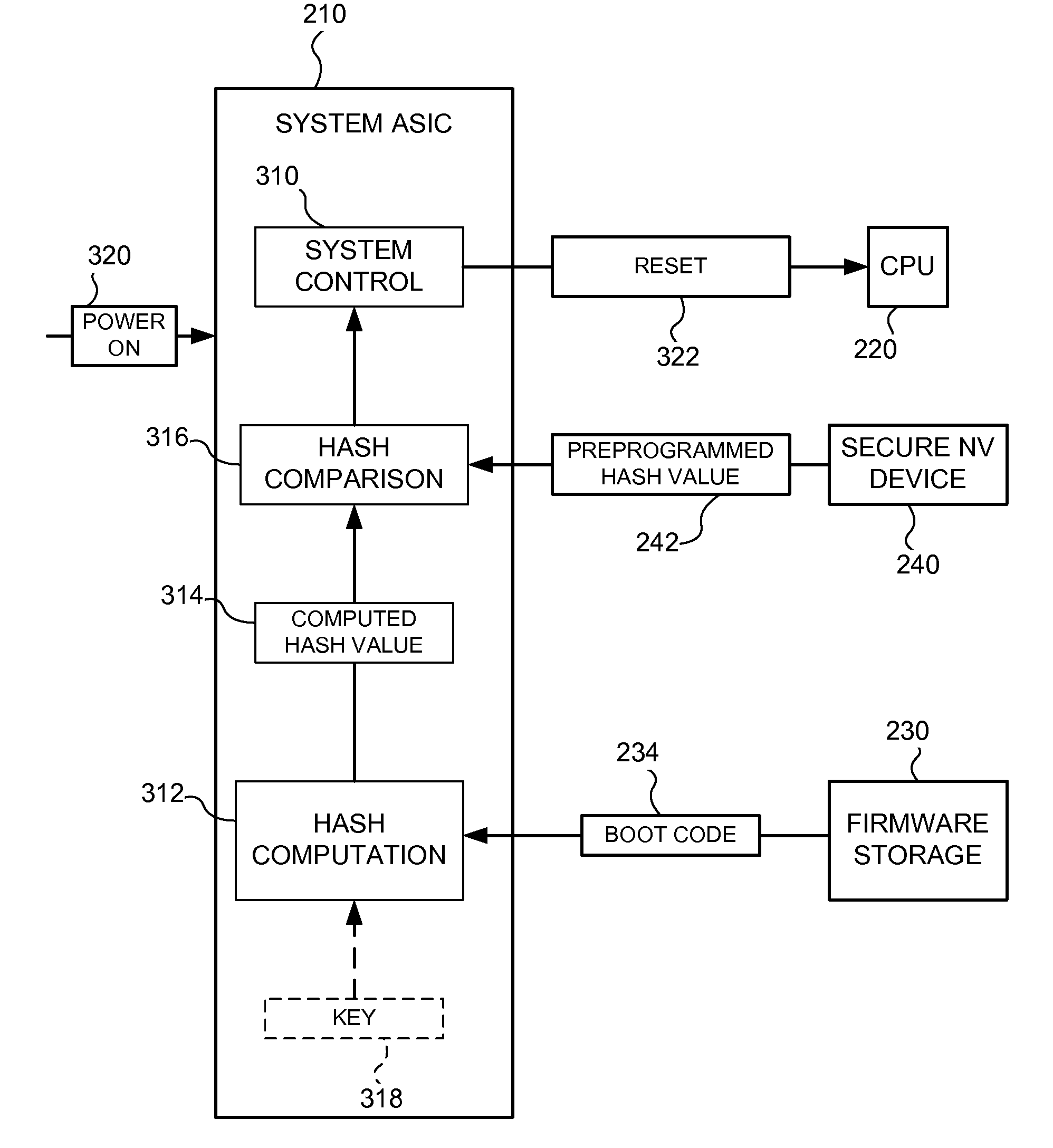
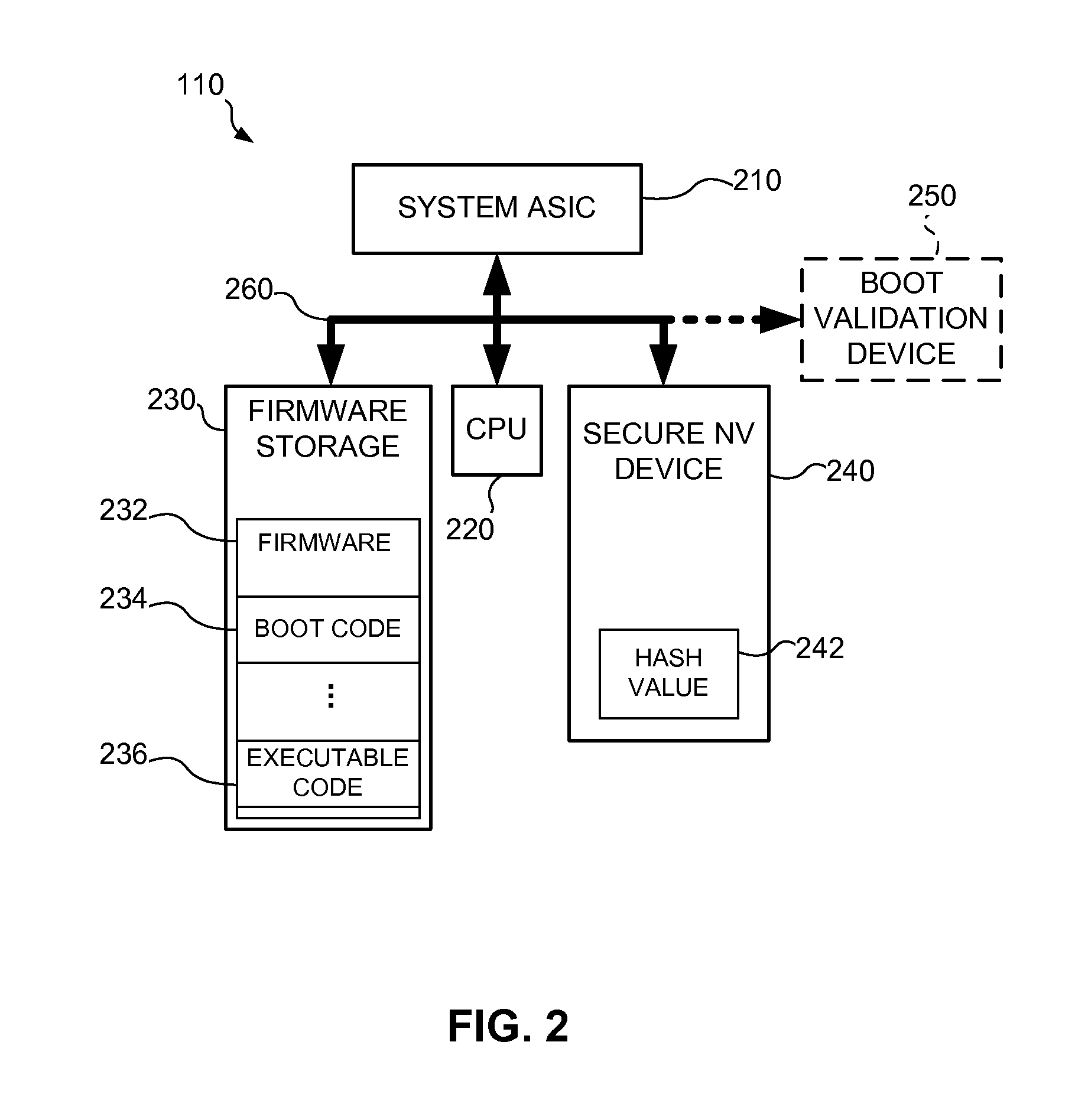
[0018]A boot validation system and method may be used in a computer system to validate boot code before allowing the computer system to execute the boot code. Once the boot code is validated, the boot code may be executed to validate other executable code (e.g., firmware) in the computer system. In an exemplary embodiment, the boot validation system and method may be used in an imaging device, such as an electrophotographic printer, an inkjet printer, a fax device, a copier, an all-in-one device or a multipurpose device. Those skilled in the art will recognize that the boot validation system and method may be used in other computer systems.
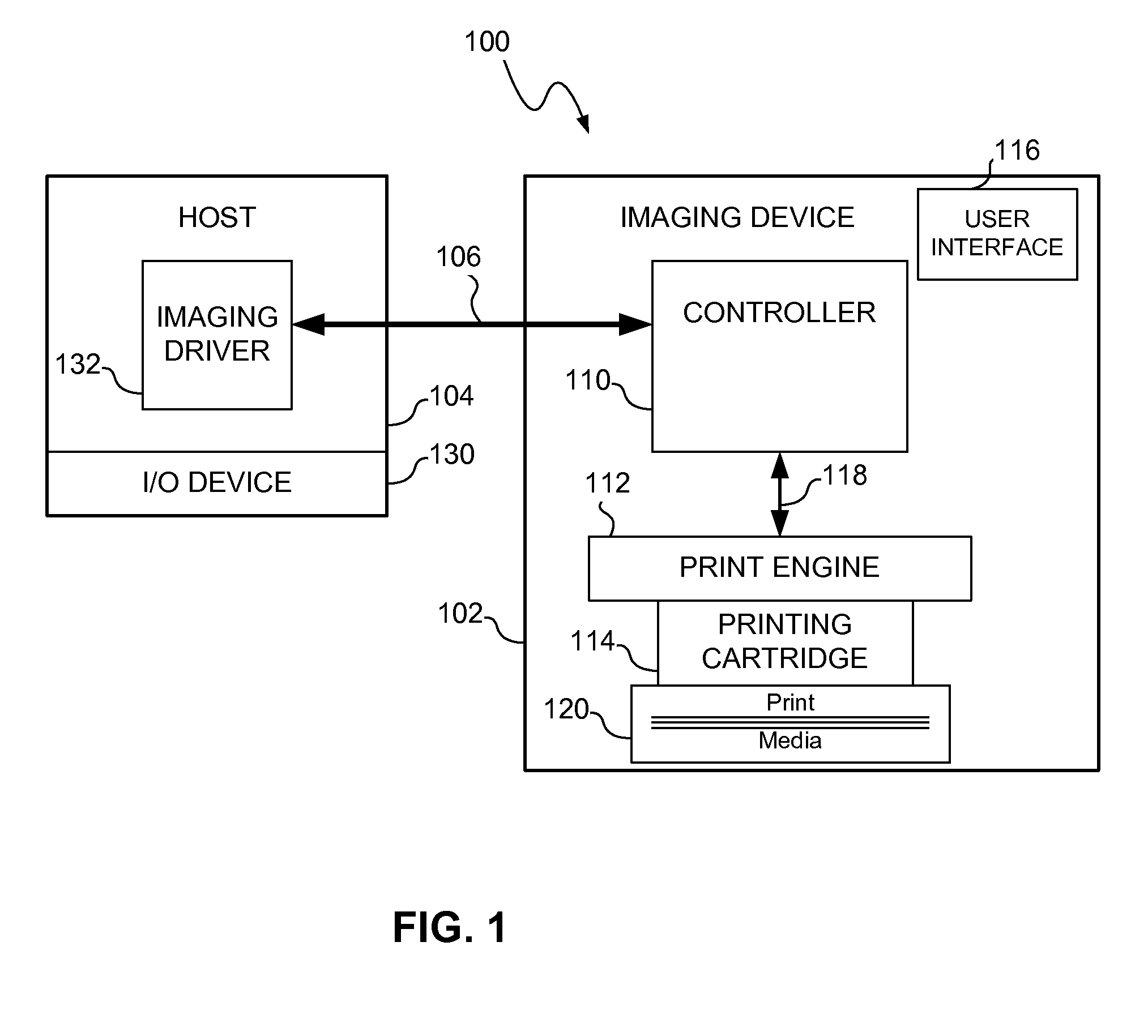
[0019]Referring to FIG. 1, a boot validation system and method, consistent with one embodiment, may be used in an imaging system 100. The imaging system 100 may include an imaging apparatus or device 102 and a host 104 that communicates via a communication link 106. The communication link 106 may include any structure that facilitates electronic c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com