Active validation for ddos and ssl ddos attacks
a technology of active validation and ddos, applied in the direction of unauthorized memory use protection, instruments, digital transmission, etc., can solve the problems of malicious clients, slow or inability to respond to other attacks, and vulnerable servers to cyber attacks, so as to improve the detection accuracy and detection accuracy of legitimate requests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021]The following detailed description refers to the accompanying drawings. Wherever possible, the same reference numbers are used in the drawings and the following description to refer to the same or similar parts. While several exemplary embodiments and features of the invention are described herein, modifications, adaptations, and other implementations are possible, without departing from the spirit and scope of the invention. Accordingly, the following detailed description does not limit the invention. Instead, the proper scope of the invention is defined by the appended claims.
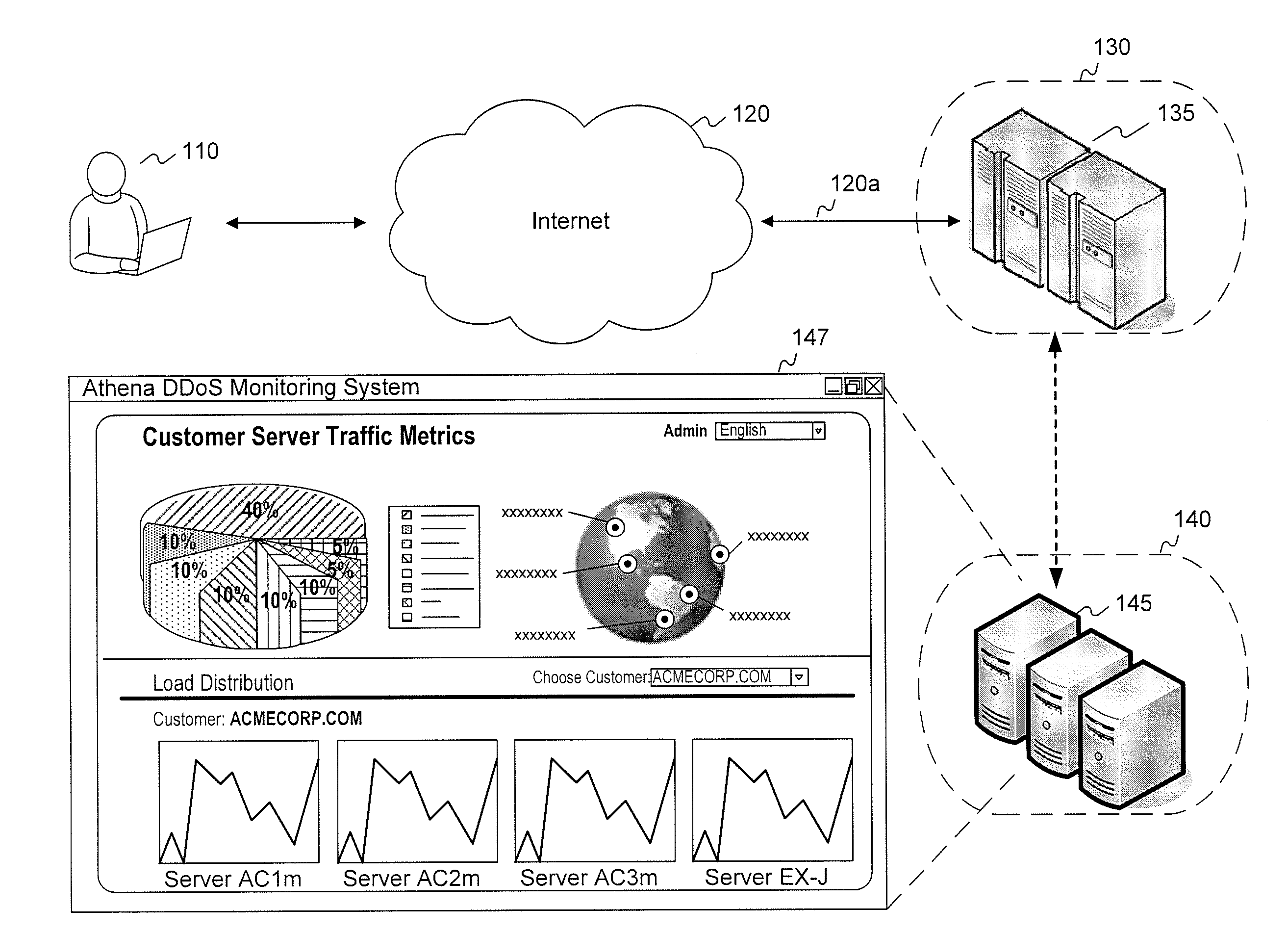
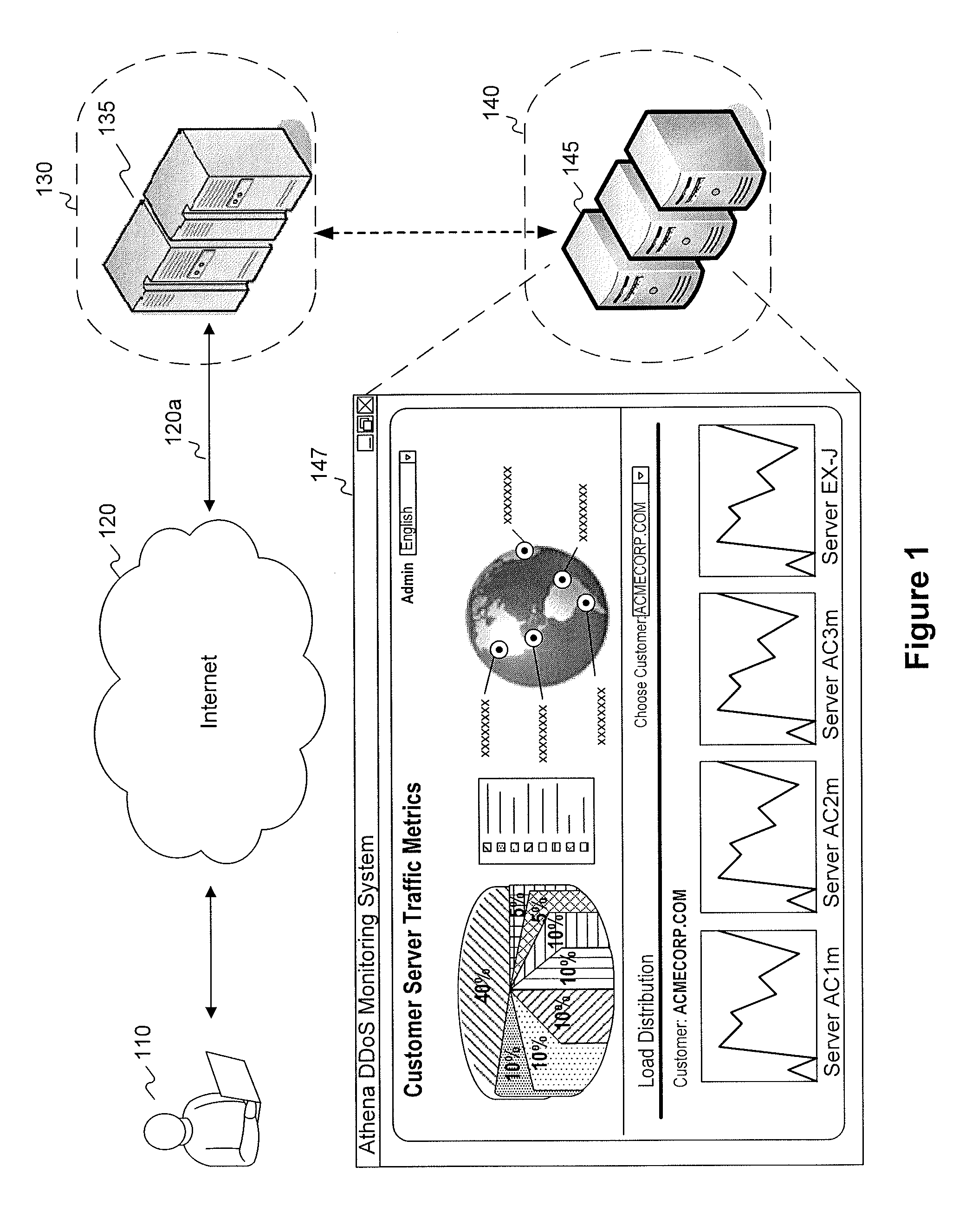
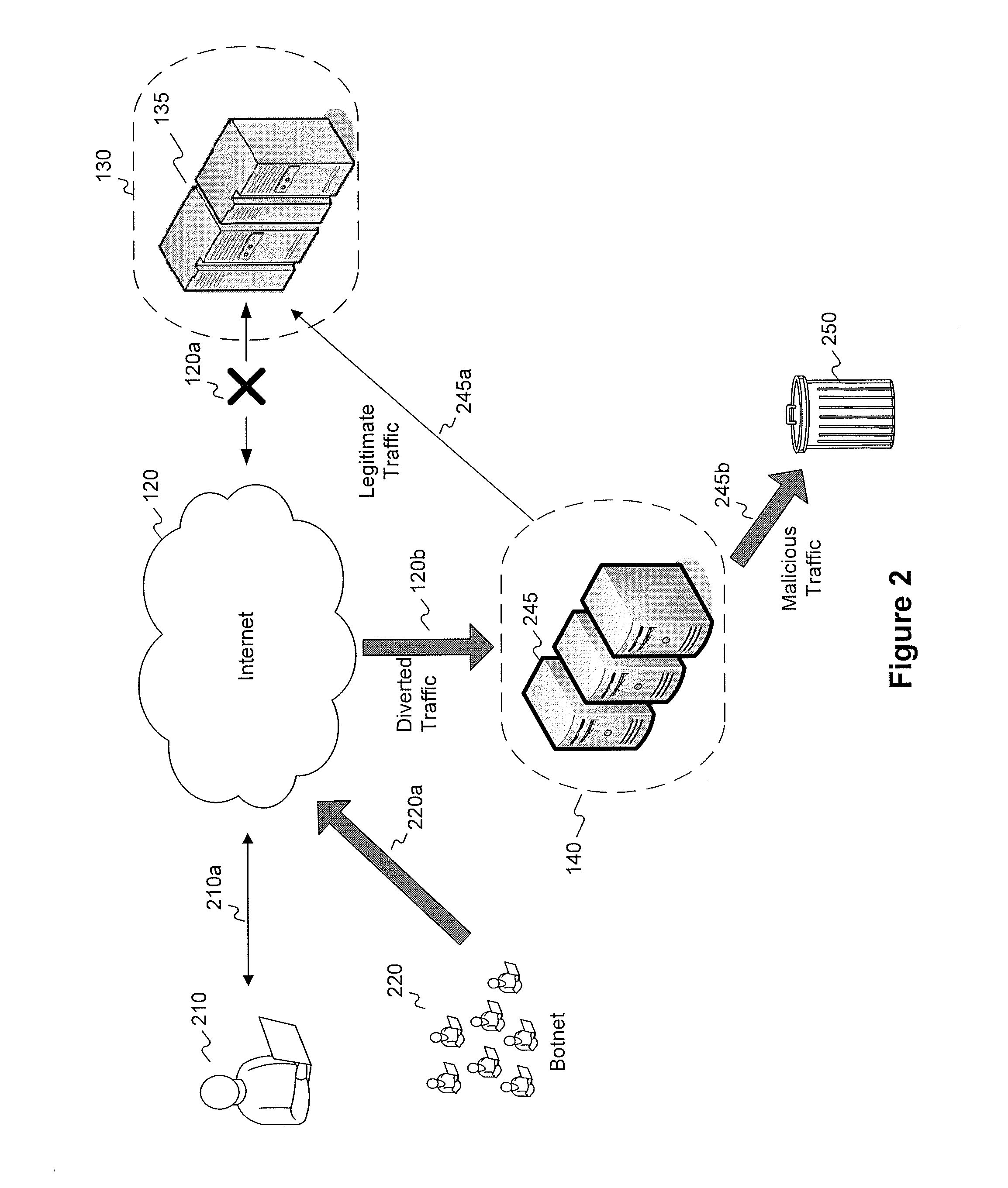
[0022]FIG. 1 is a diagram illustrating communications between one or more exemplary application servers and one or more clients consistent with certain disclosed embodiments. As shown in FIG. 1, one or more application servers 135 provide services to one or more clients or end users 110. Application servers 135 may comprise commercial web servers that service HTTP requests from clients 110 for web pages...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com