Identity Verification System Using Network Initiated USSD
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
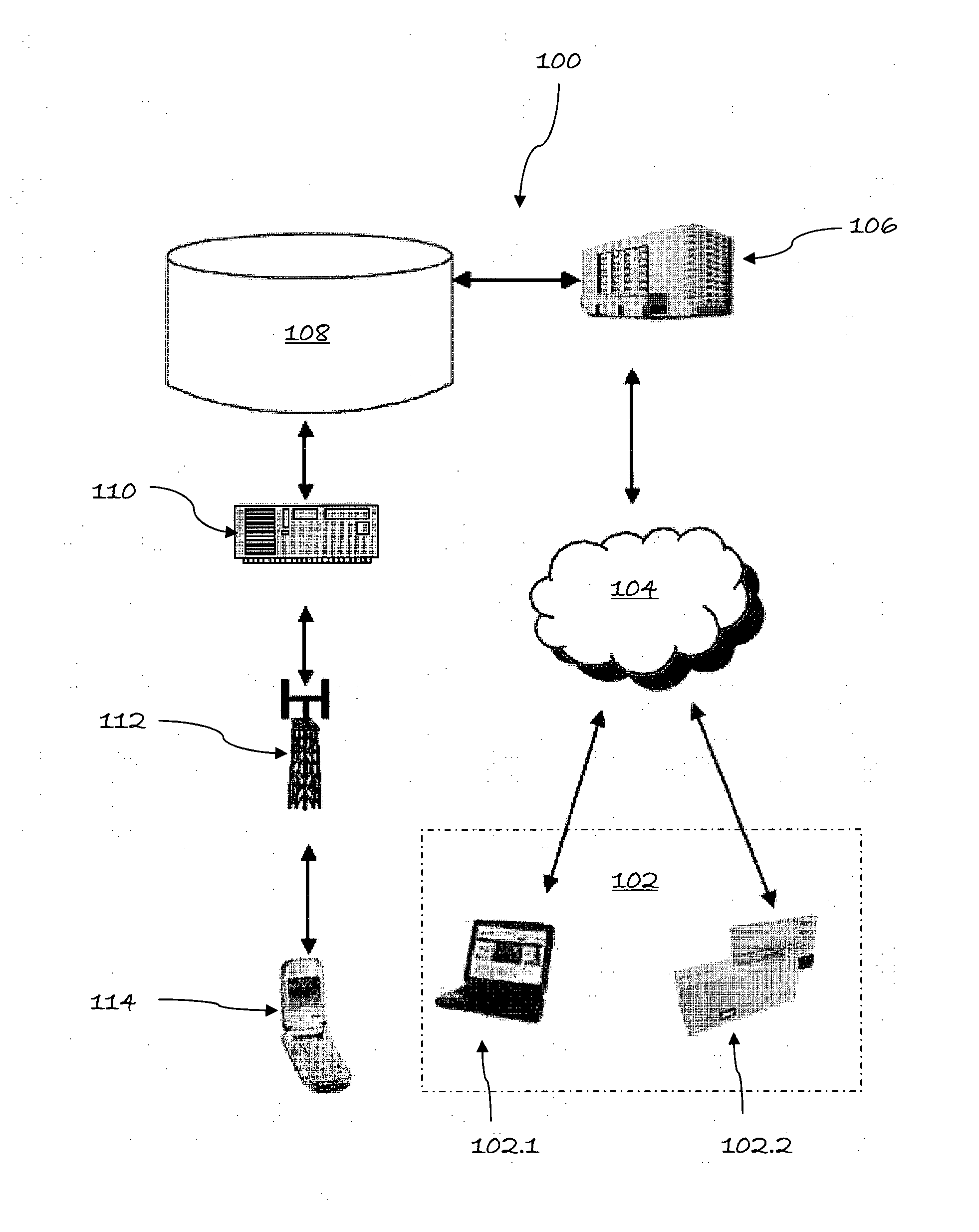
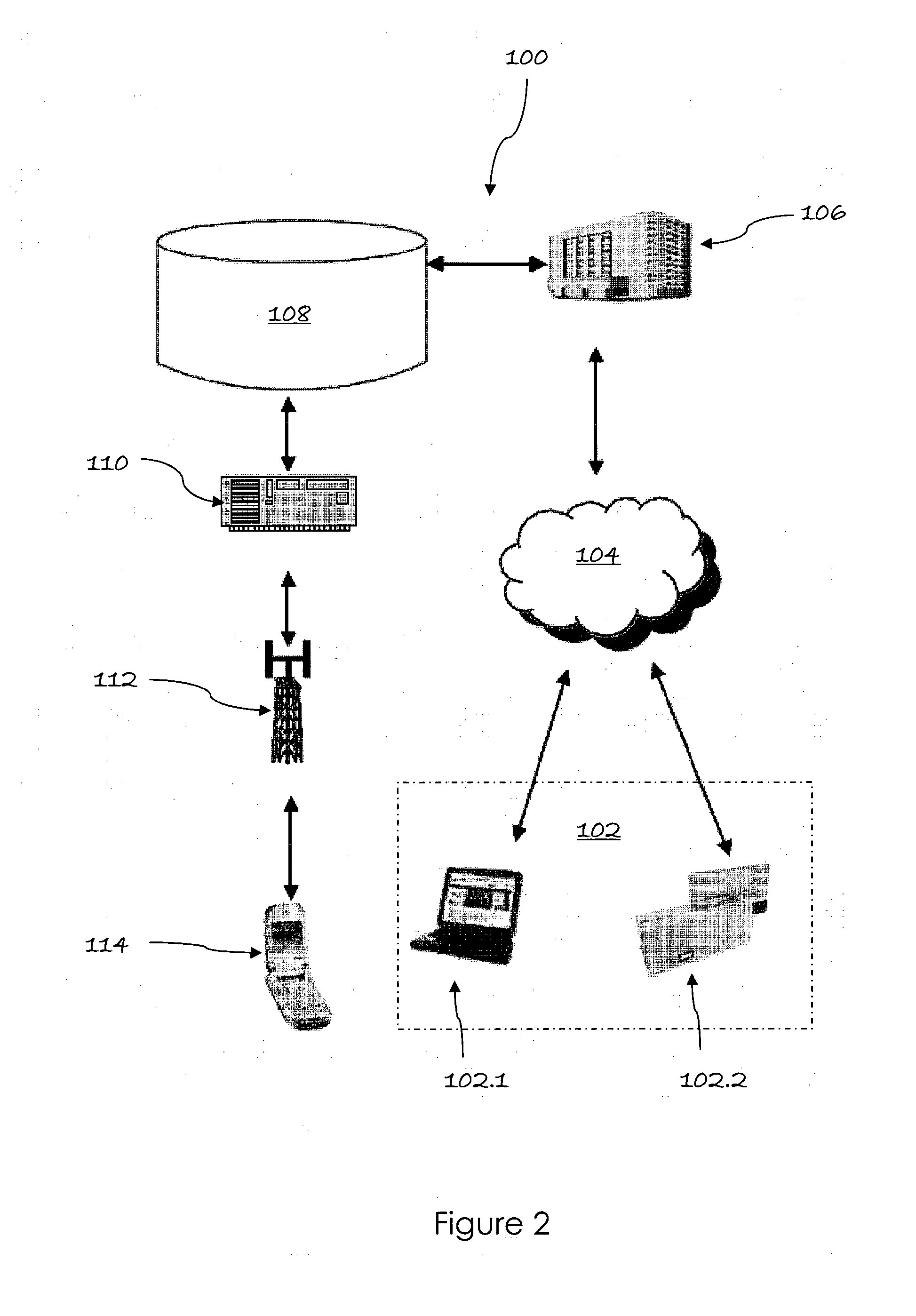
[0049]the invention is shown in FIG. 2, which illustrates, in diagrammatic form, an out-of-band authentication system 100 on which an on-line financial transaction request is processed for a user (illustrated in block outline 102). Two transaction examples are illustrated, the first being an on-line payment or banking transaction conducted on a personal computer 102.1 connected to the Internet 104 by means of which the transaction details are communicated. The second transaction example is that of a bank debit or credit card transaction 102.2 (which may be a card-present or card-not-present transaction), which commences with the user 102, as cardholder, supplying her card 102.2 (or simply the card details in a card-not-present transaction) to a merchant or the like. The card details are communicated to the Internet 104, which constitutes the primary or in-band communications channel on which the transaction 102 will be conducted and concluded.
[0050]A bank 106 is connected to the pri...
second embodiment
[0058]the invention is shown in FIG. 3, which illustrates, in diagrammatic form, an out-of-band authentication system 200 on which a merchant or retailer payment request is being processed, typically by means of a retailer POS terminal 201 connected to the Internet or some other form of telecommunications, which constitutes the primary or in-band communications channel on which the transaction will be conducted and concluded. A bank (not shown) is included in the connected to the primary, in-band channel by way of an Internet banking system. When the transaction request is received from the user POS terminal 201, the request is routed through an out-of-band authentication system 208 that is programmed to initiate and conduct a USSD communications session, by way of a network-initiated USSD (NI USSD) gateway 210 that is under the control of the out-of-band authentication system 208 and in communication with the mobile network operator 212 associated with the phone 214 of the user mak...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com