BUSINESS METHOD INCLUDING CHALLENGE-RESPONSE SYSTEM TO SECURELY AUTHENTICATE SOFTWARE APPLICATION PROGRAM INTERFACES (APIs)
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
case 1
[0089]B. Multiple Actors, Single Function
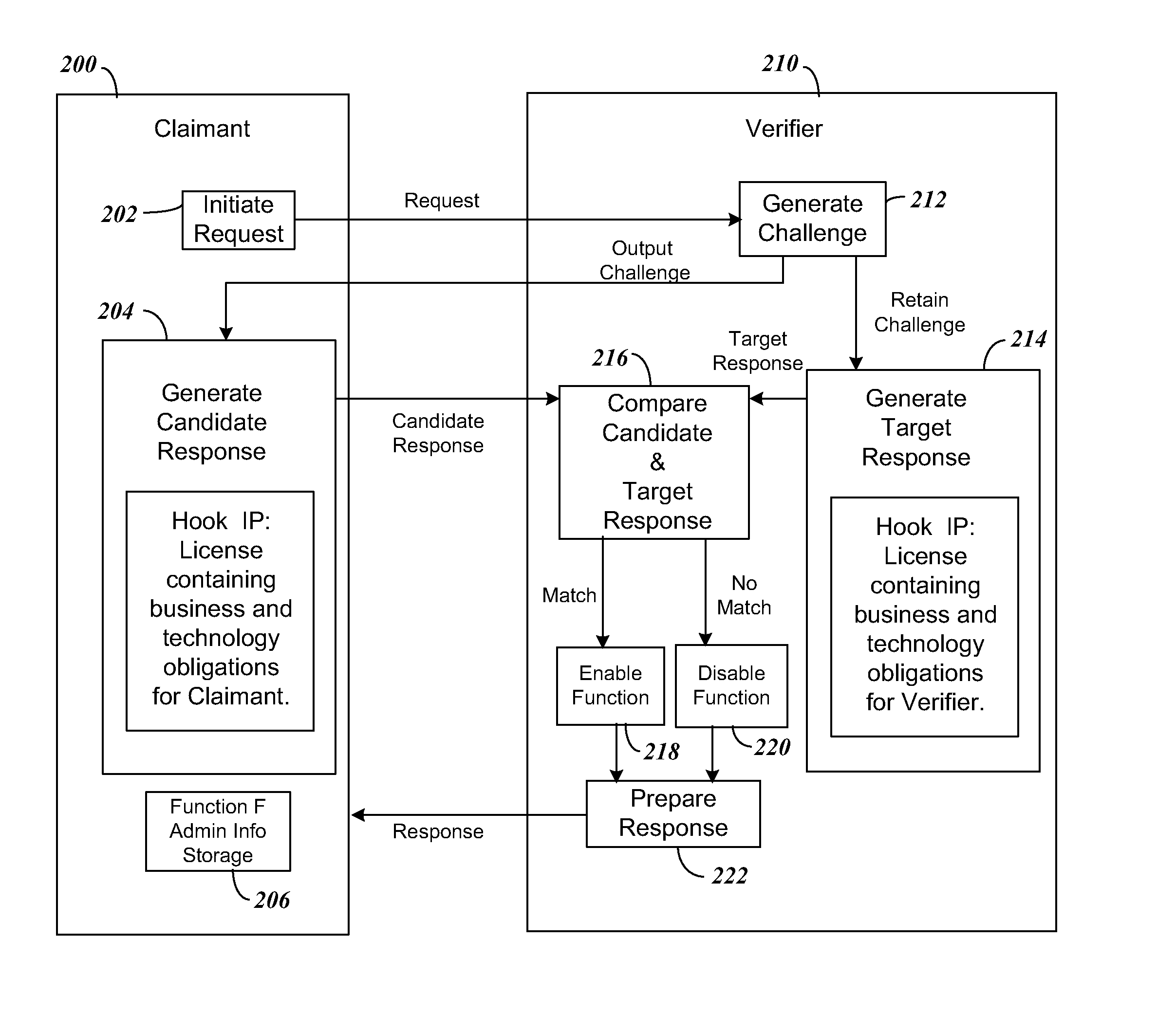
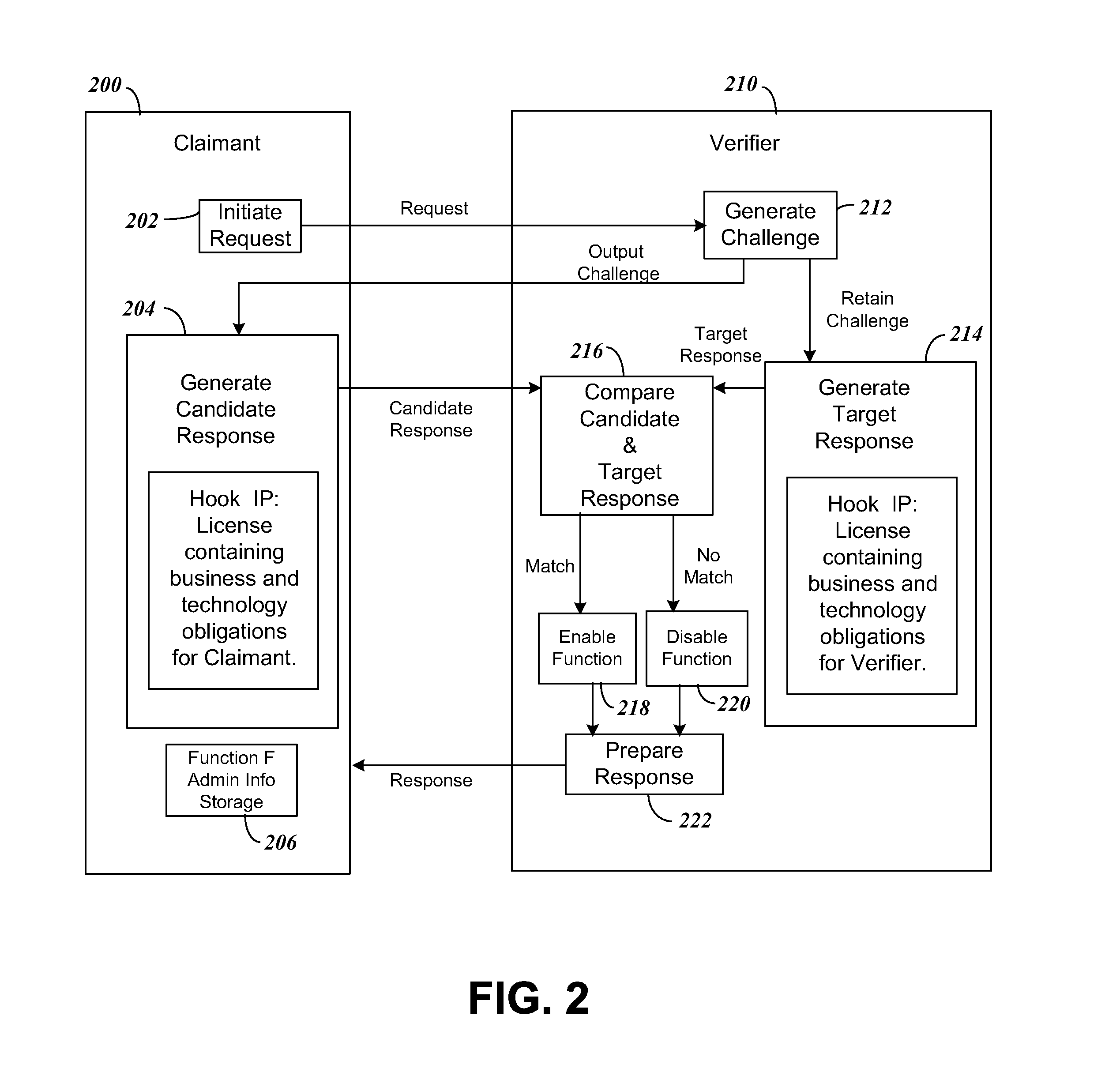
[0090]In this embodiment of the present invention, the Licensing Entity control multiple Actors that need to access a single function F1. This is achieved by beginning with a license agreement imposed upon an Actor A1 that owns or implements F1. The desirability of F1 then transfers the Licensing Regime to all other indirect users of F1, thereby spreading the Licensing Regime. Note that only Actor A1 implements F1; other users of F1 use F1 indirectly by asking A1 to operation function F1 for them through the Handshake Protocol, typically through an interface or API, where the requester acts as a Handshake Claimant and Actor A1 acts as the Handshake Verifier.
[0091]For this embodiment there must always be an “Alpha Actor” that is the very first to sign up to the Licensing Regime. The Alpha Actor will design their software or device to require the Handshake and Hook IP to perform its function F1 for other “Beta Actor” devices or software. This ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com