Method for prevention of cross site request forgery attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030]While the present invention is described herein with reference to illustrative embodiments for particular applications, it should be understood that the invention is not limited thereto. Those having ordinary skill in the art and access to the teachings provided herein will recognize additional modifications, applications, and embodiments within the scope thereof and additional fields in which the present invention would be of significant utility.
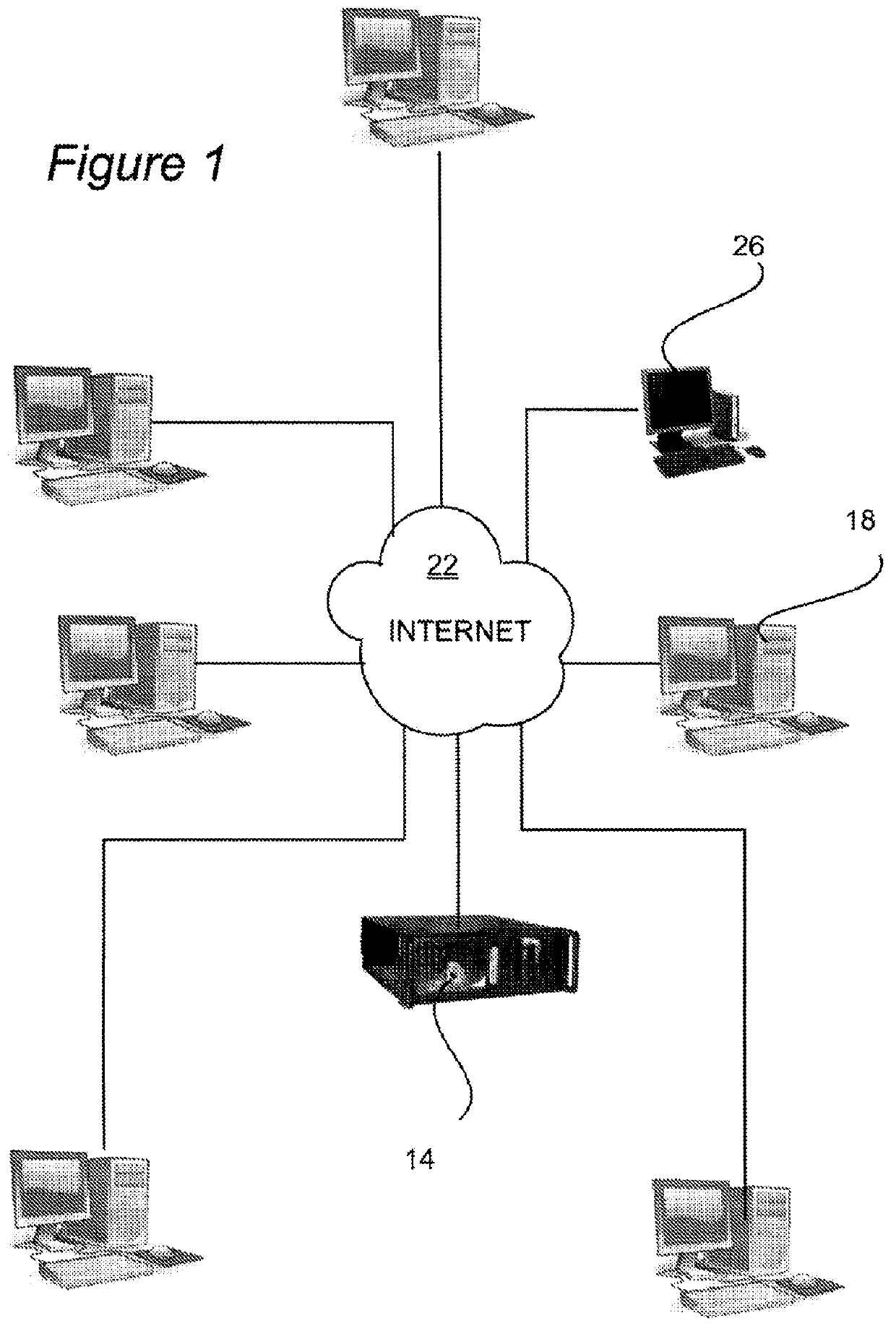
[0031]FIG. 1 is a diagram showing connection of the server 14 containing this invention 10 to the internet. Most other users 18 connected to the internet 22 are legitimate requestors who might wish at some point to access the web site maintained on this server 14. The web site has a URL of the standard form, server: port / token / resource. For example https: / / domain.com / path / to / web / application.cgi. One user 26, however, is malicious and wishes to launch an XSRF attach on this server 14 and its web site.
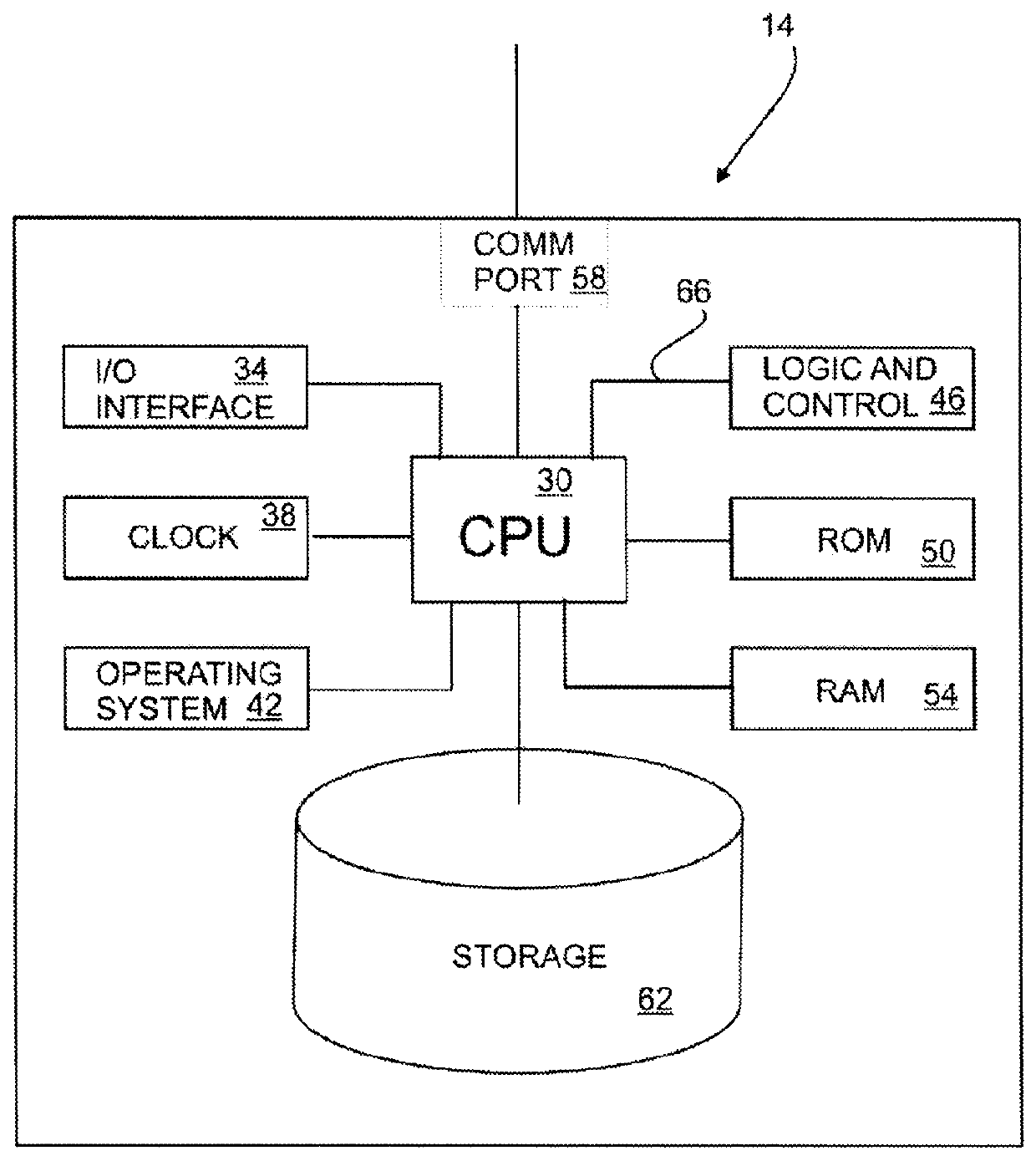
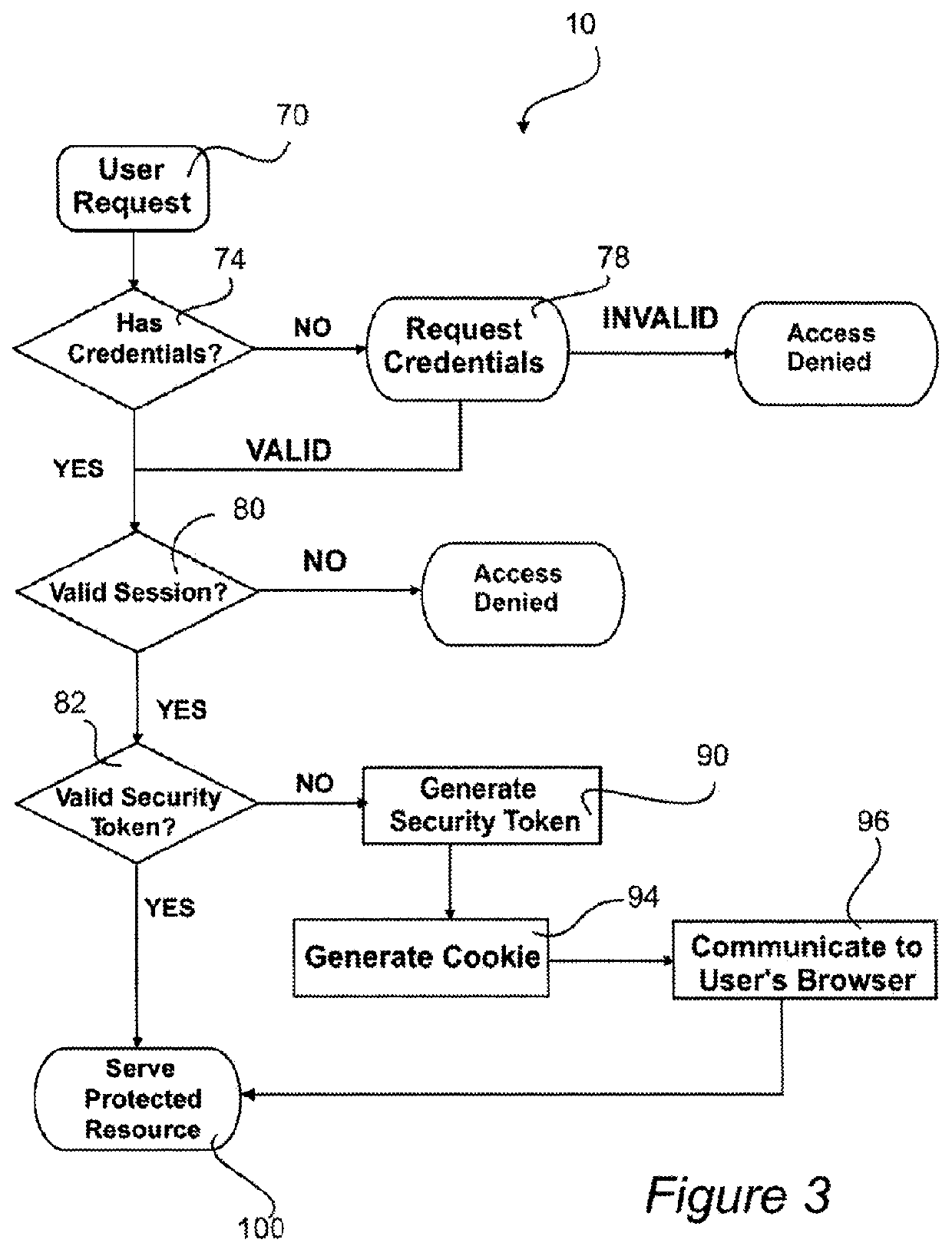
[0032]FIG. 2 depicts a block diagra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com