Password protected modular computer method and device
a modular computer and password protection technology, applied in the field of password protection modular computer methods and devices, can solve the problems of poor display technology of computing devices, poor viewing characteristics of smaller flat panel displays, and many limitations of laptop computers, so as to prevent accidental removal of acm, prevent illegal or unauthorized use, and facilitate and efficient
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
I. System Hardware
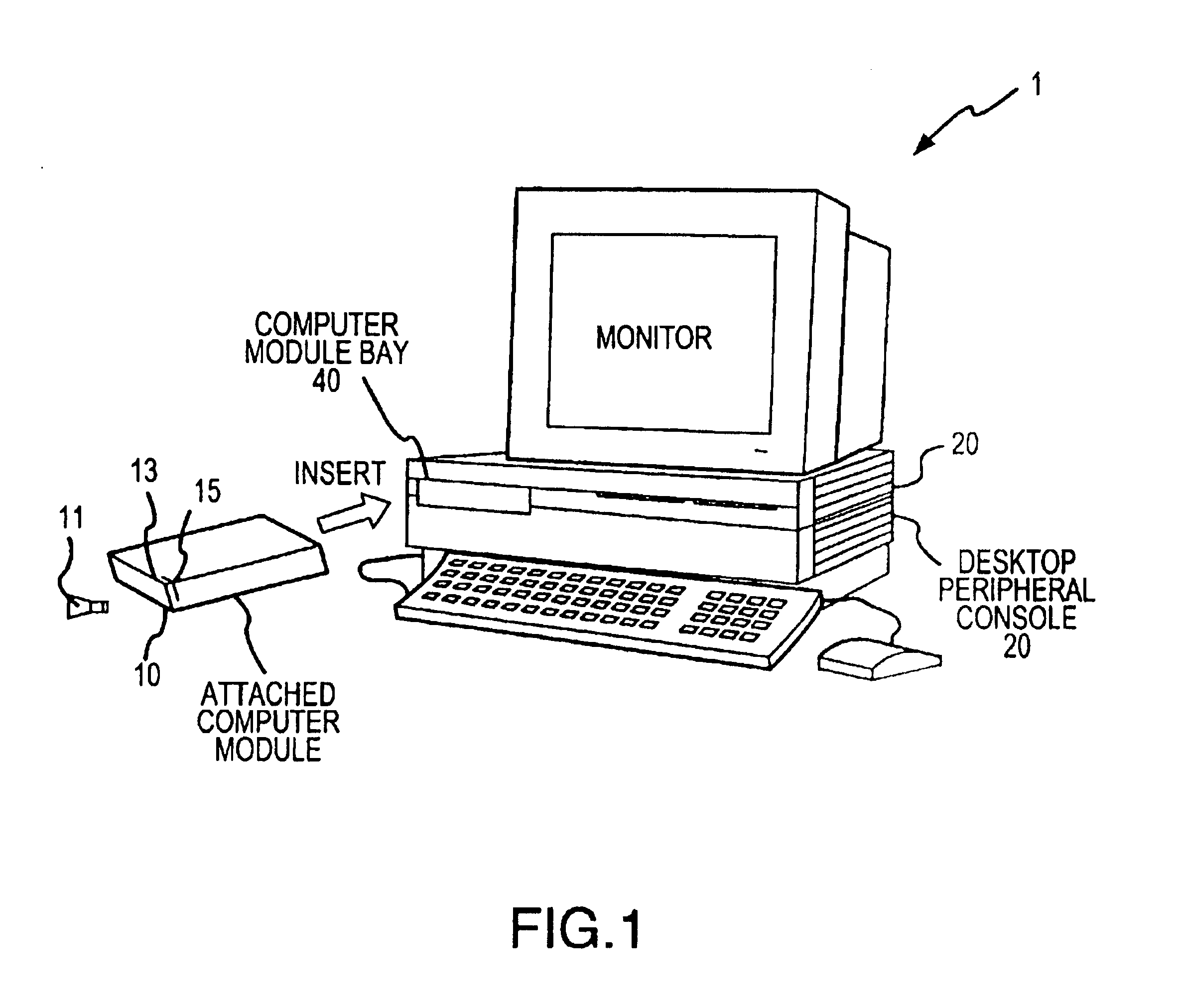
[0035]FIG. 1 is a simplified diagram of a computer system 1 according to an embodiment of the present invention. This diagram is merely an illustration and should not limit the scope of the claims herein. One of ordinary skill in the art would recognize other variations, modifications, and alternatives. The computer system 1 includes an attached computer module (i.e., ACM) 10, a desktop console 20, among other elements. The computer system is modular and has a variety of components that are removable. Some of these components (or modules) can be used in different computers, workstations, computerized television sets, and portable or laptop units.
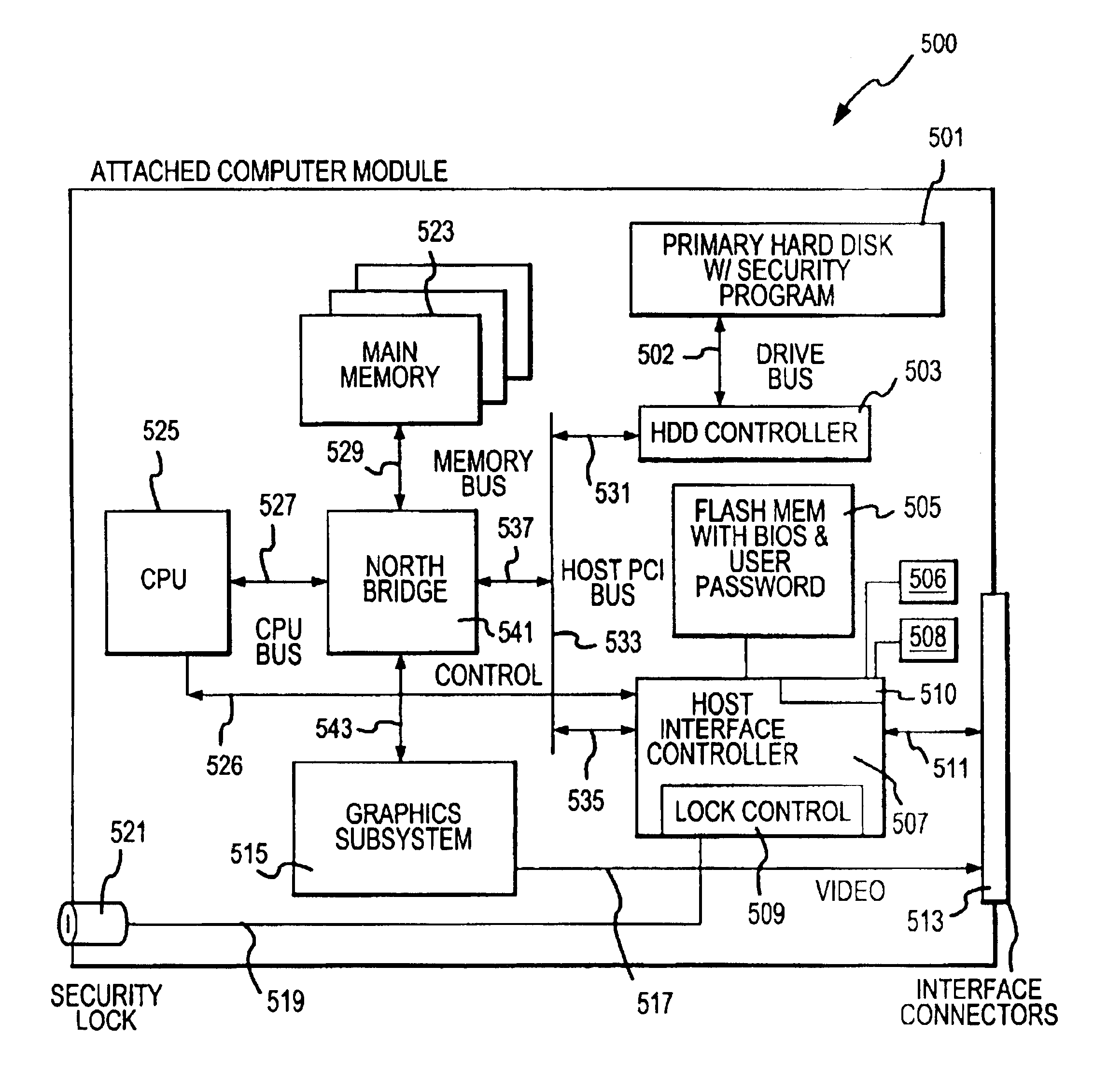
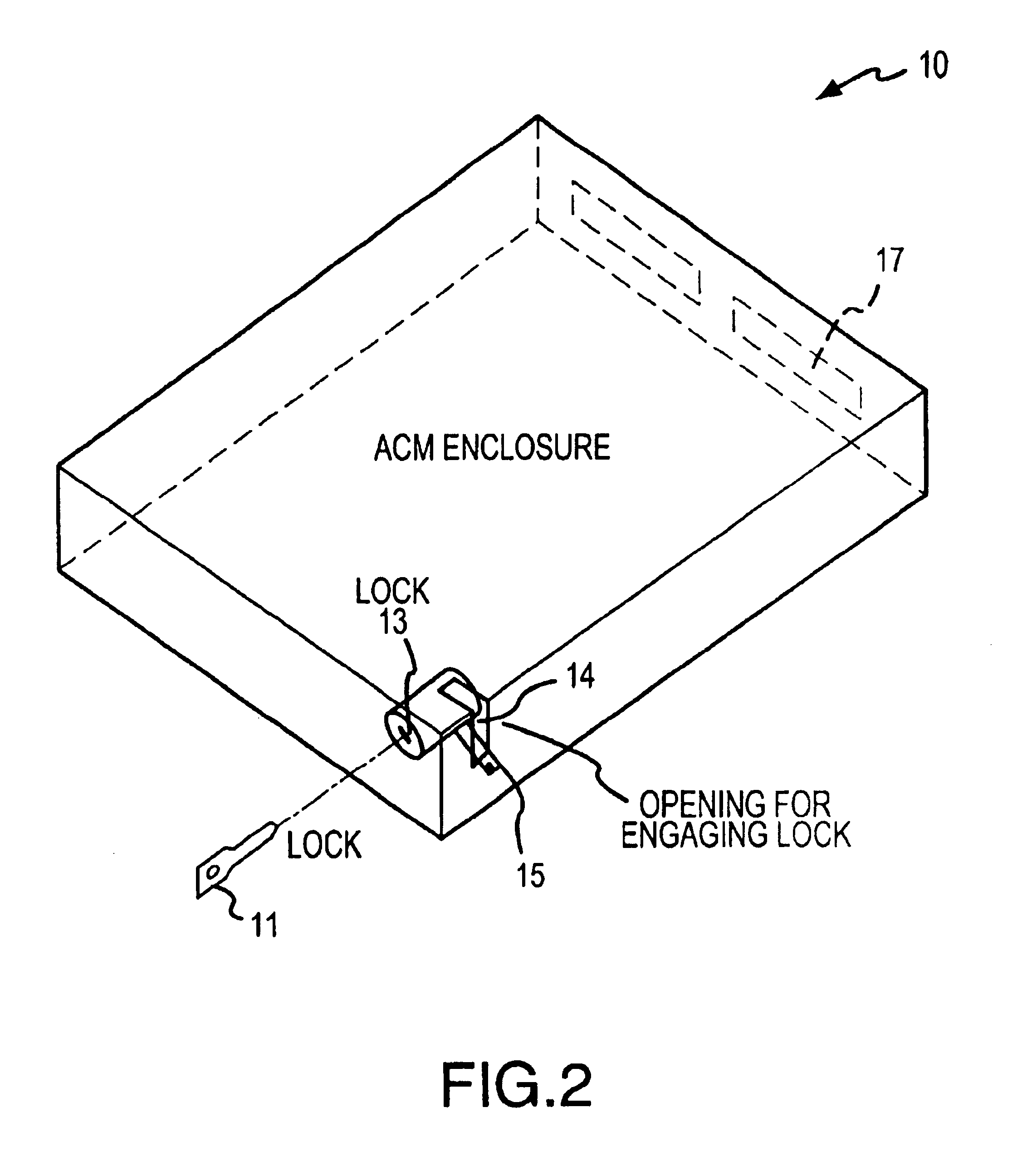
[0036]In the present embodiment, ACM 10 includes computer components, as will be described below, including a central processing unit (“CPU”), IDE controller, hard disk drive, computer memory, and the like. The computer module bay (i.e., CMB) 40 is an opening or slot in the desktop console. The CMB houses the ACM and provid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com