Method for ensuring system safety for window operating system
A Windows operating system and system security technology, applied in the field of ensuring system security to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
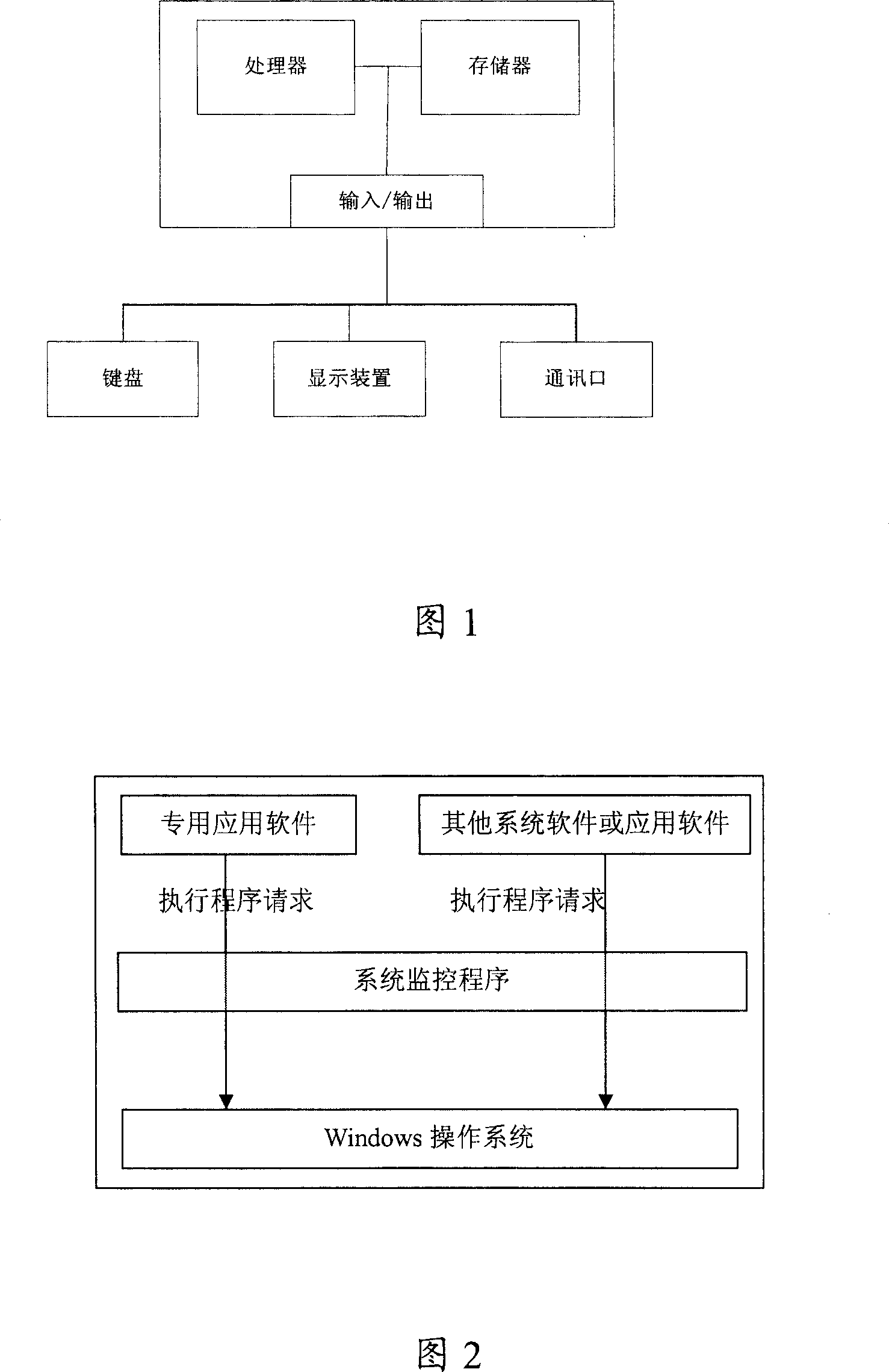
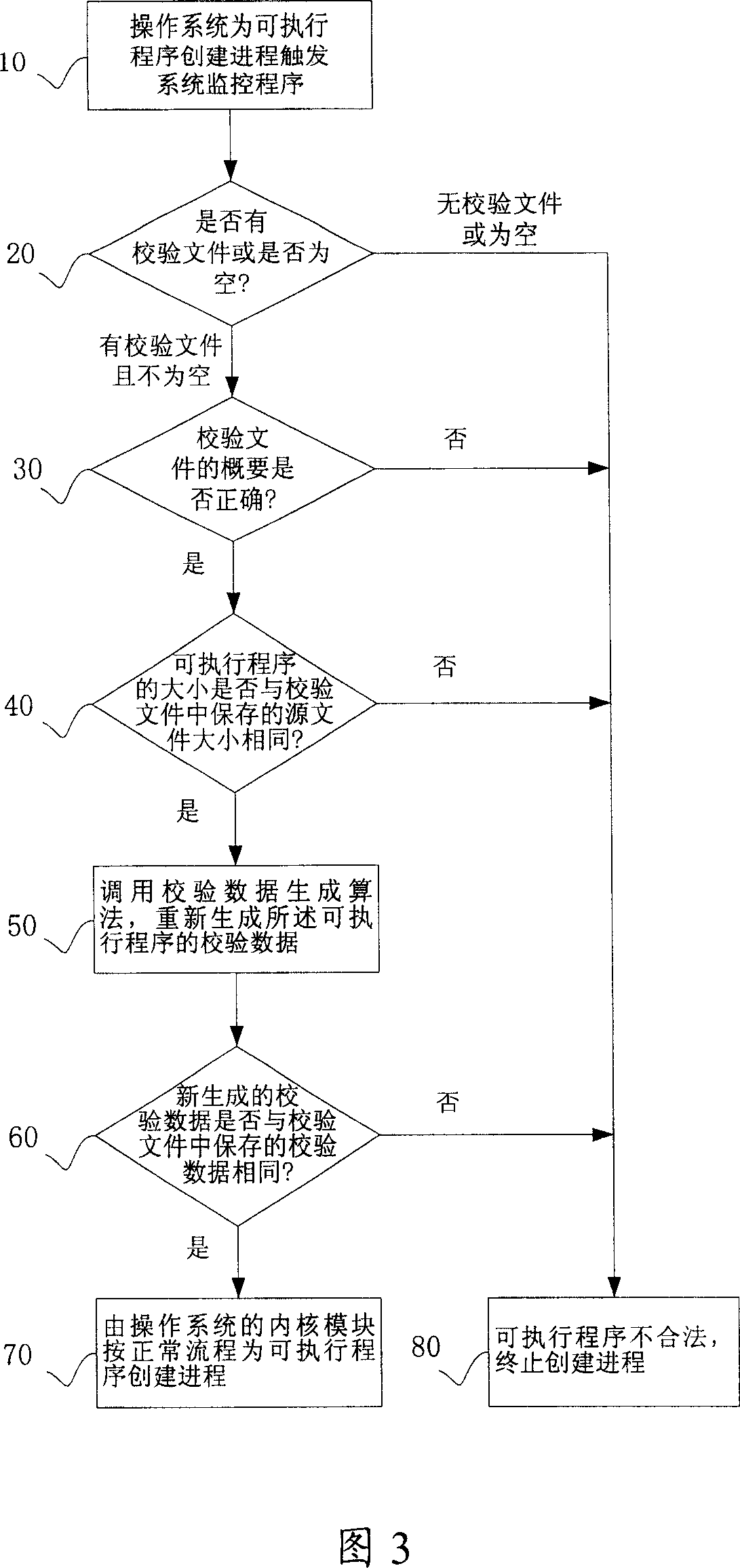
[0033] The system monitoring program of the present invention can be applicable to the protection of the application software system of the Windows operating system (ie Windows NT, 2000, XP, etc., Windows98 is not applicable) with NT as the core. By monitoring the process creation of the system, the operating system is prohibited from running unauthorized programs or programs infected by viruses, so as to ensure the security of the application software system.
[0034] Referring to Fig. 1, the basic structure of a computer has been shown in the figure, implements the method of the present invention with it. The processor of the computer is connected to the memory through the bus, and the input and output interfaces are also connected through the bus. The memory includes internal memory and external storage, and basic external storage such as hard disk; Connect to a network or other communication device.
[0035] Windows operating system programs and other executable programs ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com