Access control method and safety proxy server
A proxy server, access control technology, used in digital transmission systems, data exchange networks, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
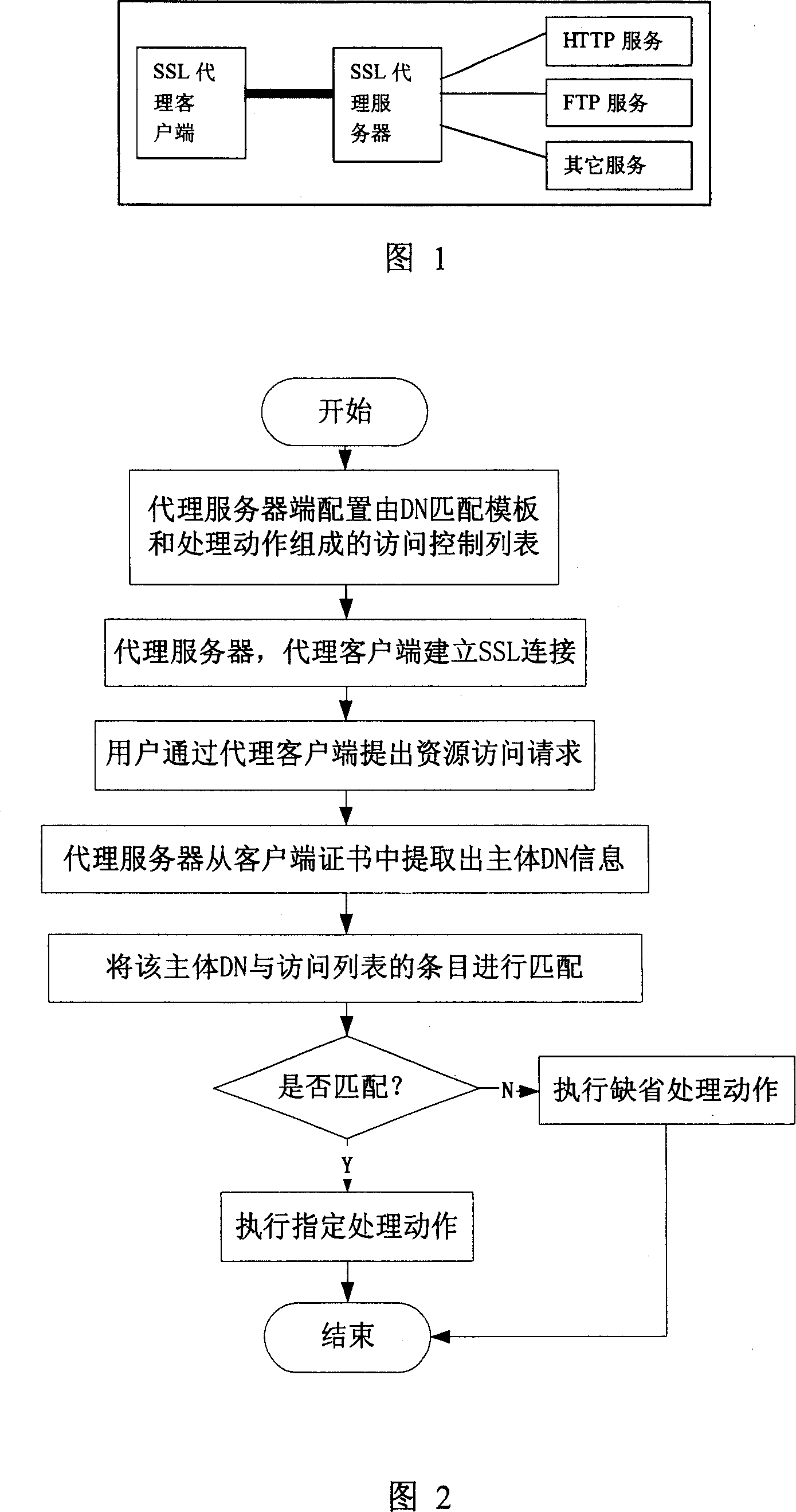
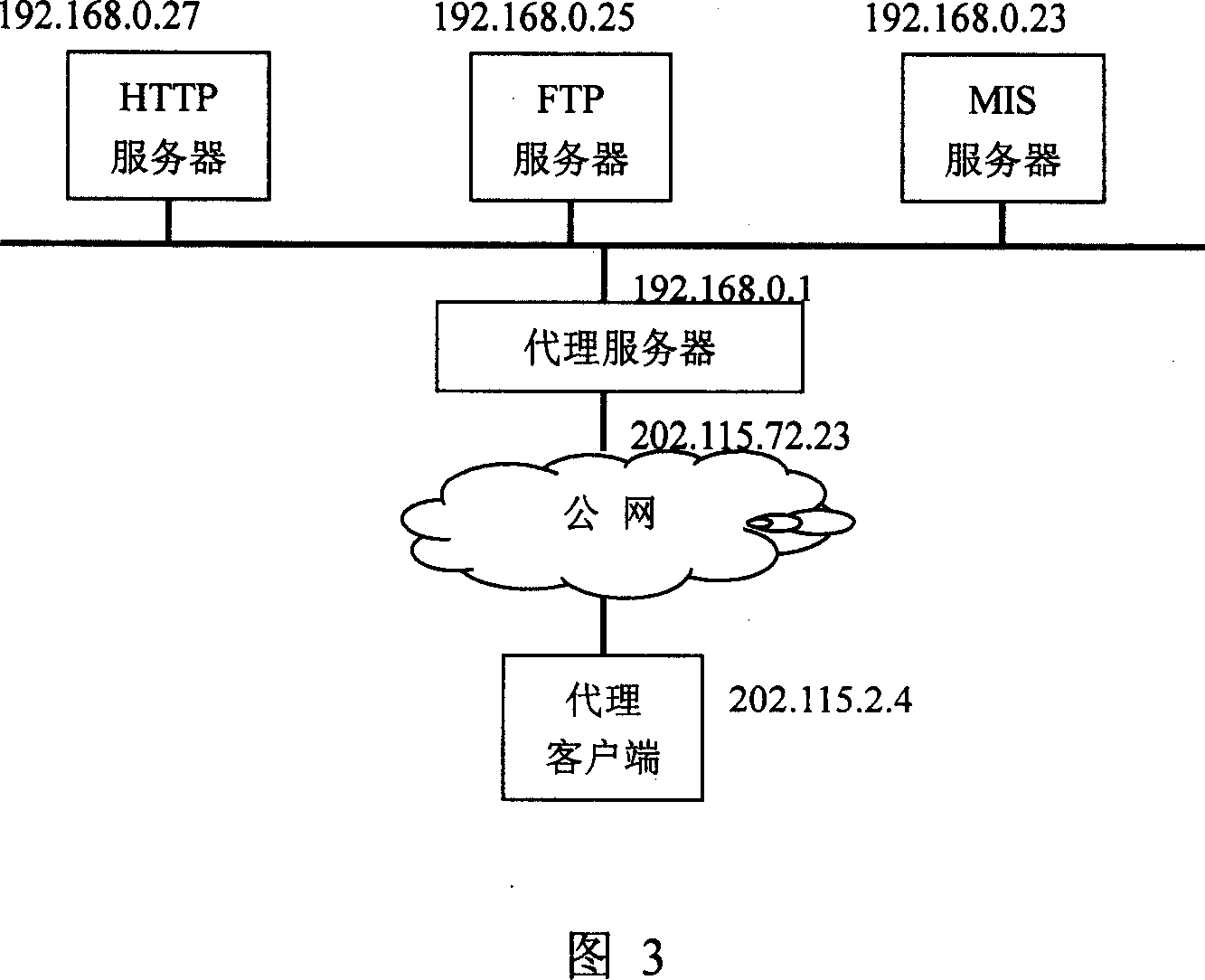
[0017] Referring to Fig. 1 and Fig. 2, the present invention relates to a proxy server and a proxy client based on the SSL protocol. In the SSL protocol, both server-side and client-side certificate verification are used, that is, the SSL server certificate is used on the SSL proxy server side, and the SSL client certificate is used on the SSL proxy client side. When users use it, they need to use the SSL client certificate to log in. In order to connect with the SSL proxy server. Since the subject DN is used in the digital certificate to identify the user's name, the access control based on the digital certificate is to control the access to the user specified in the subject DN. Implement an access control list based on the subject DN element in the digital certificate on the SSL proxy server side. Each control list can contain several entries, and each entry is composed of a DN template that needs to be matched and a processing action, that is, the subject DN can be specifie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com