Realizing method for preventing point-to point protocol recognization from being attacked in wideband cut-in network
A technology for accessing networks and implementing methods, applied in data exchange networks, user identity/authority verification, digital transmission systems, etc., can solve problems such as manual intervention, large manpower, and cost, to prevent attacks, suppress illegal attacks, and avoid The effect of the attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Below according to accompanying drawing and embodiment the present invention will be described in further detail:
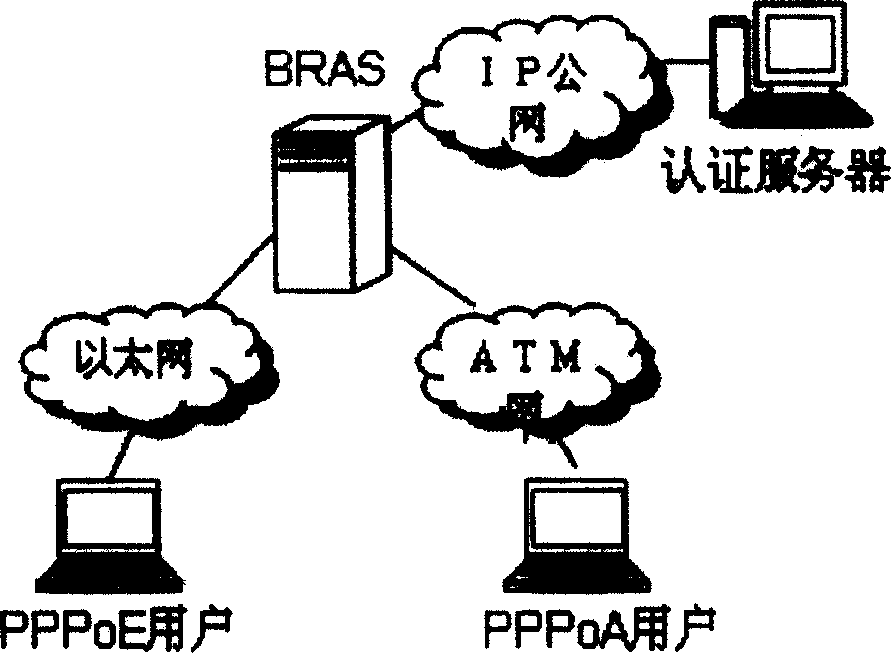
[0032] The invention provides a method for preventing PPP authentication attacks on BRAS (Broadband Remote Access Server) equipment, which can automatically identify PPP authentication attack users according to configured judgment conditions, and filter attack messages, thereby preventing illegal online access The process uses authentication packets to attack BRAS devices and authentication servers.
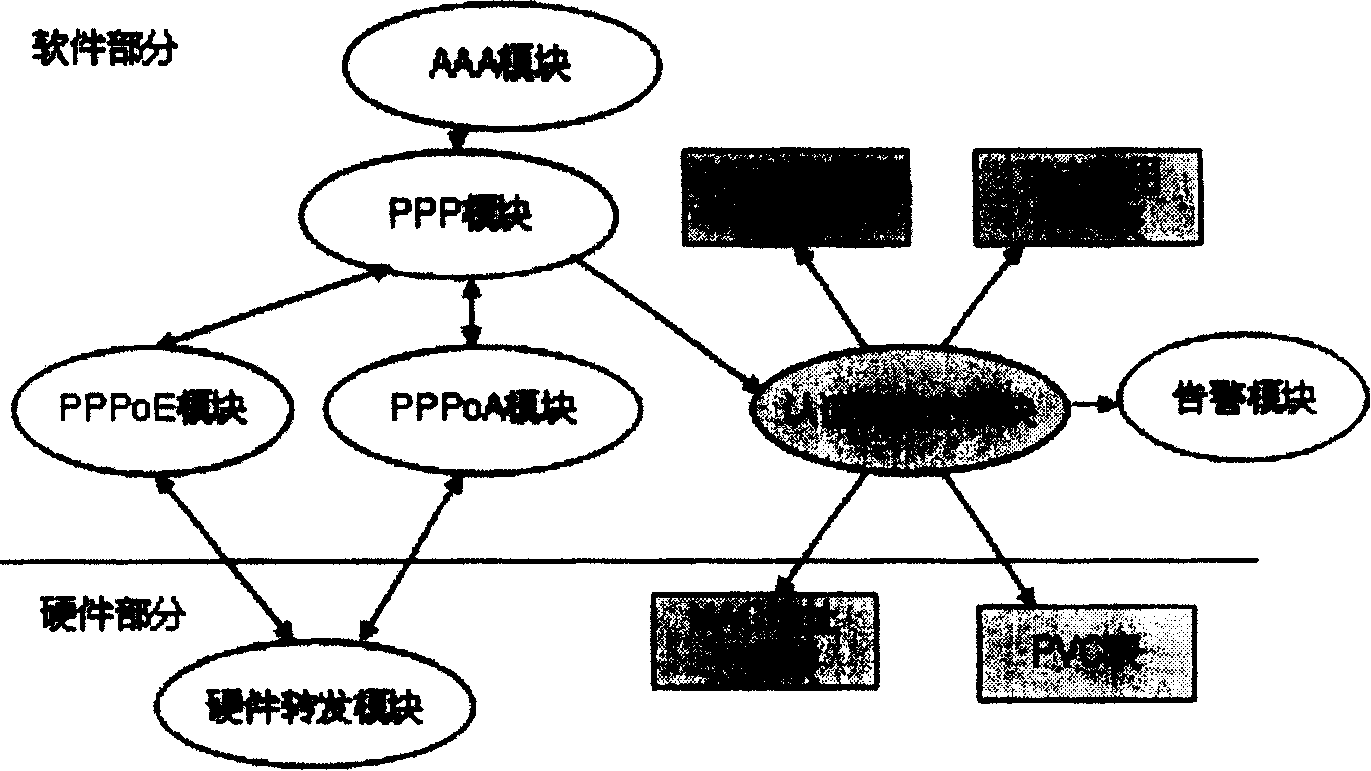
[0033] The present invention is a solution combining software and hardware, and the whole solution is all realized on the BRAS. Such as figure 2 The structure diagram of the PPP authentication attack defense system is shown. The authentication anti-attack software module, the authentication failure tracking database, and the attack disabled user table are added to the BRAS device. The MAC address filtering table is added to the hardware part of the access s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com