Configuration recovery device and the method thereof
A recovery method and recovery point technology, applied in the fields of telecommunications and databases, can solve problems such as failure to support configuration recovery well, and save time and storage resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
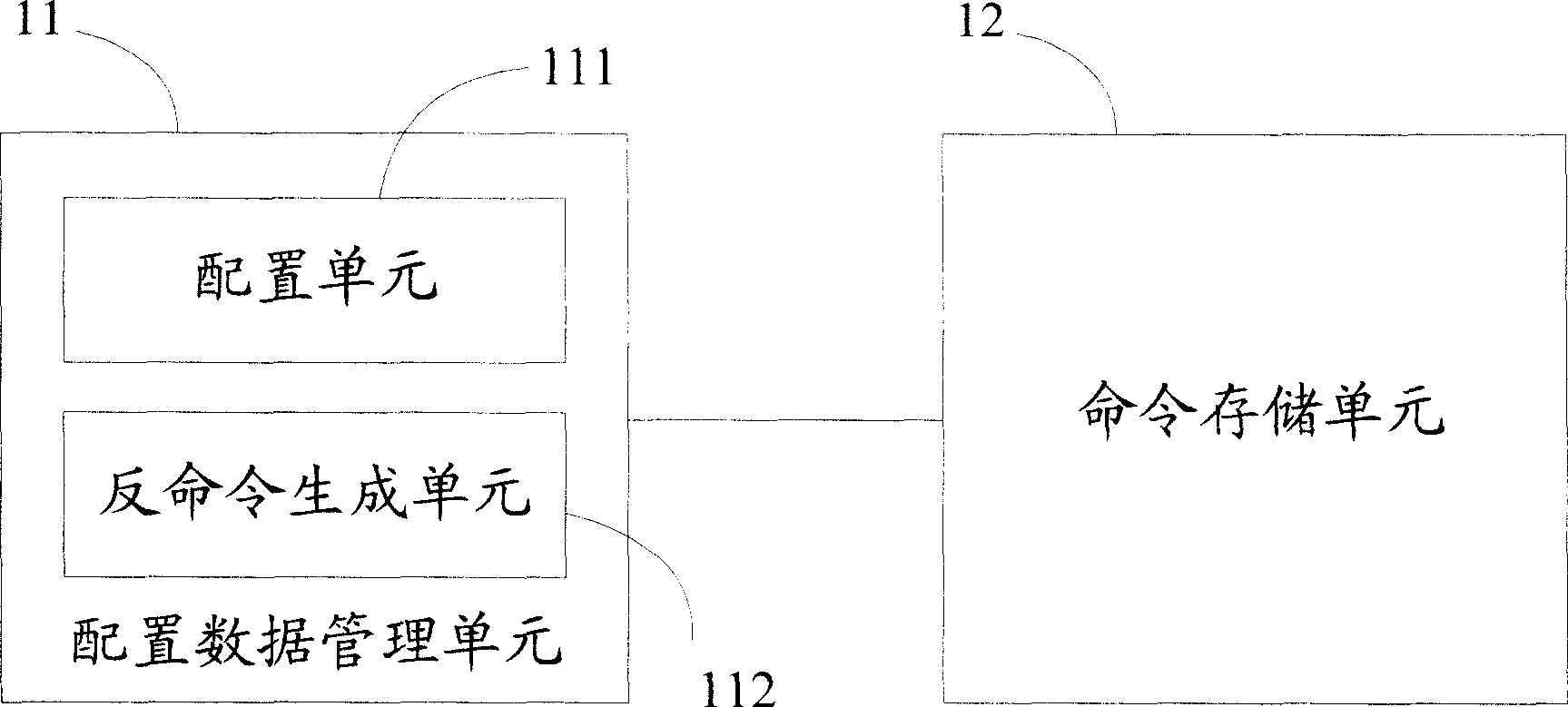
[0032] Embodiment one, when adopting figure 1 When restoring the device with the configuration shown, if the user finds that the configuration is incorrect after adding the configuration object A, the configuration needs to be restored.
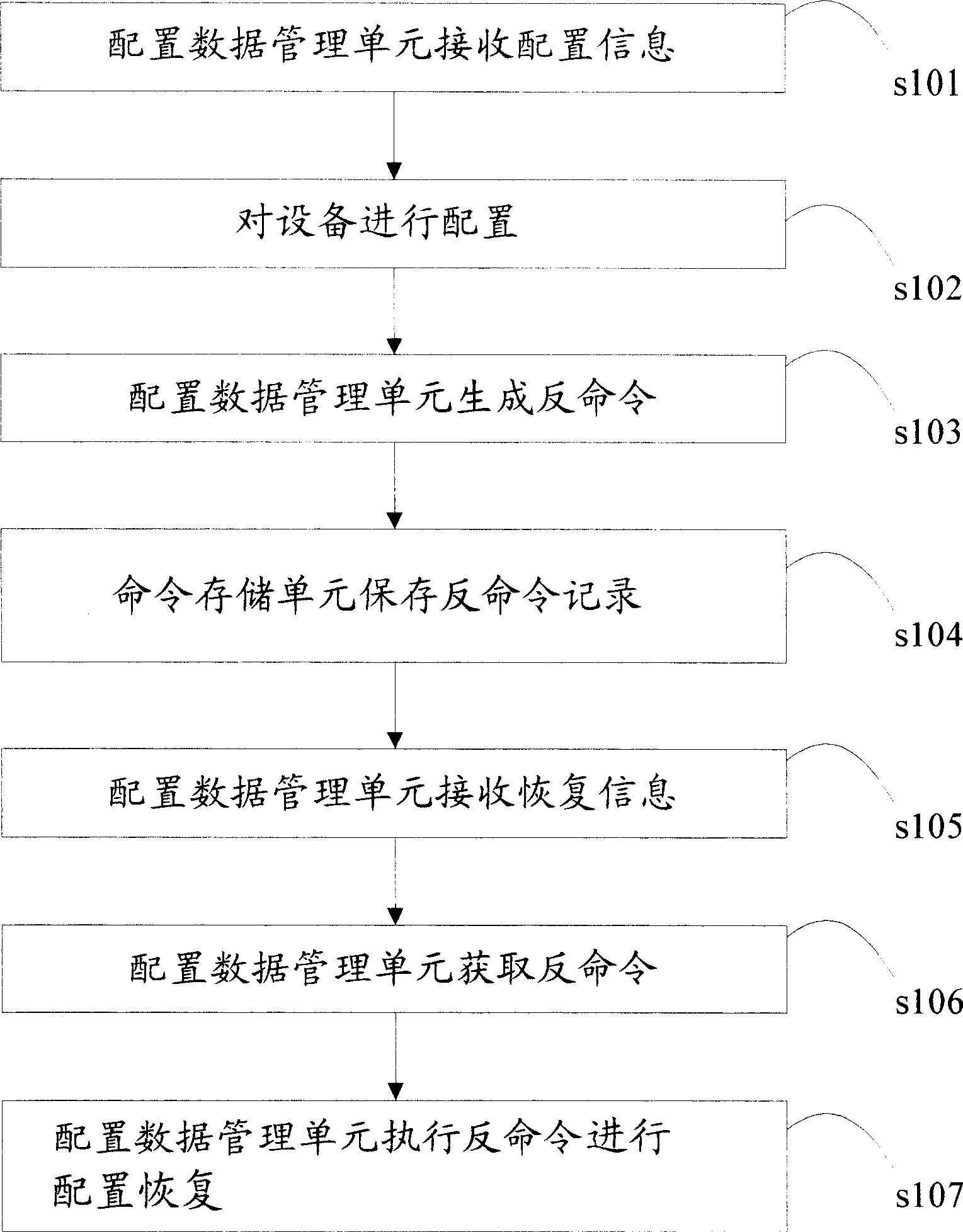
[0033] The flow of a configuration recovery method of the present invention is as follows: figure 2 shown. First, the present invention generates anti-commands during configuration; then, when an error occurs due to modification of configuration data, the anti-commands are executed to recover the configuration and restore the system to the state before configuration. refer to figure 2 , the present invention comprises the following steps:
[0034] In step s101, the configuration data management unit receives configuration information. That is, the user sends a configuration operation command to the configuration data management unit 11, and the configuration unit 111 receives the configuration operation command sent by the user, and sav...
Embodiment 2
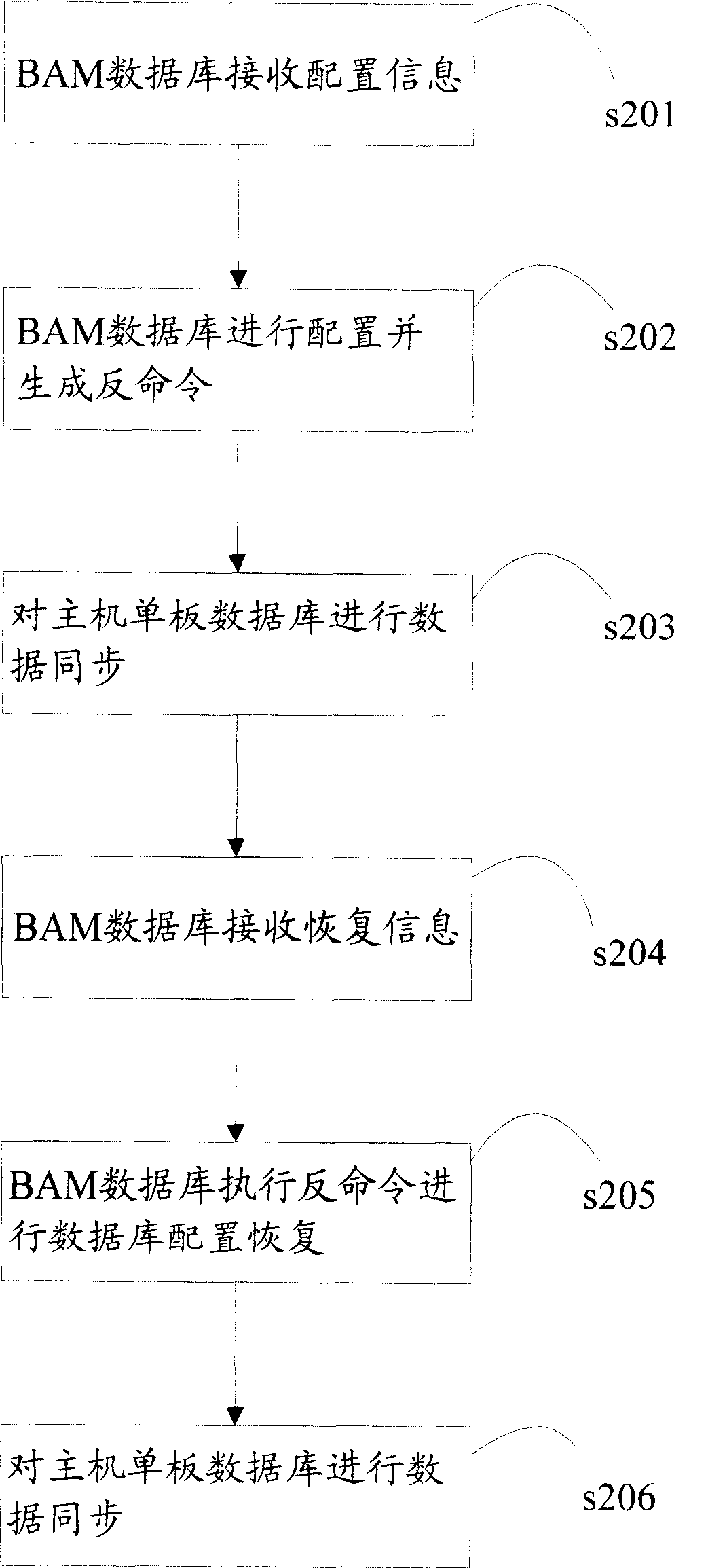
[0042]Embodiment 2, a distributed single database system includes a BAM (Back Administrative Module, back-end management module) database and a host single-board database. Wherein, the BAM database is connected to the host board database for data transmission. If the user finds that the configuration is incorrect after adding configuration data A in the database, it will cause network abnormalities, so the database configuration needs to be restored.
[0043] when using figure 1 When configuring the recovery device as shown, the flow of a configuration recovery method of the present invention is as follows image 3 shown. Firstly, the present invention generates anti-commands when configuring the database; then, when the network is abnormal due to modifying the configuration data, the anti-commands are executed to recover the database configuration and restore the database to the state before configuration. refer to image 3 , the present invention comprises the following ...
Embodiment 3
[0050] Embodiment 3, when the telecommunication equipment expands, the configuration of adding destination signaling points, adding signaling link groups and adding signaling links is performed; if a configuration error is found during the upgrade process, the configuration needs to be restored to the one before the expansion state.
[0051] when using figure 1 When configuring the recovery device as shown, the flow of a configuration recovery method of the present invention is as follows Figure 4 As shown, firstly, the present invention sets the configuration recovery point before capacity expansion, then generates counter-commands during configuration, and finally, when an error occurs due to modification of configuration data, executes counter-commands to recover the configuration and restore the system to Sets the state when the restore point was configured. refer to Figure 4 , the present invention comprises the following steps:
[0052] In step s301, the system rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com