Modified hash method, and application
A hash and hash function technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problem of large changes in the number of memory times, improve utilization efficiency, and overcome the effects of large changes in the number of memory accesses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
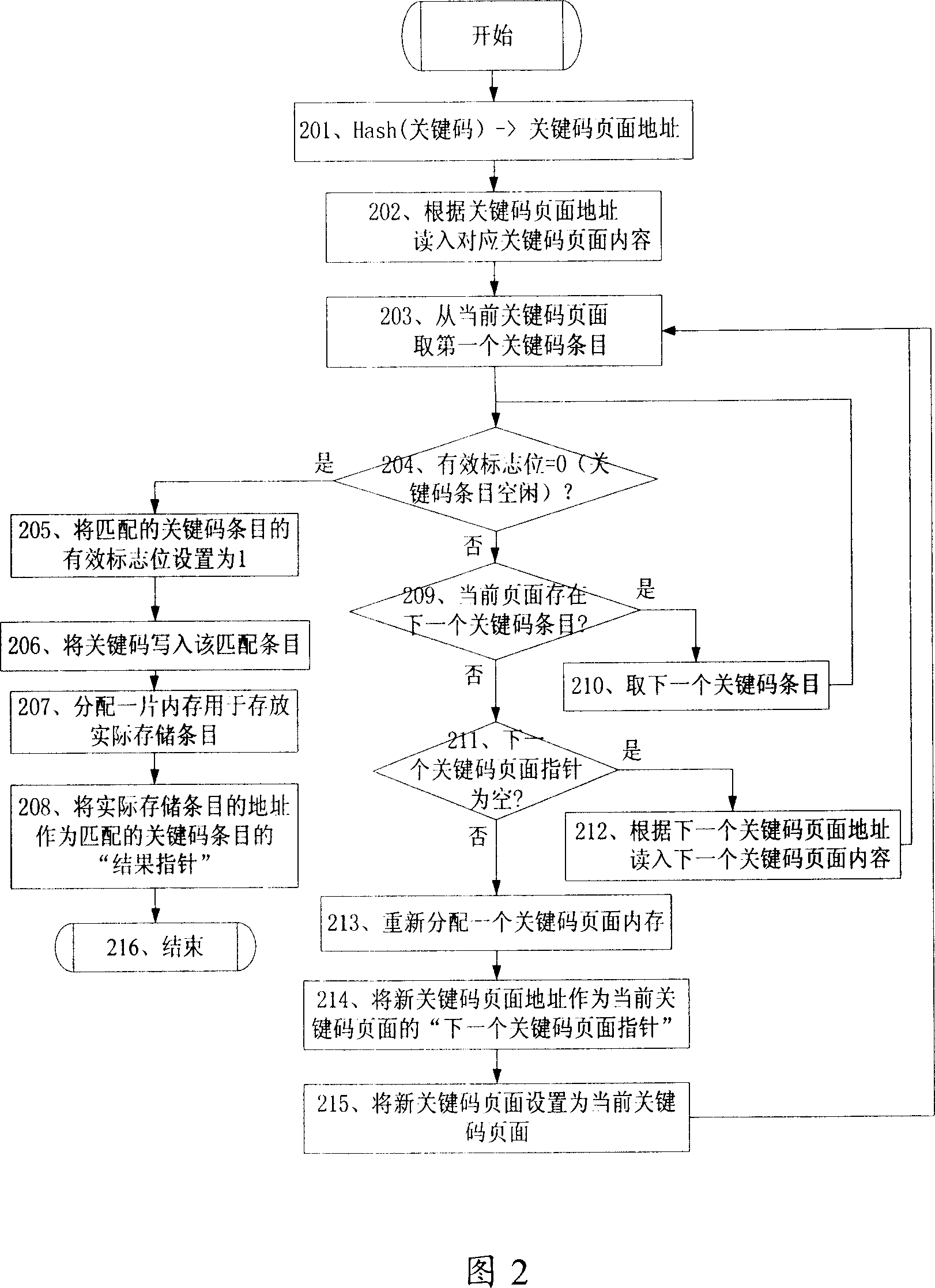
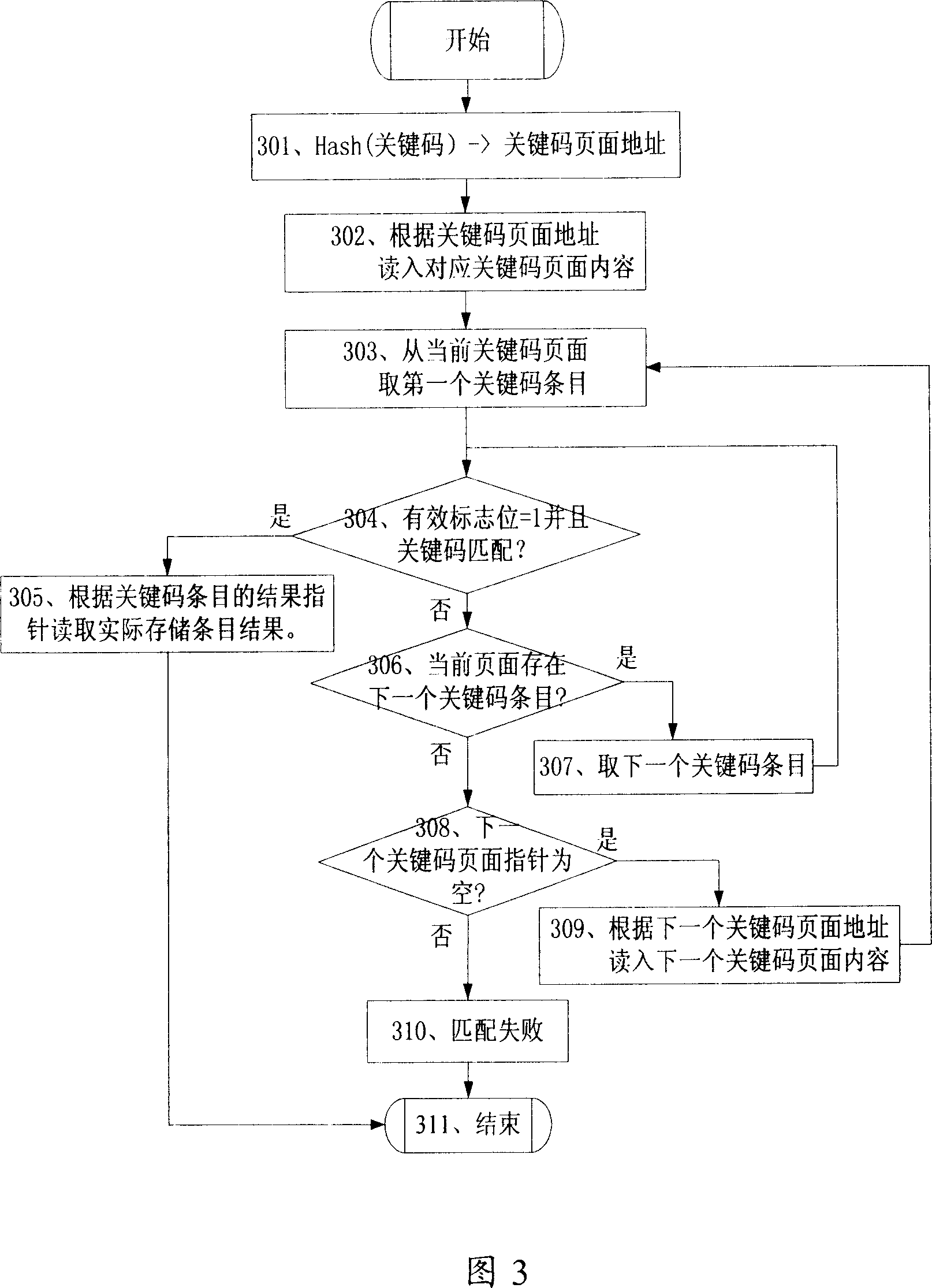
[0042] The implementation of the technical solution will be further described in detail below in conjunction with the accompanying drawings.
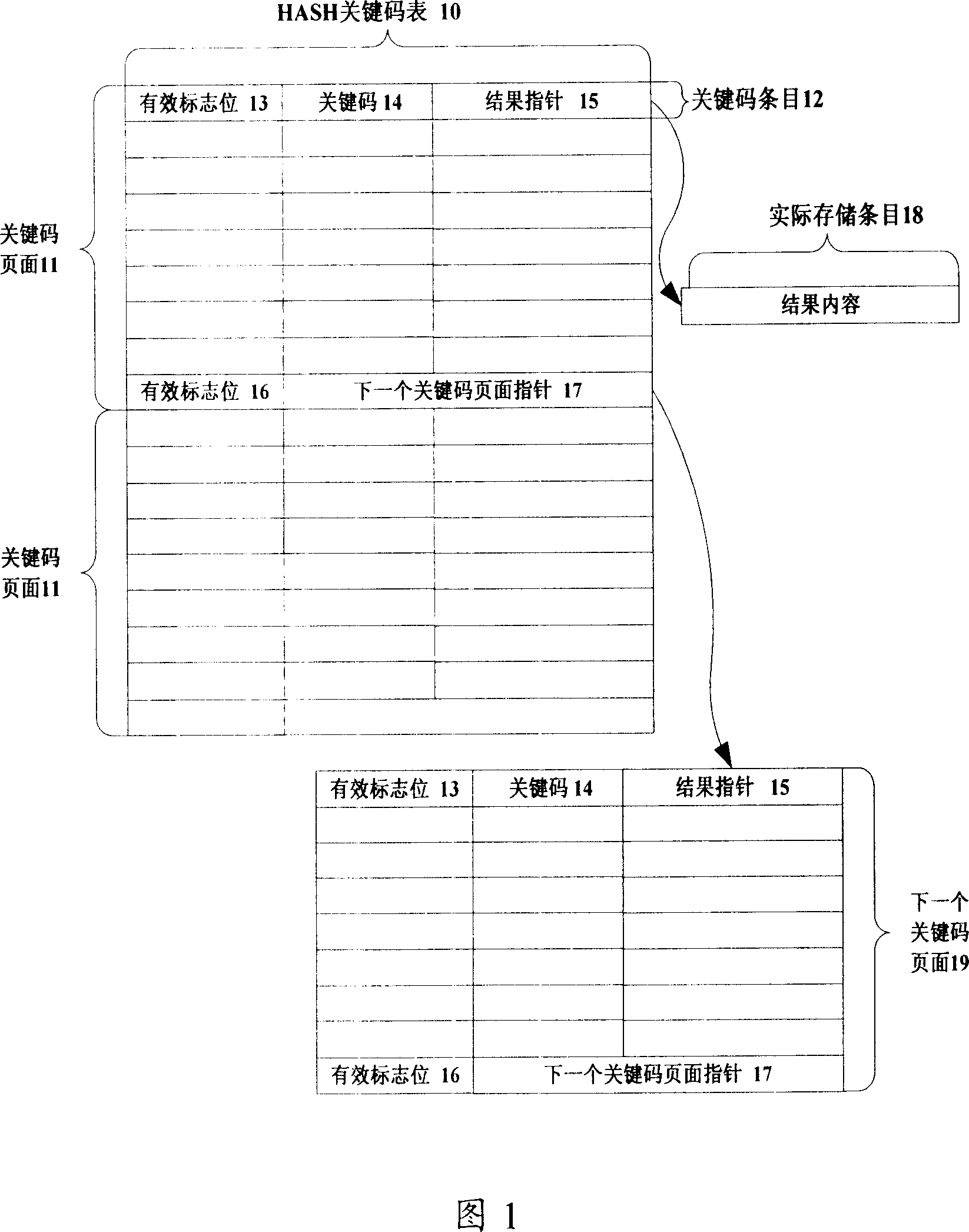
[0043] As shown in Figure 1, the data structure that the improved HASH method of the present invention applies comprises:
[0044] HASH key code table 10: a storage space table composed of a series of HASH key code pages 11.
[0045] Key code page 11: it is a memory block storing information such as a series of key codes, including a certain number of key code entries 12 and pointers 17 pointing to the next key code page. In this embodiment, it is assumed that a key code page 11 contains 8 key entry.
[0046] Key code entry 12: contains effective flag bit 13, key code 14 and result pointer 15.
[0047] Valid flag bit 13: indicates whether the current key code entry is valid, 0 indicates that the current key code entry is invalid, and is an idle entry, and 1 indicates that the current key code entry is valid.
[0048] Key code 14: sto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com