Network authorization method
A technology of network authentication and authentication equipment, applied in the network field, can solve problems such as hidden dangers of network resource security, uncontrollable resource access rights, loss of campus network management departments, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
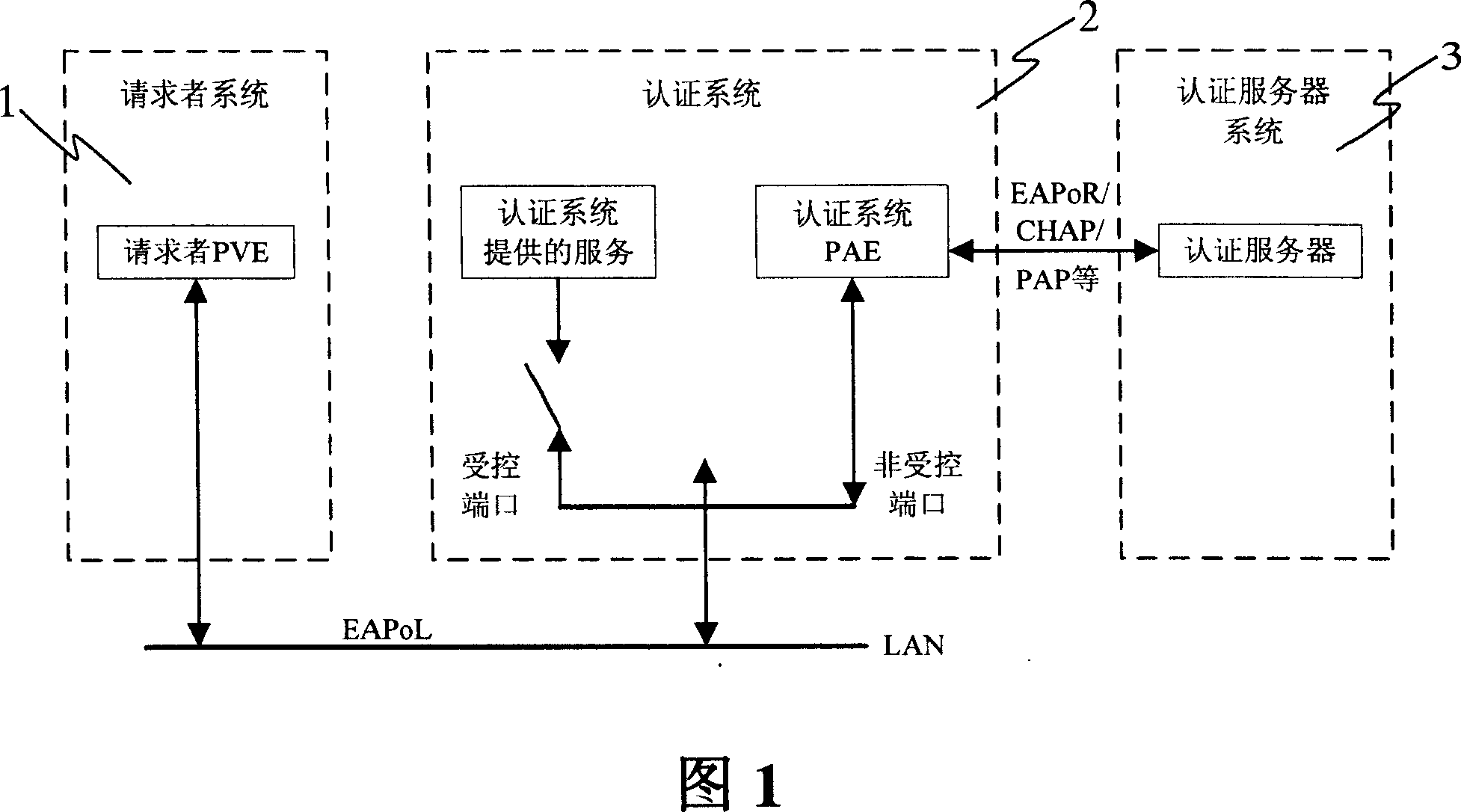
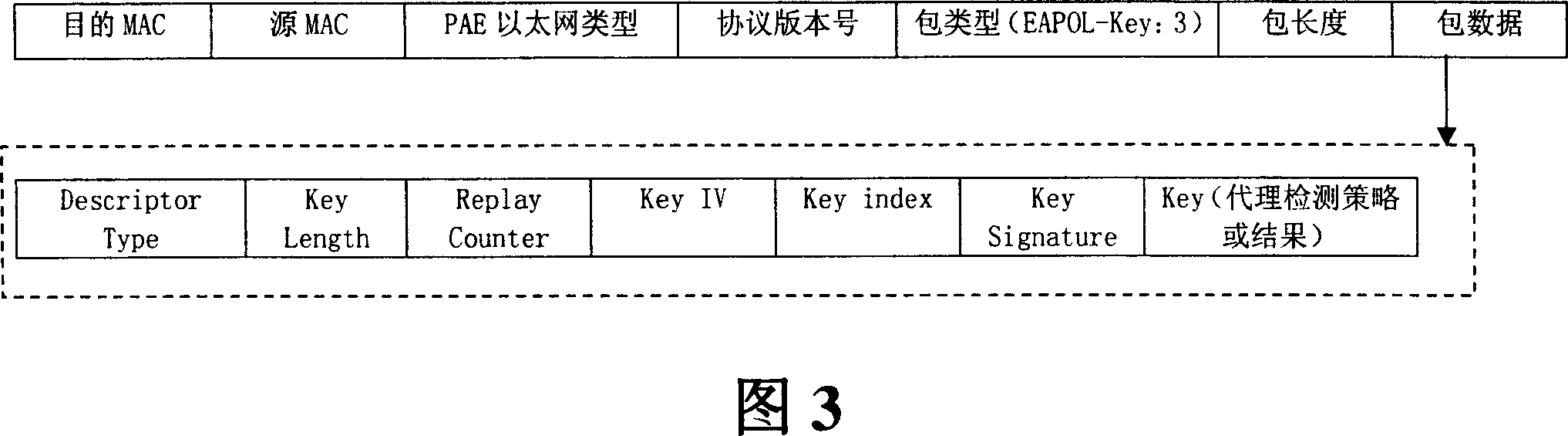
[0050]FIG. 3 is a schematic diagram of the format of an EAPoL (Extensible Authentication Protocol over Local Area Network) packet and an EAPoL-Key (keyword of the Extended Authentication Protocol over Local Area Network). EAPoL packet consists of destination MAC address, source MAC address, Ethernet PAE packet type (PAE packet value is 2), EAP protocol version number (0x01), packet type (as shown in Figure 4, this field is used to indicate packet The transmitted data type, such as the transmitted data type is EAP-Key (extensible authentication protocol key type), value 3), packet length (not including the header data of the packet) and packet data and other fields. As shown in Figure 3, the packet data among the present invention is filled by the data format of EAPoL-Key: Descriptor Type (descriptor type: adopt RC4 encryption as Key data, then take value 1), Key Length (keyword data length) , Replay Counter (retransmission counter), Key IV (keyword random data), Key index (key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com