Certifying method and system
An authentication method and key technology, which is applied in the field of authentication systems, can solve problems such as reducing security, and achieve the effect of ensuring security and reducing hardware costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
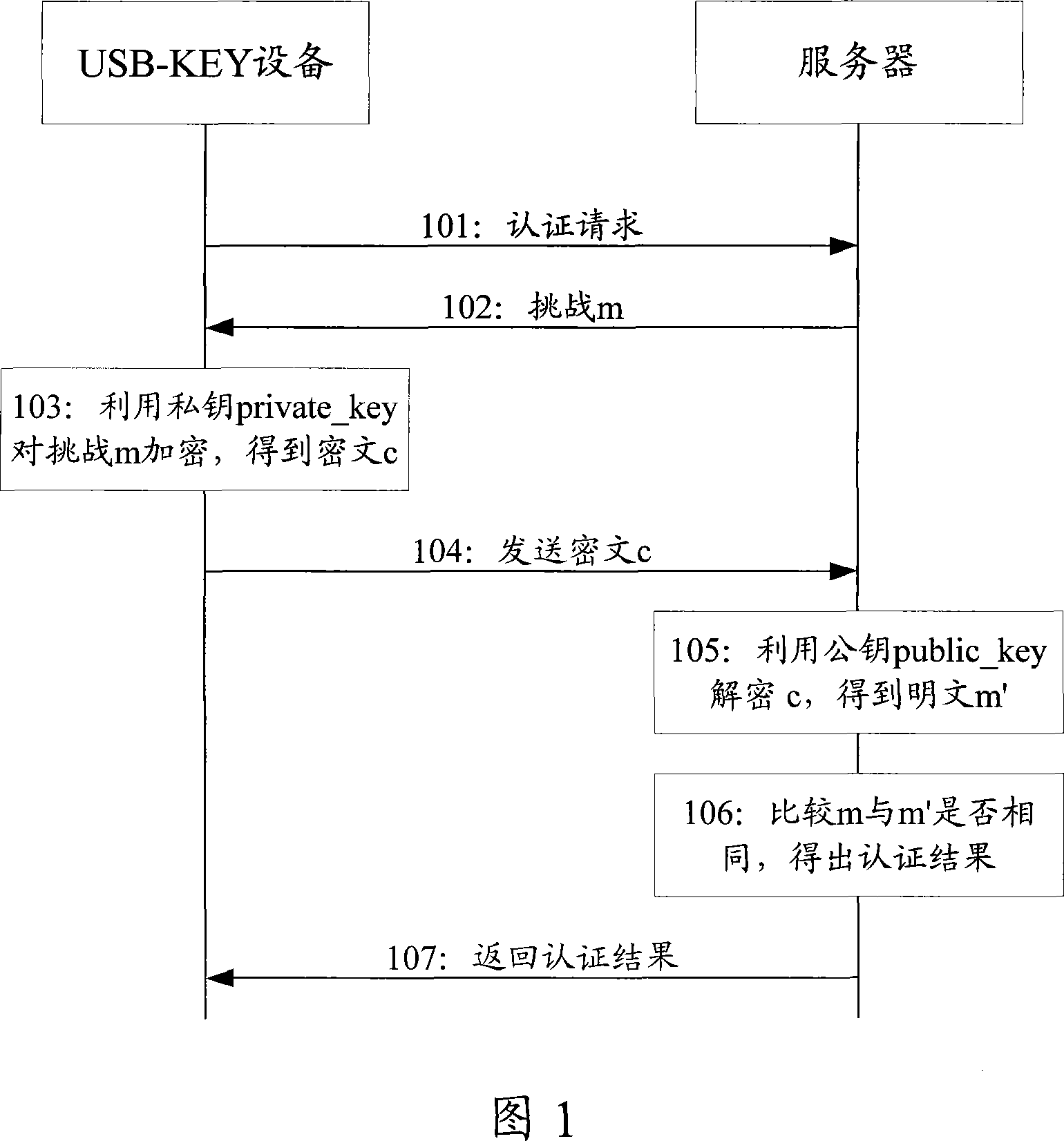
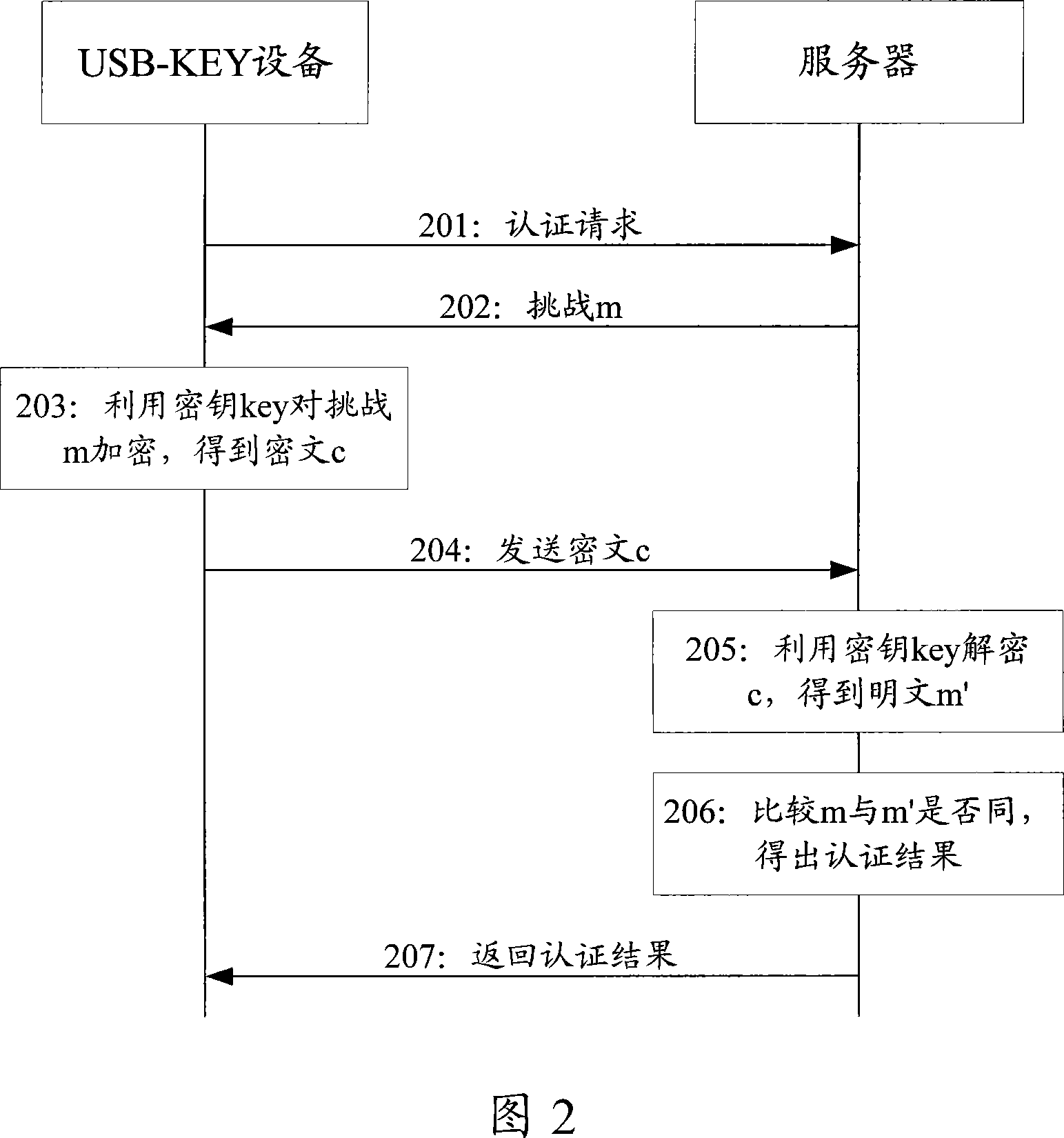
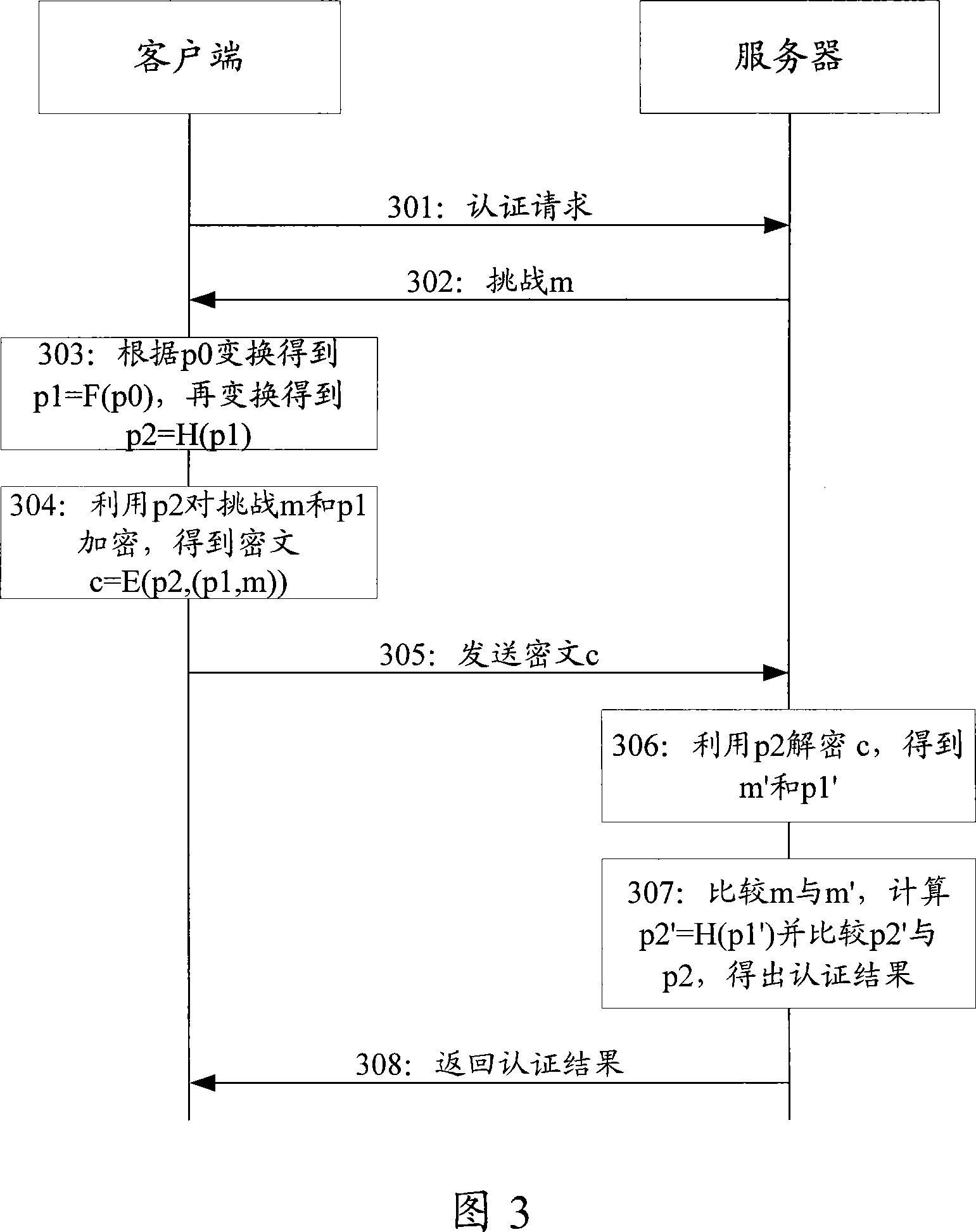
[0045] In order to make the purpose, technical solution and advantages of the present invention clearer, the following examples are given to further describe the present invention in detail.
[0046] In the embodiment of the present invention, for the key p0, a general transformation function y=F(x) is used to transform p0 to obtain p1=F(x), and then a single-phase hash function y=H(x) is used Transforming p1 yields p2=H(p1).
[0047] Among them, the general transformation function y=F(x) only needs to ensure that there is one and only one y corresponding to one x, such as y=x, y=x 3 Wait.
[0048] The characteristic of the one-way hash function y=H(x) is that y can be obtained through x, but x cannot be restored through y. For example, currently general message digest algorithm (MD5), secure hash algorithm (SHA1), etc. For a single-phase hash function, the situation in which two different xs generate the same y is called "collision". Since the probability of collision in p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com