Random access method of cellular wireless communication system
A communication system and random access technology, applied in the field of communication, can solve the problems of not knowing the timer protection time of high-level protocols, increasing processing complexity, etc., and achieve the effects of reducing signaling burden, reducing complexity, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
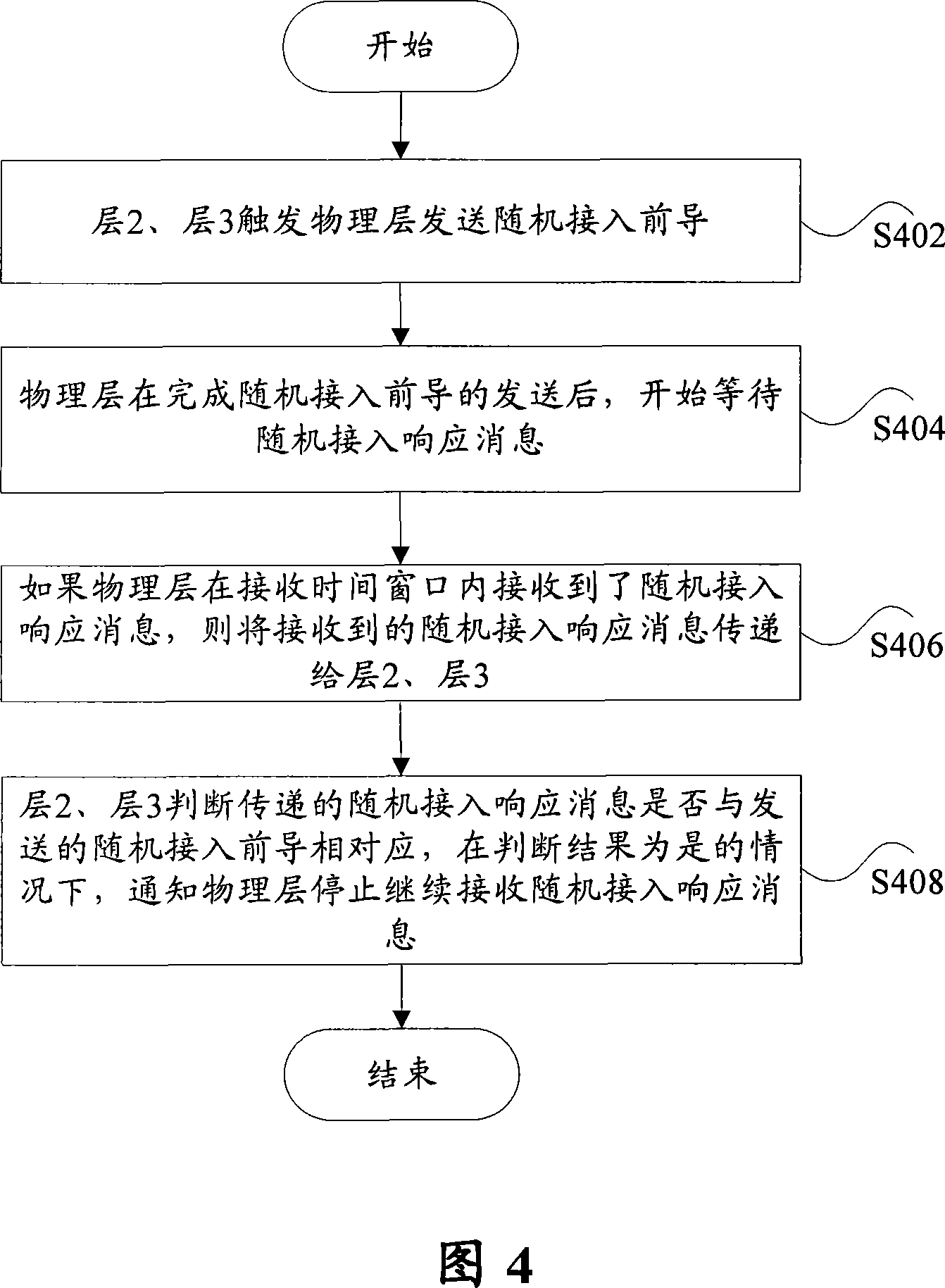
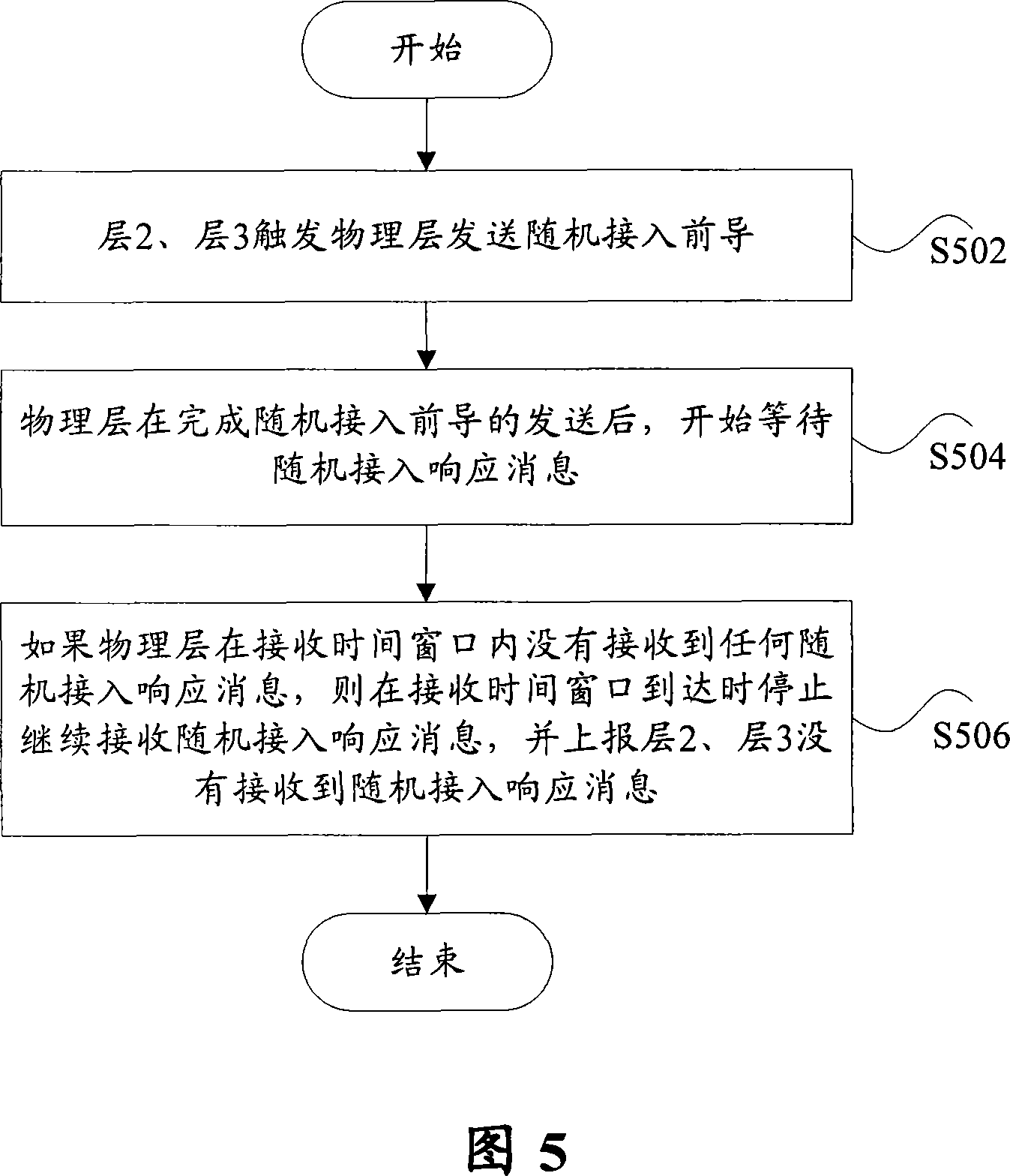
[0036] Example 1: The physical layer receives a random access response message within the receive time window
[0037] As shown in Figure 4, including the following processing:
[0038] Step S402, layer 2 and layer 3 (for example, MAC layer) trigger the physical layer to send the random access preamble;
[0039] Step S404, after the physical layer finishes sending the random access preamble, it starts to wait for the random access response message;
[0040] Step S406, if the physical layer receives the random access response message within the receiving time window, then transfer the received random access response message to layer 2 and layer 3;
[0041] In step S408, layers 2 and 3 judge whether the transmitted random access response message corresponds to the sent random access preamble, and if the judgment result is yes, notify the physical layer to stop receiving the random access response message.
[0042] In the above process, if the physical layer receives multiple r...
example 2
[0044] Example 2: The physical layer does not receive any random access response message within the receive time window
[0045] As shown in Figure 5, including the following processing:
[0046] Step S502, layer 2 and layer 3 (for example, MAC layer) trigger the physical layer to send the random access preamble;
[0047] Step S504, after the physical layer finishes sending the random access preamble, it starts to wait for the random access response message;
[0048] Step S506, if the physical layer does not receive any random access response message within the receiving time window, stop receiving the random access response message when the receiving time window arrives, and report that layer 2 and layer 3 have not received random access Respond to the message.
[0049] It should be noted that the start time for the physical layer to receive the random access response message and the end time for the physical layer to send the random access preamble may or may not be the sa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com