Digital cryptographic key protection method
A digital key and key technology, applied in electrical components, transmission systems, etc., can solve the problems of cumbersome key management, unguaranteed key security, and consumption of system resources and manpower
Inactive Publication Date: 2010-12-01
ZTE CORP
View PDF2 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
1. Key management is cumbersome
In some application scenarios where a large number of files need to be encrypted, the negotiation of many keys and algorithms or email transmission will greatly consume system resources and manpower;
2. It is difficult to update the key
In some cases, such as the key being cracked, it is necessary to replace the key in a timely and effective manner, and the above method is difficult to achieve
3. Whether it is negotiating the key or the email transmission itself, there are still security issues. If hackers or intermediaries leak, the security of the key is still not guaranteed
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
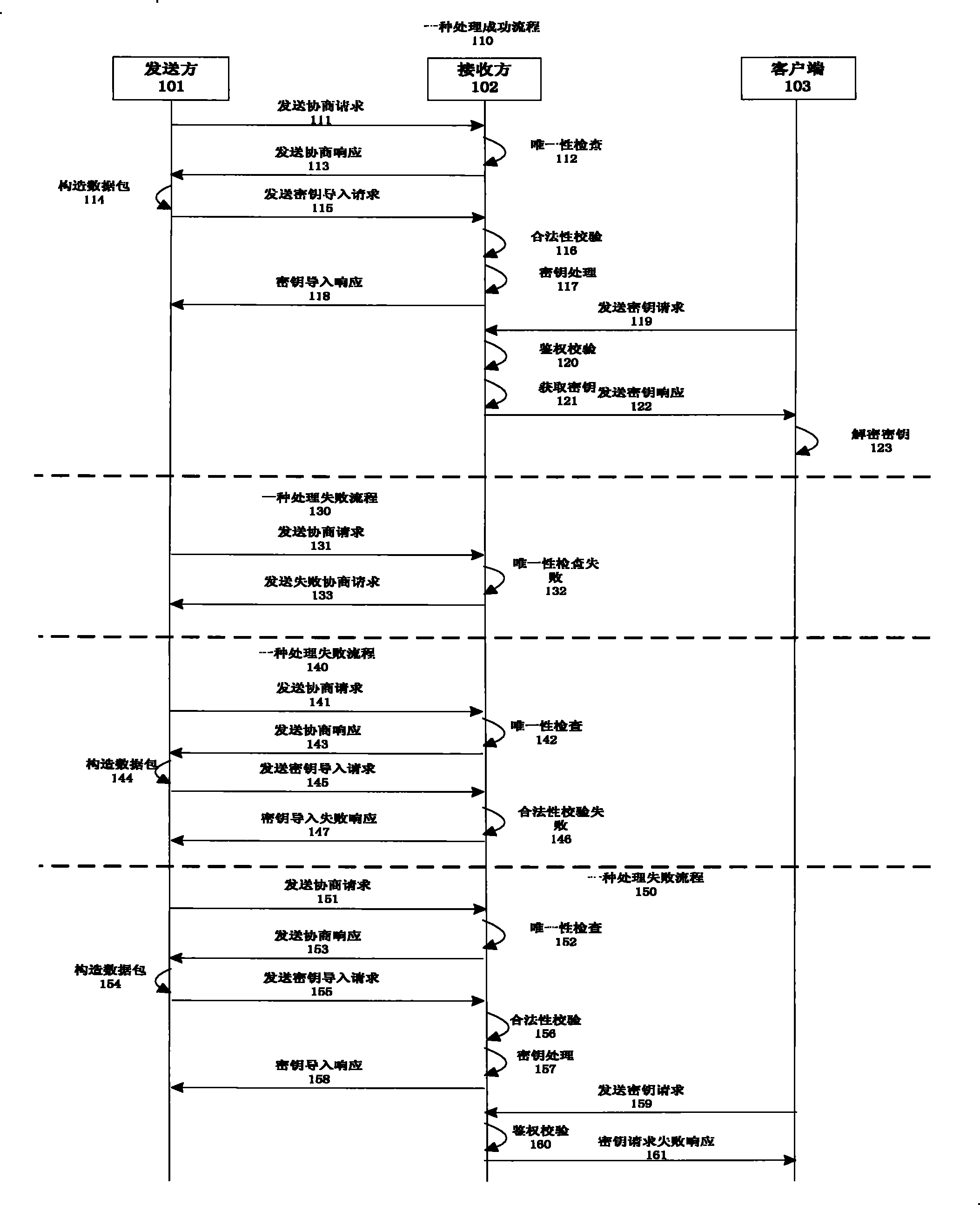
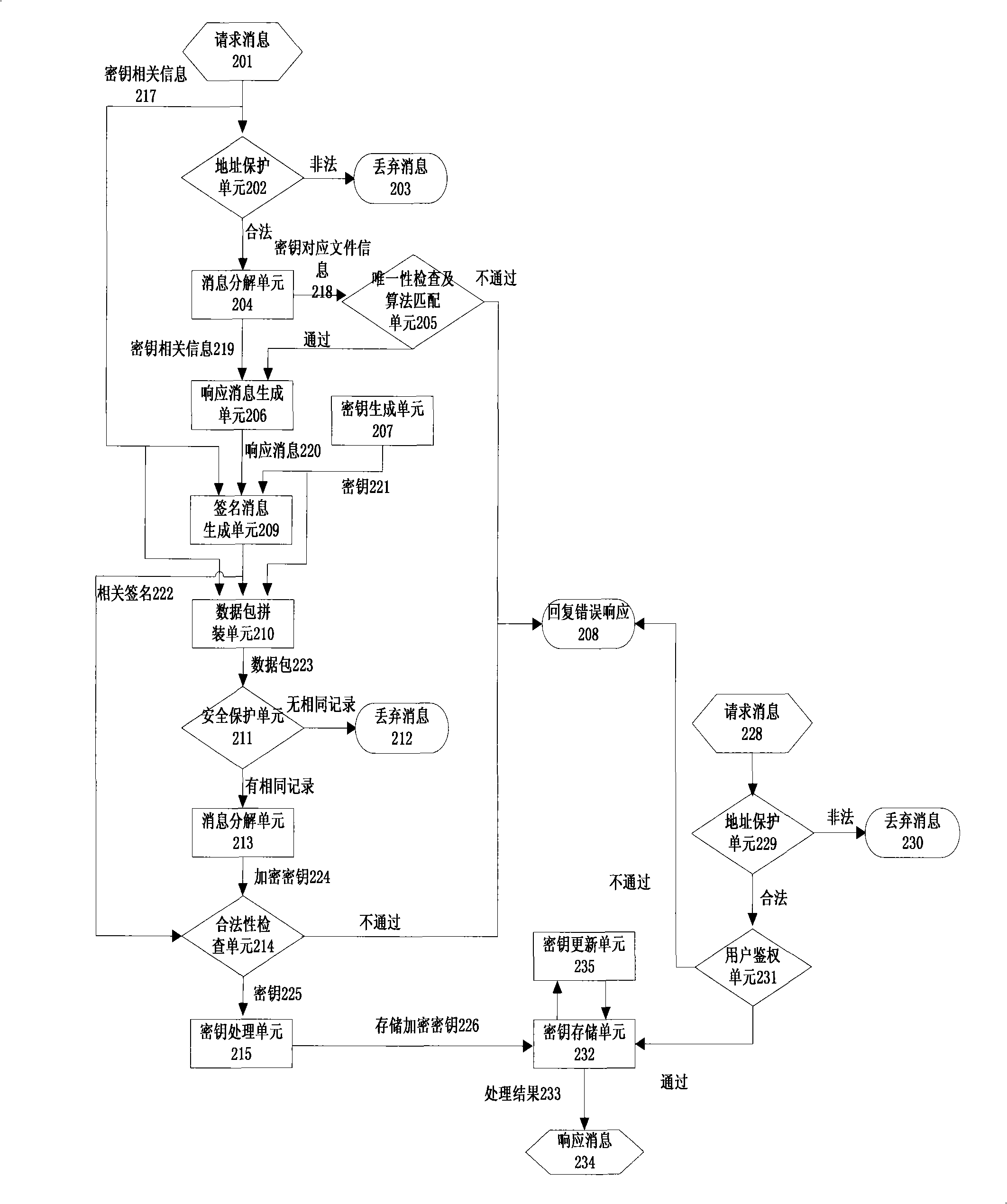
The present invention discloses a digital cryptographic key protecting method, which comprises that a server encrypts to the original cryptographic key with a receiver public cryptographic key according to the encryption algorithm, to span the encryption cryptographic key messages, a data packet is formed with the encryption cryptographic key messages and other cryptographic key related messages,a signing operation to the data packet is performed with a server private cryptographic key to span the signing messages, the data packet and the signing messages is sent to the receiver, the receiver processes the other related messages of the cryptographic key in the data packet according to the first message-digest Algorithm, to span a message-digest value which acts as a scrambling cryptographic key to encrypt to the original cryptographic key, thus a storage encryption cryptographic key is obtained, and the storage encryption cryptographic key, the related messages of the original cryptographic key and the scrambling algorithm are stored in a data base, the client end sends a cryptographic key requirement to the receiver, the receiver encrypts again to the storage cryptographic key after the storage cryptographic key is taken out, and sends the results to the client end and takes out the messages in the data base regularly, and update the scrambling algorithm and the message-digest and the storage encryption cryptographic key. The present invention improves the security of the cryptographic key input, storage, output and updating on the cryptographic key management convenience guaranteeing.
Description
A Digital Key Protection Method technical field The invention relates to the field of file encryption, in particular to a protection method in the whole life cycle of inputting, storing, outputting and updating encryption keys. Background technique With the development of broadband Internet technology and the continuous improvement of information security requirements, there is an urgent need for key security processing technology, including key transmission, storage and update processing methods. These technologies can effectively prevent malicious attacks by hackers or middlemen, thereby reducing the possibility of key leakage and protecting the rights and interests of users. In order to be able to decrypt the data correctly, there are currently two common methods: first, before sending the key, the sender and the receiver negotiate the relevant parameters, the sender uses the key to encrypt the file and then sends the encrypted file to the receiver, and the receiver T...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L29/06
Inventor 何康许军宁吕吉
Owner ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com