Digital cryptographic key protection method
A digital key and key technology, which is applied in the transmission system, electrical components, etc., can solve the problems that key security cannot be guaranteed, key update is difficult, key management is cumbersome, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
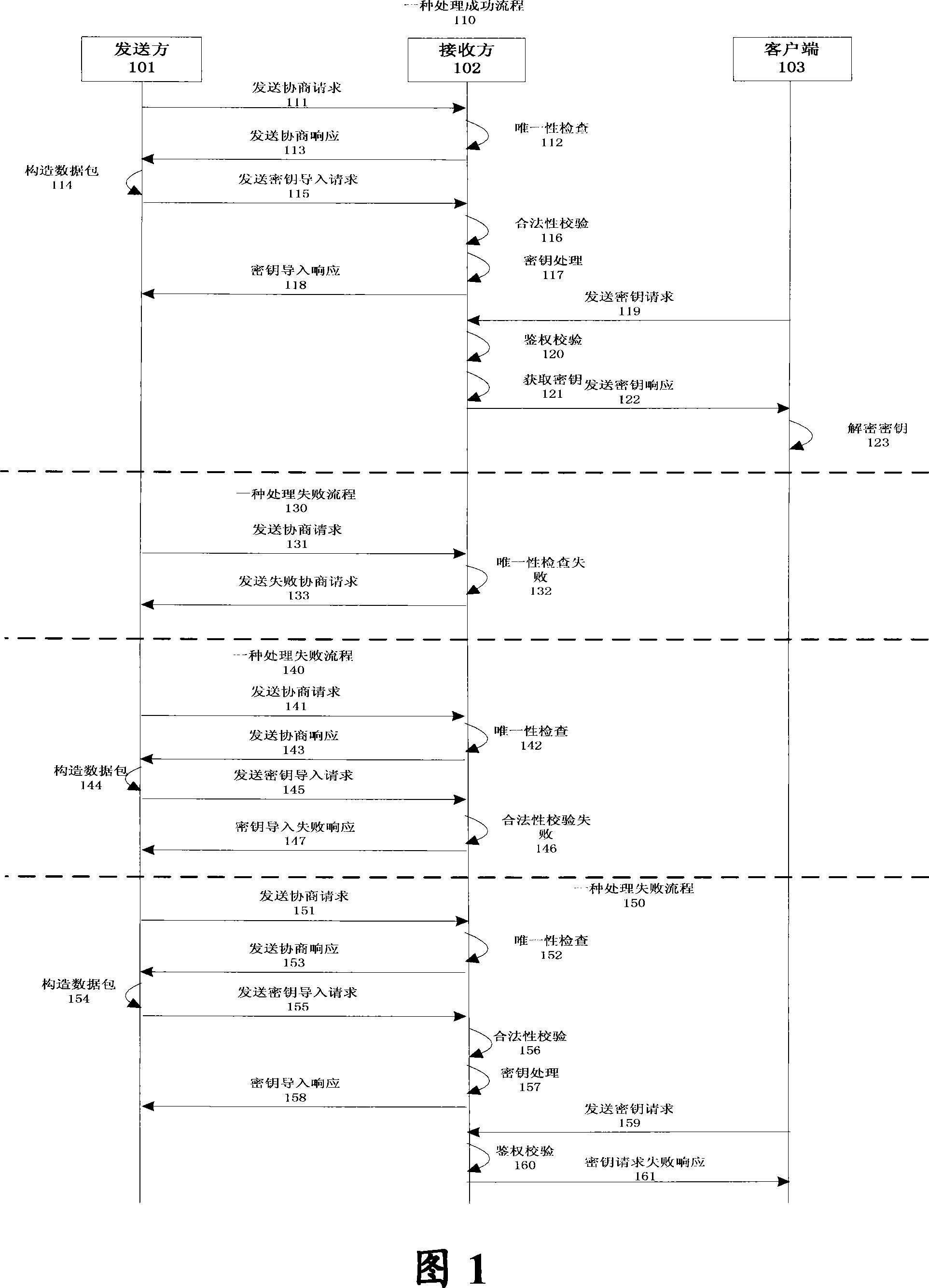
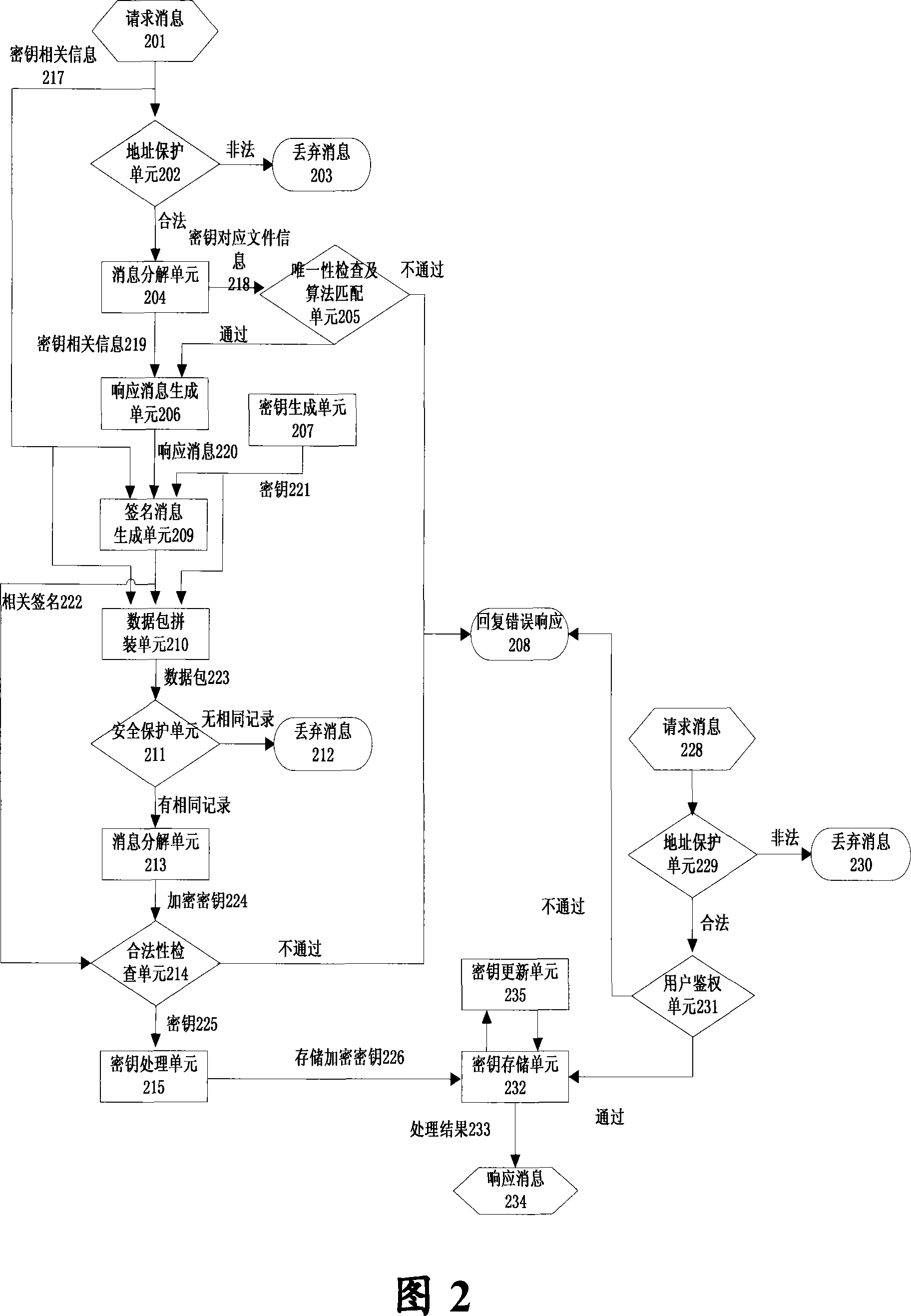
[0039] The present invention provides a digital key protection method, which can be applied to the technical field of network communication security, and improves the security issues of related key input, storage, output and update. Specific embodiments are described in detail below, but not as a limitation to the present invention.
[0040] A kind of digital key processing method of the present invention is described below in conjunction with accompanying drawing and embodiment, the digital certificate described here refers to the digital certificate that conforms to the X.509 specification standard; The corresponding private key file; the key mentioned here refers to the key in the string format that needs to be transmitted.
[0041] As shown in Figure 1, the key processing method in Embodiment 1 of the present invention involves two logical entities:
[0042] The sender 101, the sender 101 sends an algorithm negotiation request and a key import request to the receiver 102 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com