Movable memory apparatus monitoring method and apparatus for
A mobile storage device and mobile device technology, applied in computer security devices, preventing unauthorized use of memory, instruments, etc., can solve problems that cannot solve fundamental problems, and achieve the effect of solving leaks and great flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
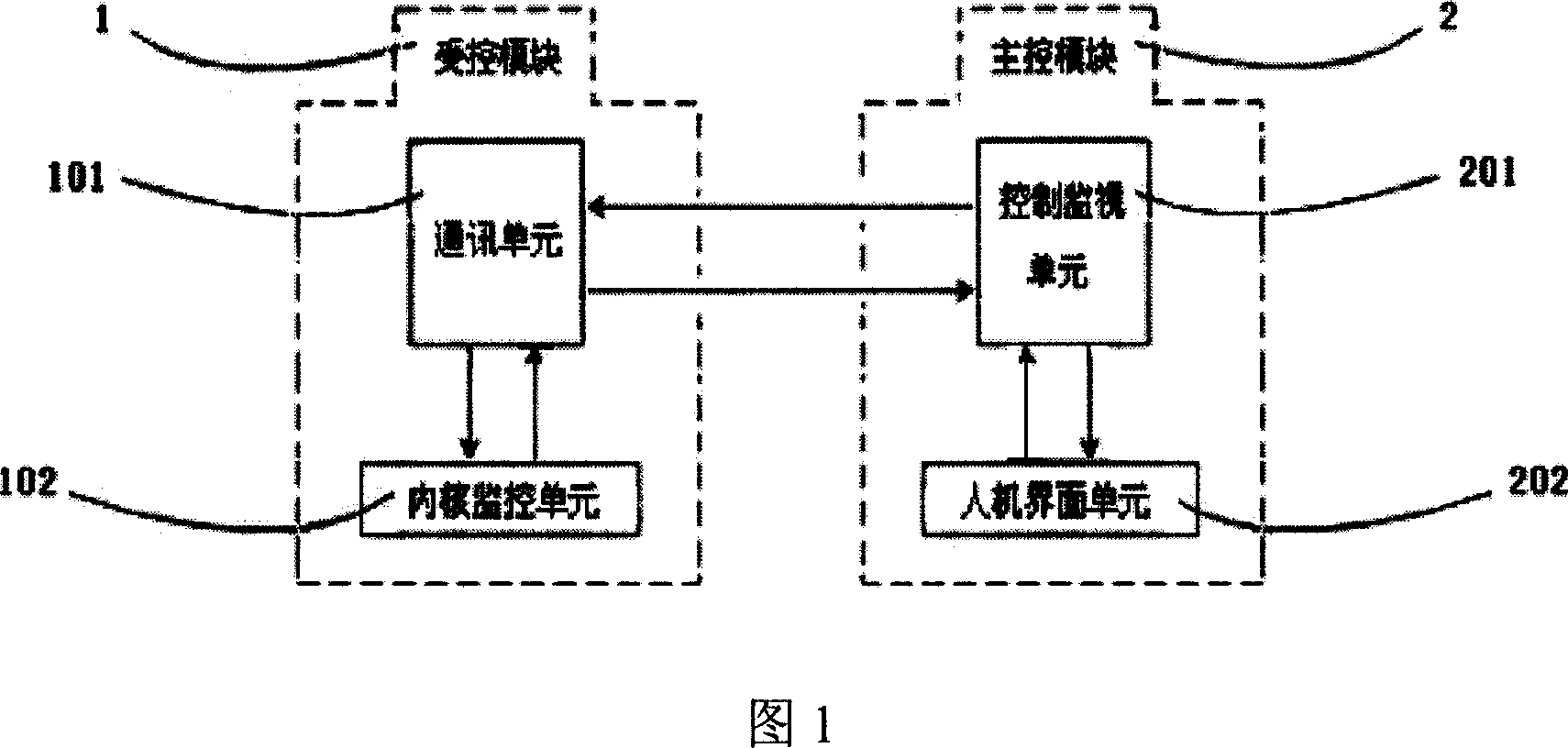
[0017] As shown in Figure 1, a mobile storage device monitoring device includes: a main control module 2 and a controlled module 1, the main control module 2 sends a control command to the controlled module 1, and the controlled module 1 sends a control command to the controlled module 1 The main control module 2 returns monitoring information.
[0018] Wherein, the main control module 2 includes a man-machine interface unit 202 and a control monitoring unit 201 , and the controlled module 1 includes a communication unit 101 and a kernel monitoring unit 102 .
[0019] The man-machine interface unit 202 generates a control command and displays monitoring information, the control and monitoring unit 201 transmits the control command to the communication unit 101, and receives the monitoring information transmitted from the communication unit 101, and the communication unit 101 sends the monitoring information to the communication unit 101. The core monitoring unit 102 transmits ...
no. 2 example
[0021] A monitoring method for monitoring mobile equipment using the above device, comprising the following steps:
[0022] Step 1, intercepting the data read or written by the application through the file system;
[0023] Step 2, judging whether the reading location or writing location of the above-mentioned data is a mobile device, if not, then end, if yes, then proceed to step 3;
[0024] Step 3, judging whether the above-mentioned mobile device has the corresponding read / write authority, if not, discarding the data, and if it has the corresponding authority, proceed to step 4;
[0025] Step 4, transfer the above data to its target location, and generate monitoring information.
[0026] The above-mentioned device and method can be applied to various operating systems, and each operating system provides support interfaces for expanding file system functions. Through these interfaces of the operating system, a module with a new function can be added to it, so that the new fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com