Method and system for multicast and broadcast service authentication and authorization
A multicast broadcast service and multicast broadcast technology are applied in the field of realizing multicast broadcast service authentication, which can solve the problems of wasting broadband resources, user terminal authentication and authentication failure, and user terminal being unable to access the network, etc., to prevent illegal attacks. Threats, prevention of illegal attacks, and shortened authentication time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
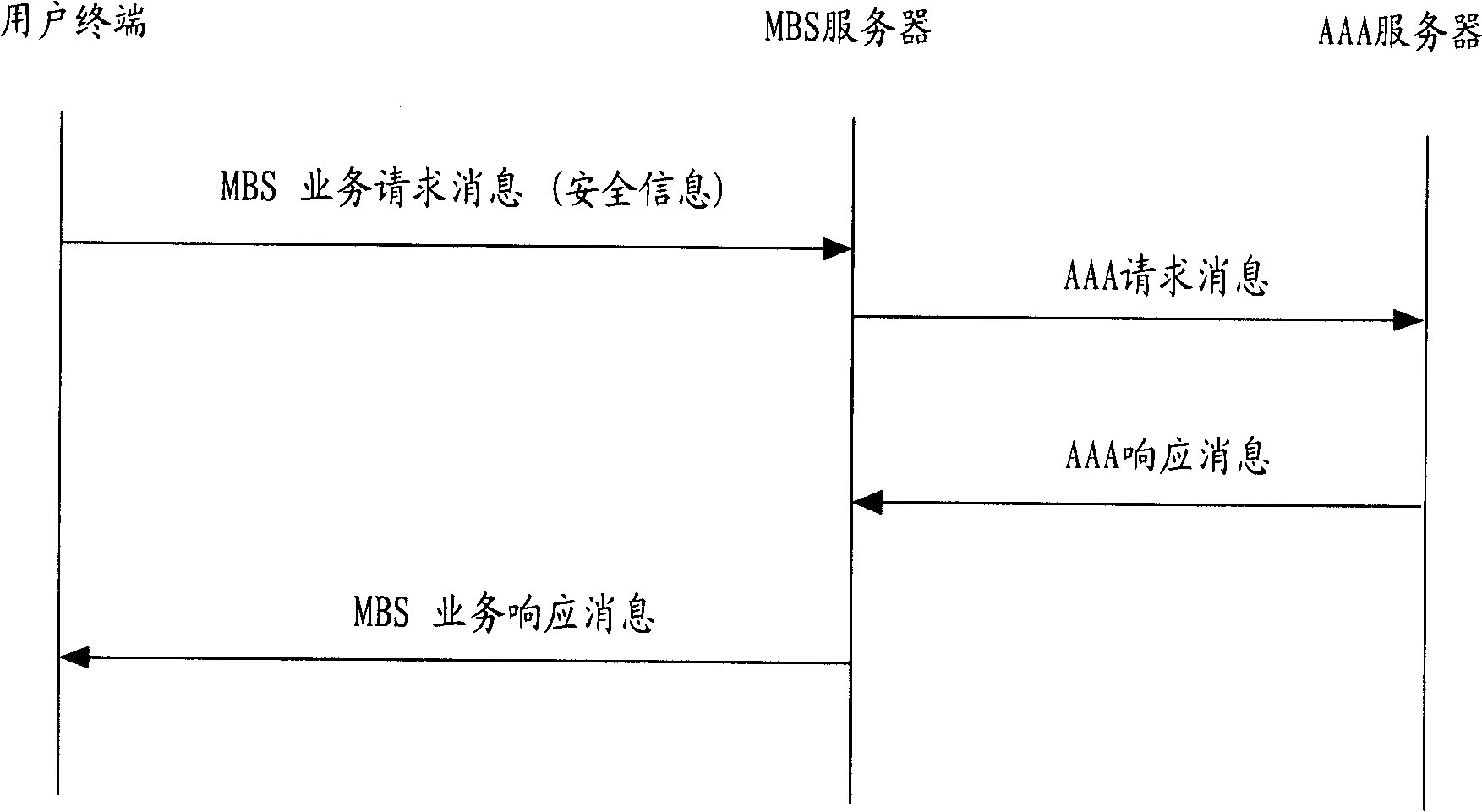
[0050] Such as figure 2 As shown, when the authentication authentication uses the AAA server, the user terminal sends the MBS service request to the MBS server, and the request includes security information for verifying the legitimacy of the identity of the user terminal;
[0051] The attribute value for preventing replay attack contained in the security information and the message authentication code for integrity authentication of the message do not affect the implementation of the present invention;
[0052] The method for generating security information is specifically as follows:
[0053] The user terminal uses the extended master session key EMSK obtained in the access authentication process to generate a multicast broadcast service root key (MBS-RK) and its context (MBS-RK context);
[0054] The AAA server uses the extended master session key obtained during the access authentication process to generate the root key of the multicast broadcast service and its context,...
Embodiment 2
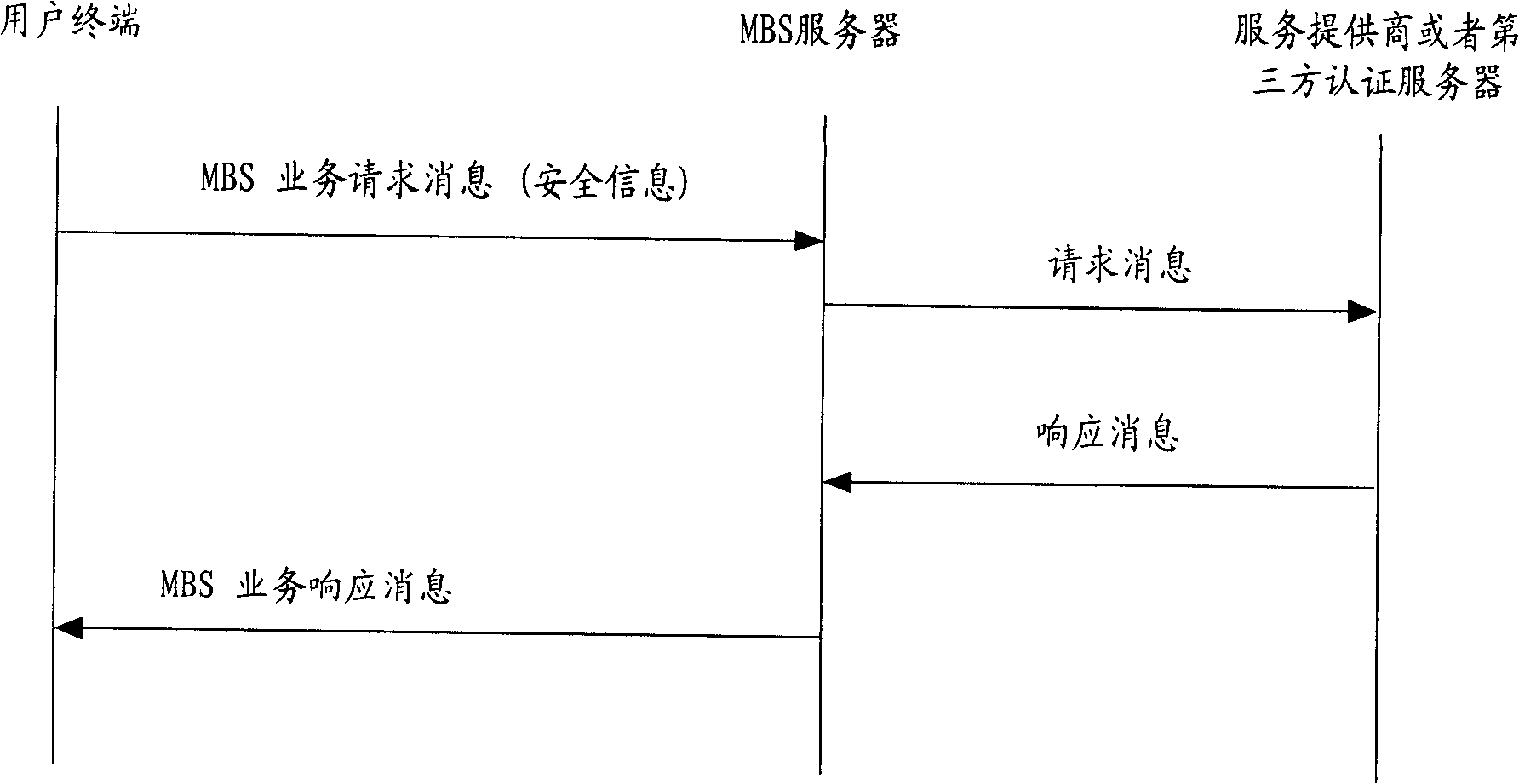
[0094] Such as image 3 As shown, the difference between this embodiment and embodiment 1 is:
[0095] When the authentication authentication user is a third-party authentication server, the key context generation method including security information is as in embodiment 1;
[0096] When the third-party authentication server sends a response message to the MBS server, the NASID is not included in the message, because the service provider or the third-party authentication and authorization server does not provide access authentication and authorization for the user's bearer network, and cannot know the user's current authenticator;
[0097] Parts that are the same as those in Embodiment 1 will not be described again here.
Embodiment 3
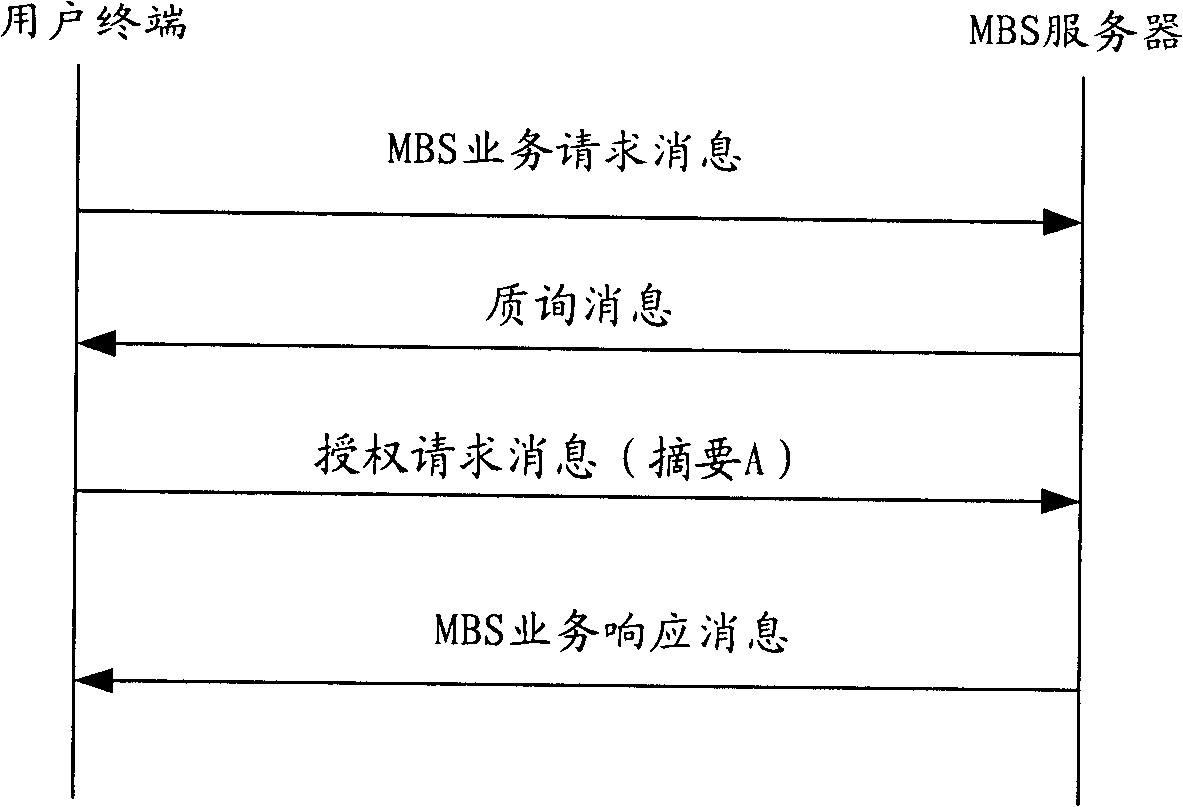
[0099] Such as figure 2 As shown, the difference between this embodiment and embodiment 1 is:
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com