Safe JTAG connection identification system and identification method
An authentication method and security technology, applied in the field of secure JTAG connection authentication system, can solve problems such as cumbersome operation and achieve the effect of simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
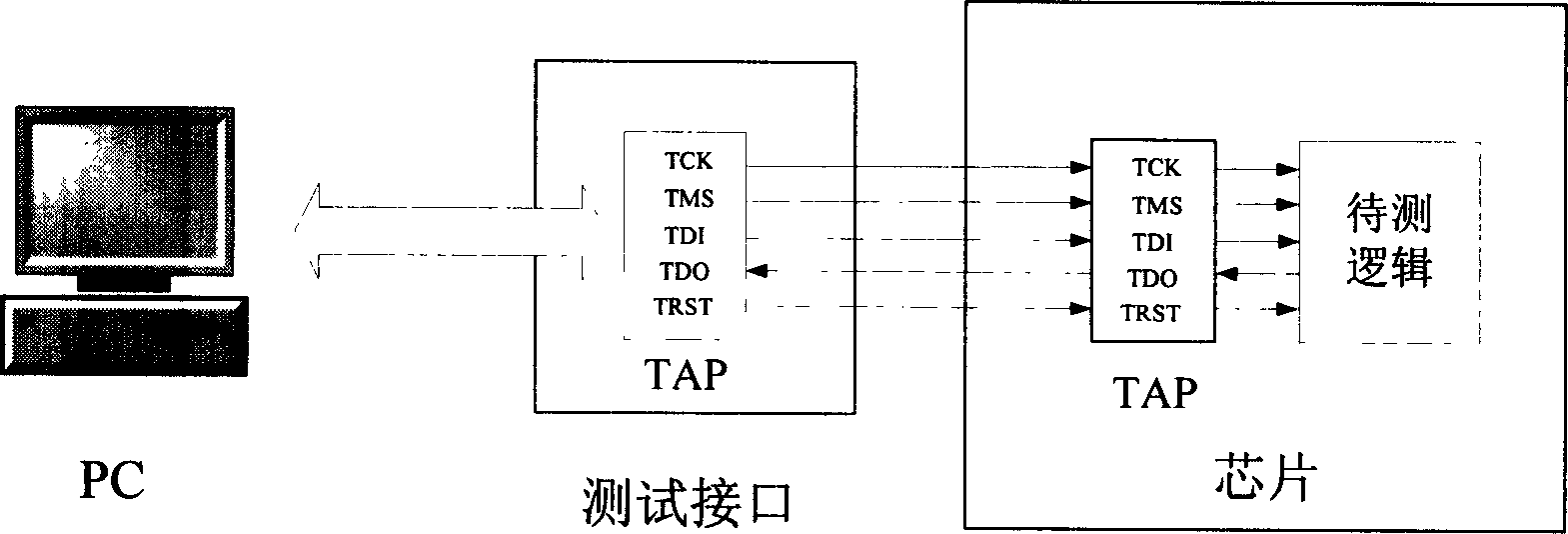
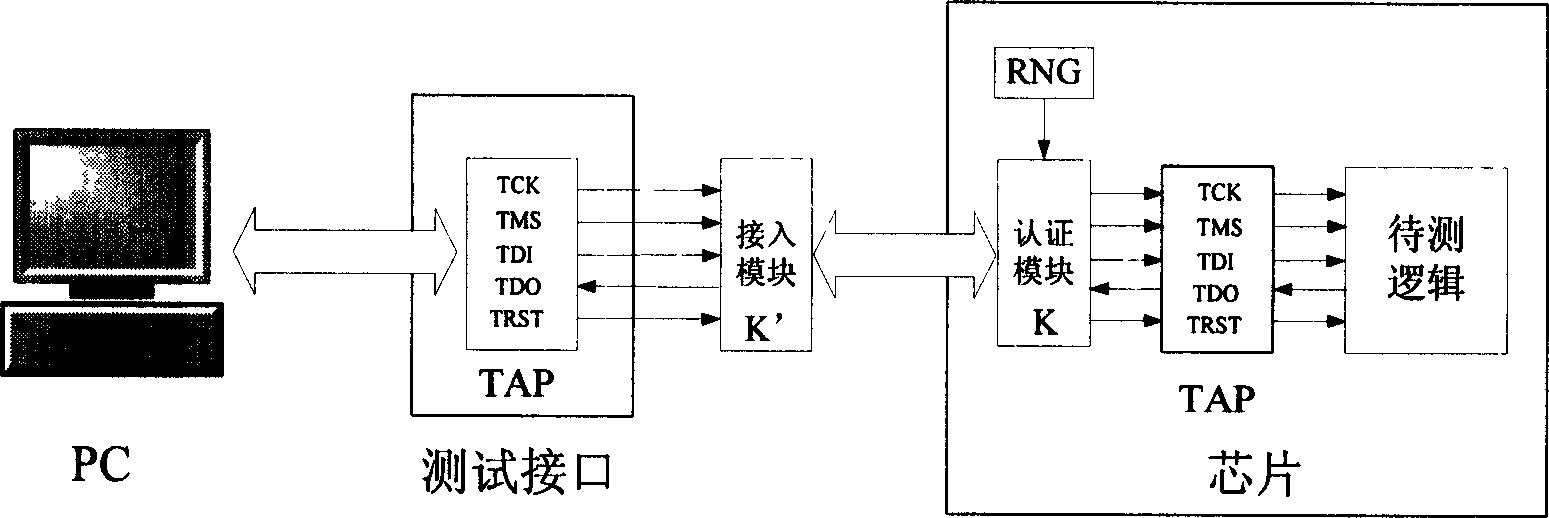
[0032] see figure 2 , which is a structural schematic diagram of a secure JTAG connection authentication system of the present invention. it is in figure 1 On the basis of the structure, two modules are added: an access module and an authentication module. Such as figure 2 As shown, the access module is placed outside the chip, and the authentication module is placed inside the chip. Both the access module and the authentication module store the same key. When the test interface is connected to the chip side, an authentication process will be carried out between the access module and the authentication module. After the authentication is passed, the authentication module will open the chip side. port, the computer can be like figure 1 Debug the chip transparently as shown.
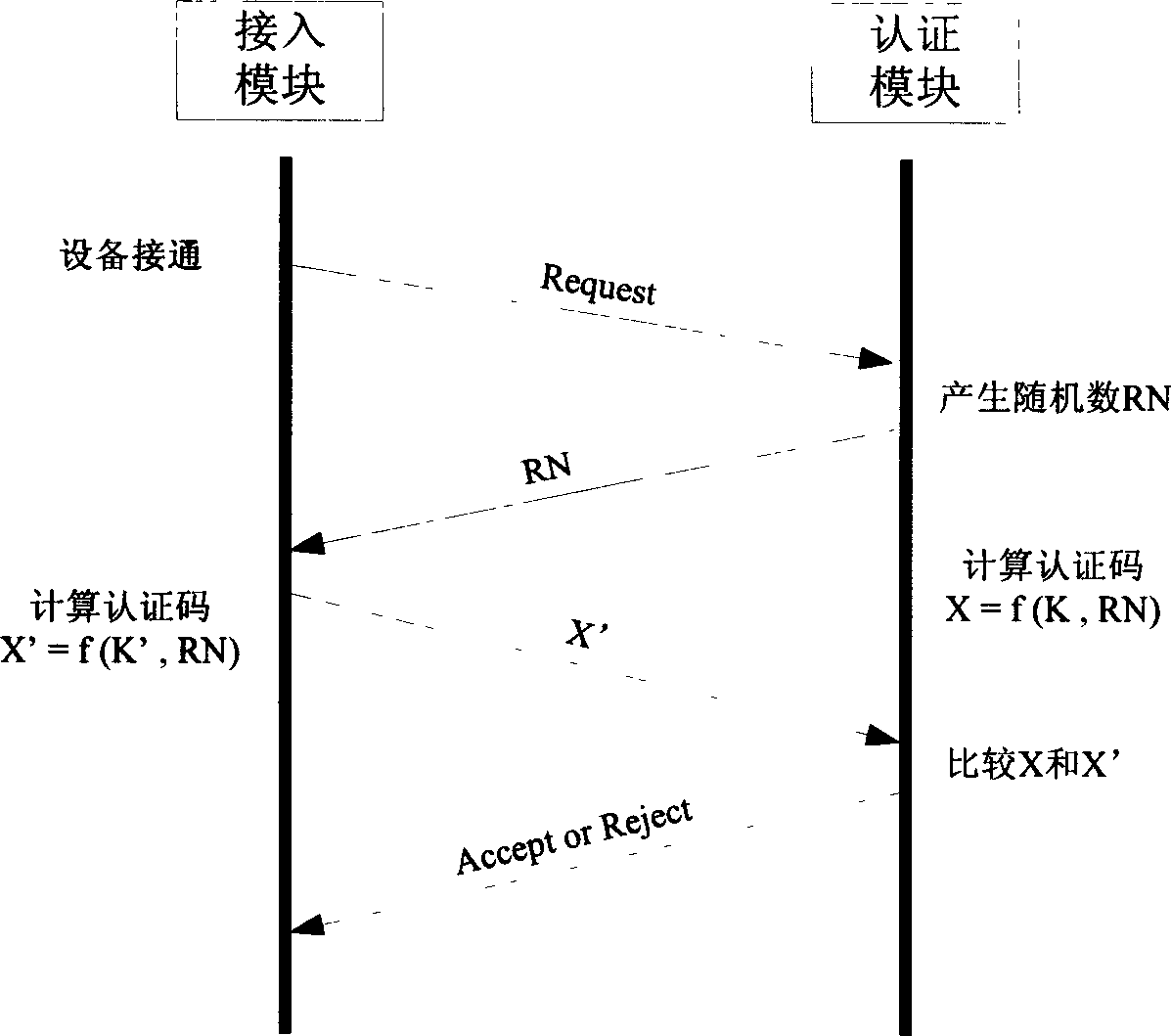
[0033] see again image 3 , it is embodiment 1 of authentication method among the present invention, and it uses authentication system as above, and concrete steps are:
[0034] Step 1: The access...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com