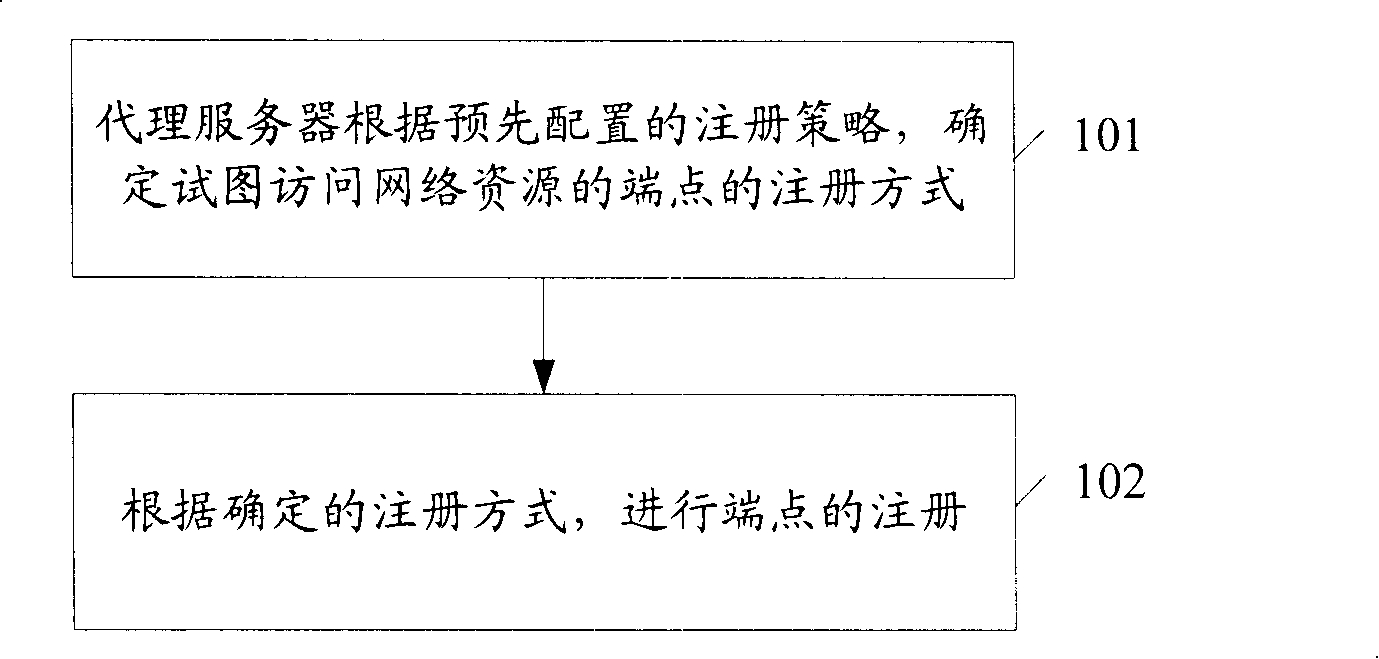
A registration method and agent server
A proxy server and endpoint technology, applied in the field of registration methods and proxy servers, can solve problems such as hindering access to network resources, heavy server load, and inability to take into account network security and high-quality service requirements, and achieve the effect of ensuring network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
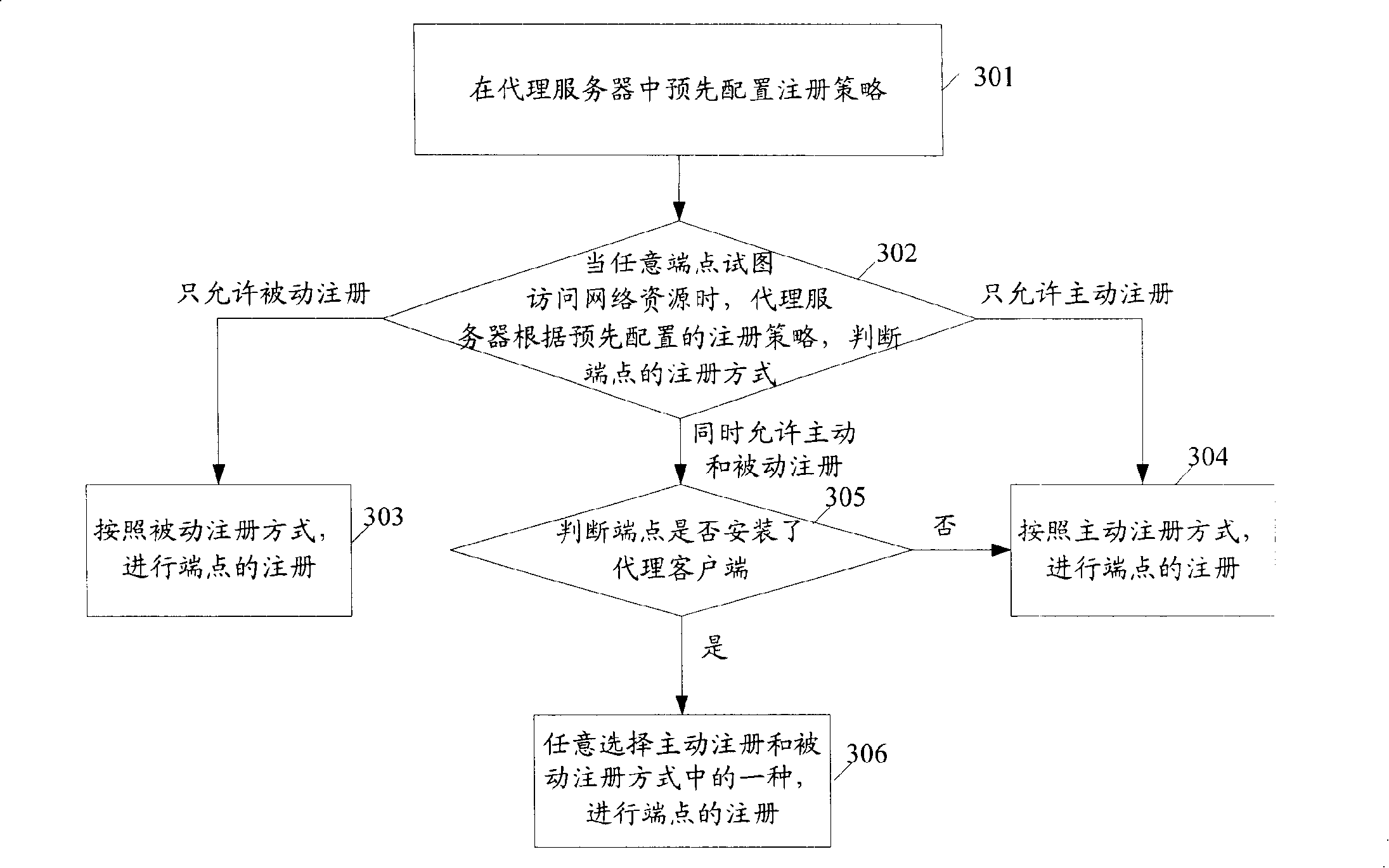
[0035] image 3 It is a specific flow chart of the registration method in Embodiment 1 of the present invention. In this embodiment, the NEA evaluation system is taken as an example to describe the specific implementation manner. Such as image 3 As shown, the method includes:
[0036] Step 301, pre-configure the registration policy in the proxy server.
[0037] In this step, the proxy server configures the registration policy mainly from the perspective of security and network processing capability, and balances the relationship between system security and network user service quality. The main method adopted is: obtain the network environment information, and set the corresponding registration method for the endpoint according to the network environment information. The network environment information may include one or any combination of the following: the security status of the area where the endpoint is located, the security requirements of the network area that the e...
Embodiment 2
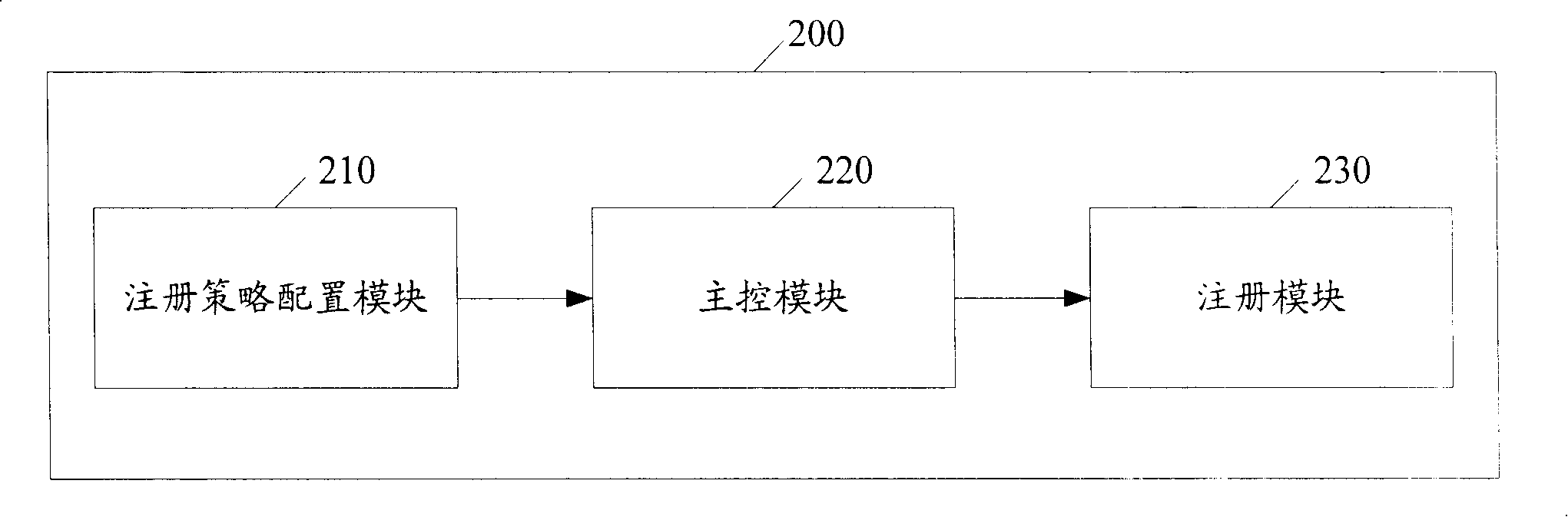
[0064] Figure 4 It is a specific structural diagram of the proxy server in Embodiment 2 of the present invention, and the proxy server can be used to implement the above registration method. In this embodiment, the specific implementation manner of the proxy server is described by taking the NEA evaluation system as an example. Such as Figure 4 As shown, the proxy server 400 includes: a registration policy configuration module 410 , a main control module 420 , a registration module 430 , and an acquisition module 440 .
[0065] In the proxy server 400, a registration policy configuration module 410 is configured to configure a registration policy. The obtaining module 440 is used to obtain network environment information, wherein the network environment information includes one or any combination of the following: the security status of the area where the endpoint is located, the security requirements of the network area to be accessed by the endpoint, the system load of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com