Method for realizing of Hach coprocessor
A coprocessor and processor technology, applied in the field of information security and encryption, can solve problems such as leakage and loss, and achieve the effect of flexible application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The specific implementation of the present invention is basically consistent with the structure and principle set forth in the description of the present invention. The present invention will be described in detail below in conjunction with the accompanying drawings.
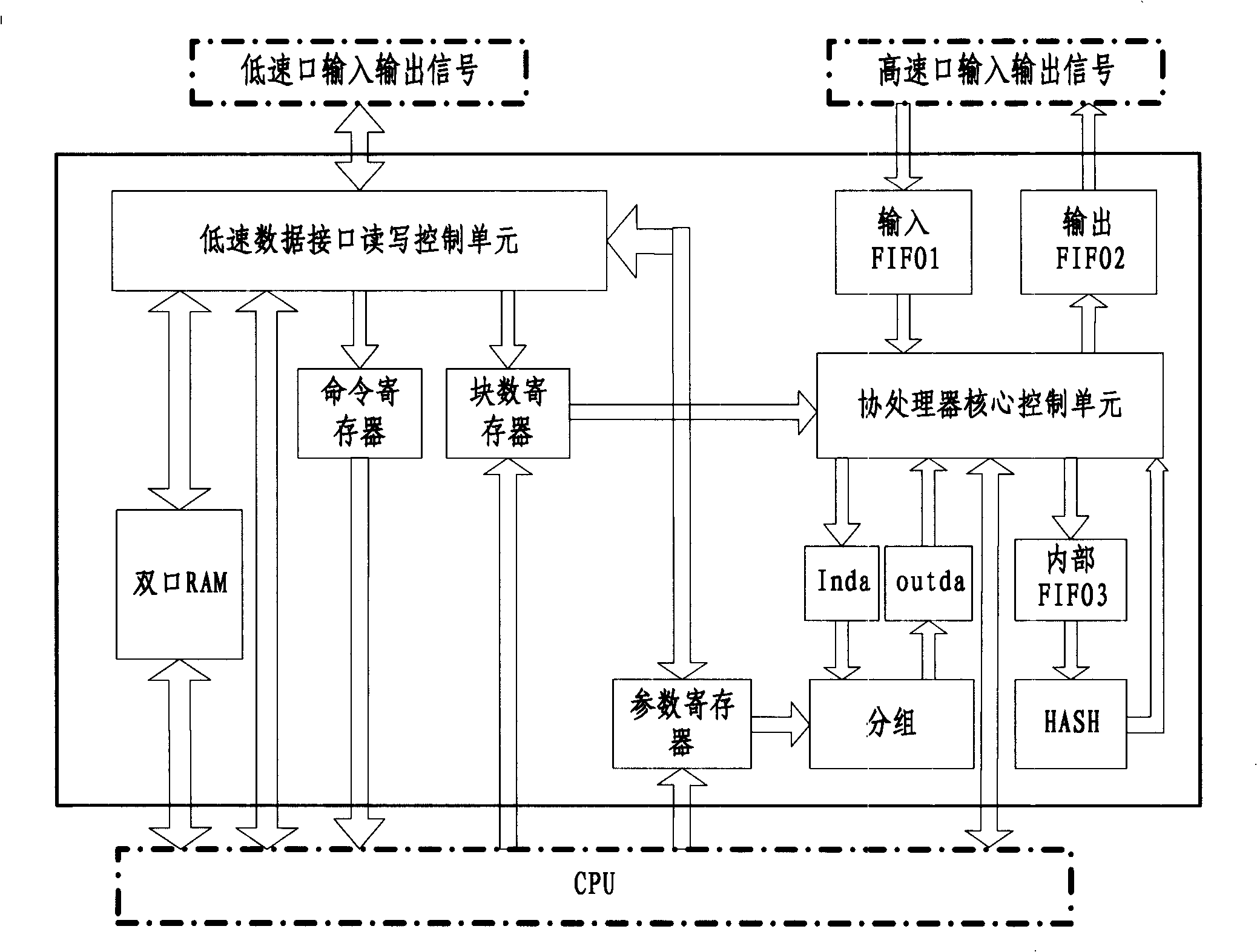
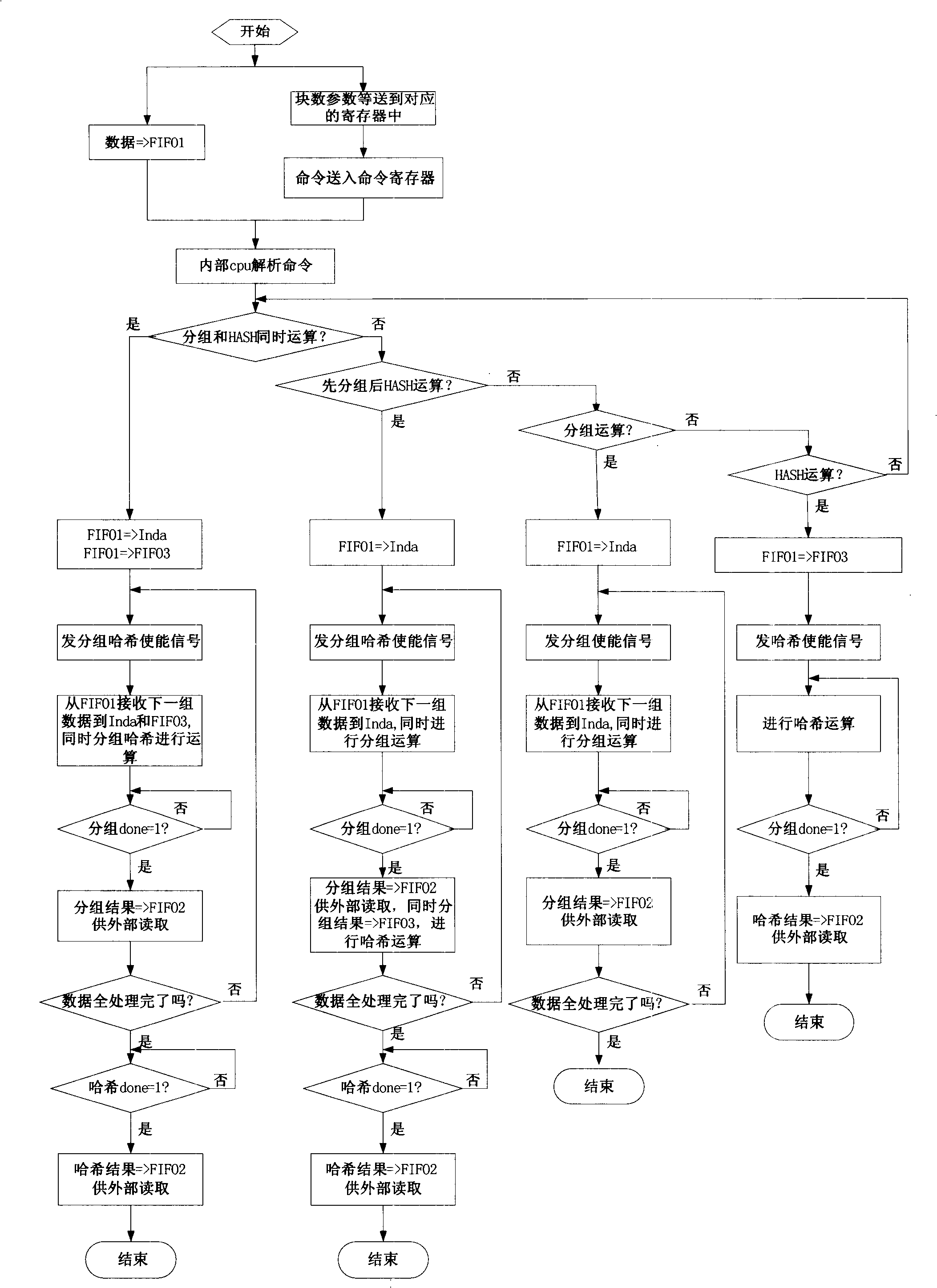
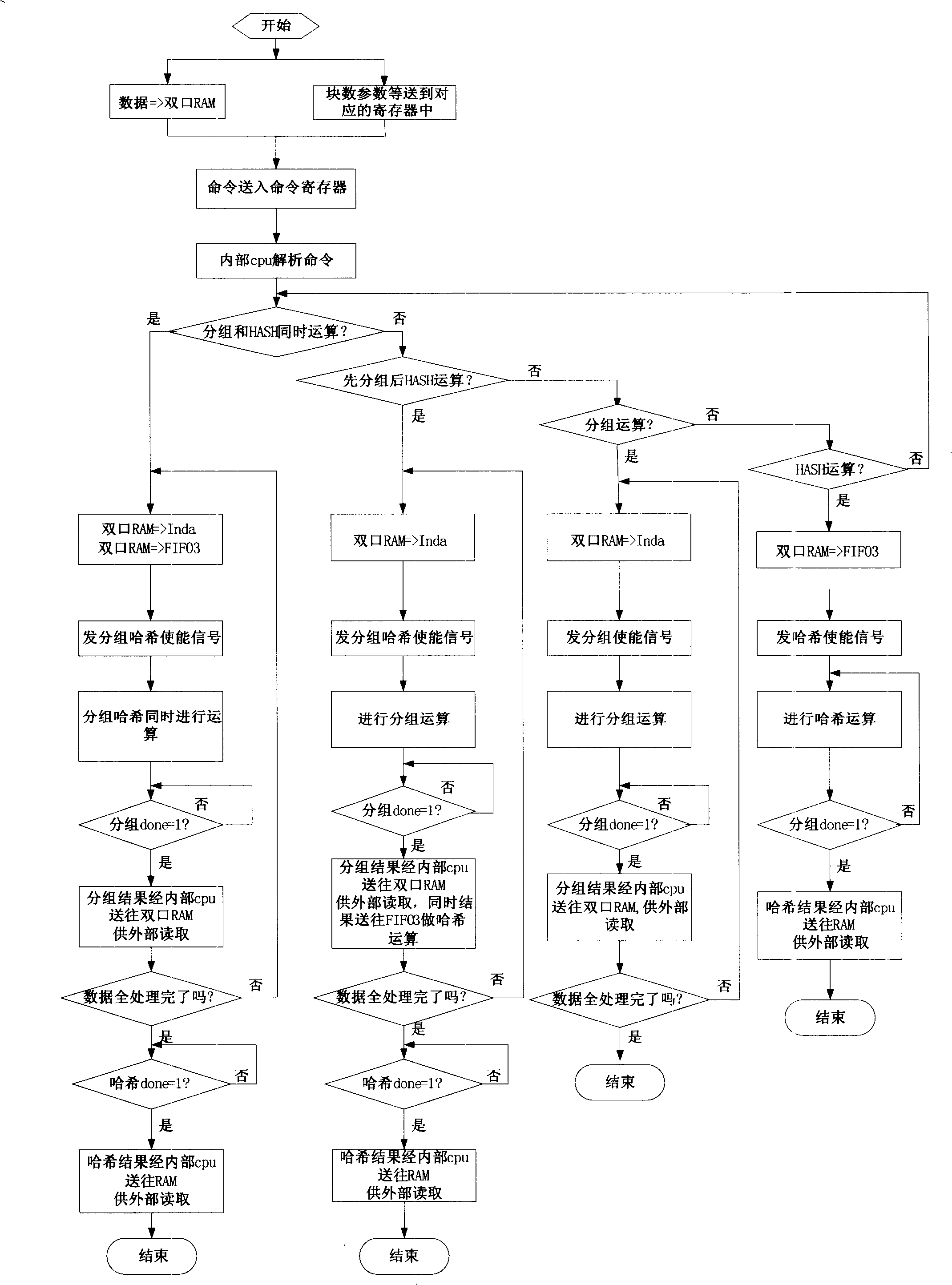
[0069] The invention discloses an implementation of a packet hash coprocessor, the hardware components of which include: a packet operation unit, a hash operation unit, a low-speed data interface read and write control unit, and a high-speed data interface processing unit (by input FIFO1 and output FIFO2 Composition), coprocessor core control unit and a dual-port RAM, internal FIFO3, command register, block number register, parameter register, group input buffer register Inda and group output buffer register Outda, etc.
[0070] Please refer to the attached figure 1 The solid line box part is a schematic structural diagram of the hardware components realized by the above-mentioned structure in the presen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com