Computer information safe method
An information security and computer technology, applied in the field of information security, can solve problems such as user security risks and system efficiency overhead, and achieve the effects of good security, recognition efficiency and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
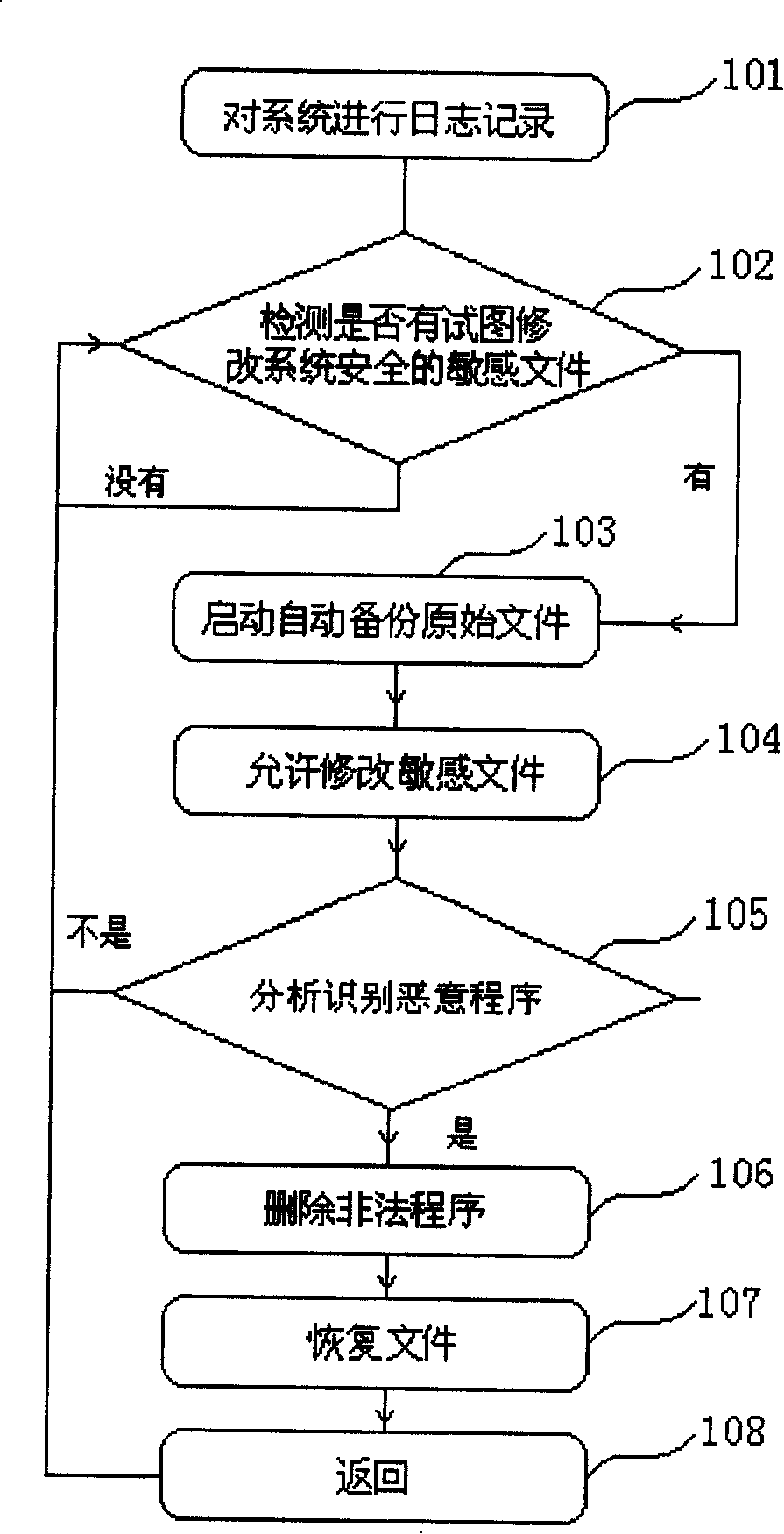
[0043] The main flow of the embodiment of the present invention is as follows figure 1As shown, it at least includes the following steps: step 101, log the system; step 102, detect whether there are sensitive files that try to modify the system security; if not, continue to perform step 102; if so, perform step 103, start automatic backup of the original file; then execute step 104, allow to modify the sensitive files of system security; execute step 105, analyze and identify malicious programs through the operation log records set up in step 101; if yes, execute step 106, delete illegal programs; then complete step 107, according to the The running track of the illegal program restores the contents of the file and the registry modified by the malicious program, so that the system can be restored to the state before the malicious program (and its related malicious programs) run, thereby maintaining the normal operation of the system; and then by the steps Step 108 returns to s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com