Website access analysis system and method based on built-in code proxy log
A website access and analysis method technology, applied in the direction of transmission system, digital transmission system, data exchange network, etc., can solve problems such as inability to embed code, time-consuming, and cookie cannot be generated across domain names, so as to avoid statistical errors and errors Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
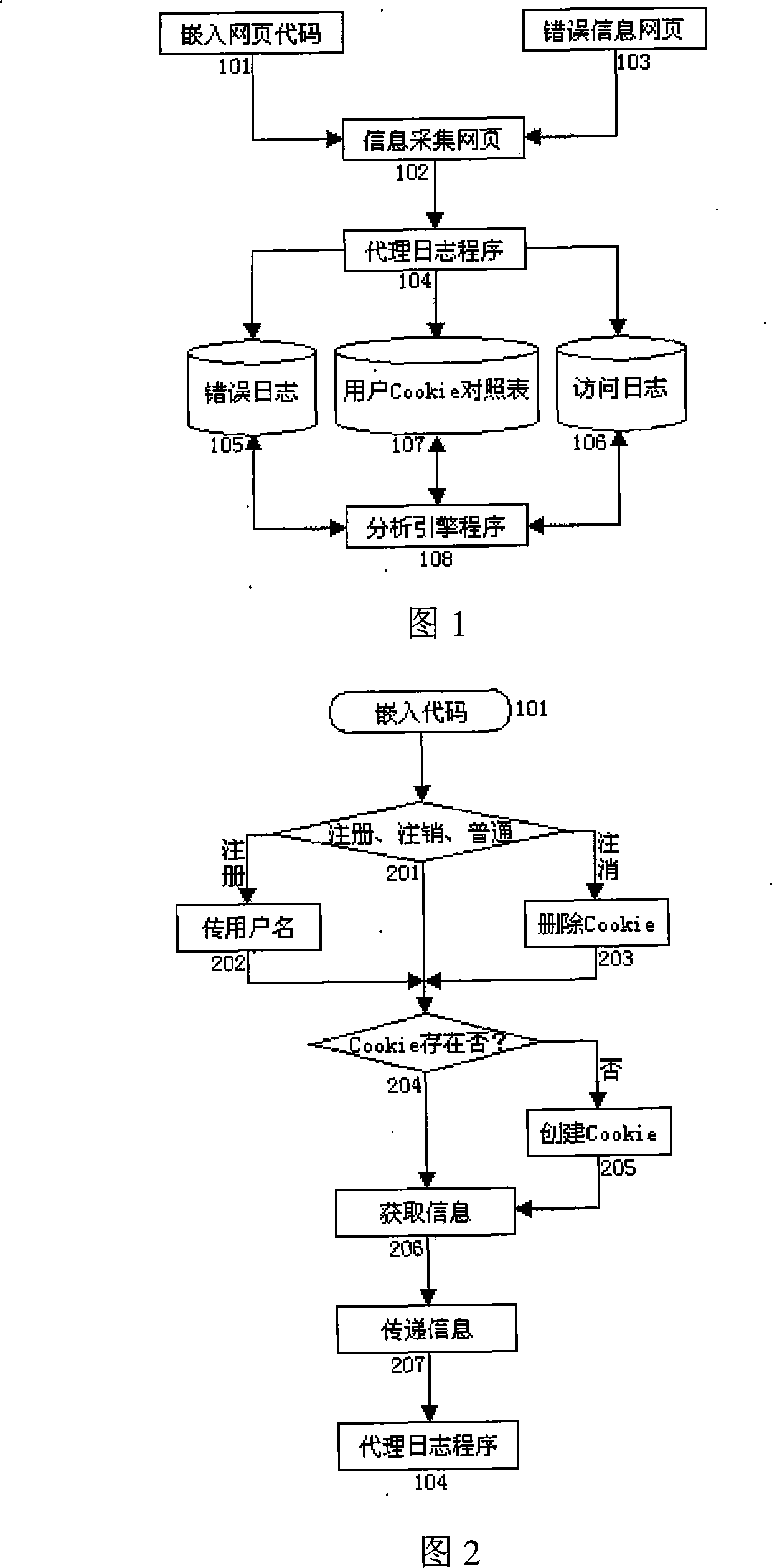
[0041] (1) System installation
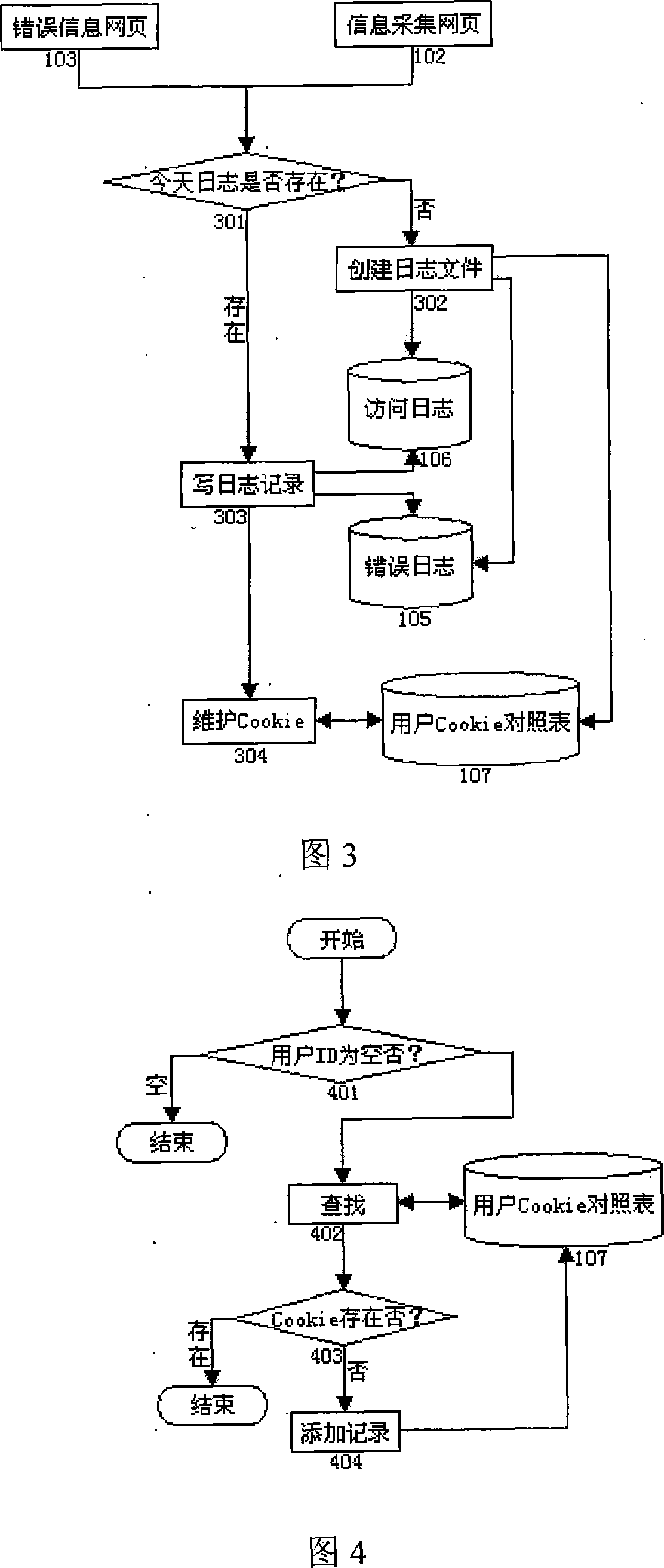
[0042] Proxy log server: set up a web server on the Internet, and install the JavaScript file of the "information collection web page" program and the JSP file program of the "proxy log program" on the server.
[0043] Analysis engine server: establish a web server on the Internet, connect with the "proxy log server" through the network, and install the "analysis engine program" on this server.
[0044] Error information webpage: copy and install the "error information webpage" provided by this system to the server to be analyzed, change the default error information link path of the server, and set various error information prompts to the path where the "error information webpage" file is located.
[0045] Embedding code: in the webpage of the analyzed website, embed the embedding code provided by the present invention, and the "webpage type mark" Page-Flag place notes indicate whether it is a "registration webpage", "logout webpage" or "commo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com