Method for implementing reliable network system based on reliable computation
A technology of trusted computing and network systems, applied in the field of computer networks and trusted computing, can solve problems such as not using network systems, achieve the effects of reducing costs, protecting existing software properties, and enhancing security and credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the features and advantages of the present invention more clearly understood, below in conjunction with accompanying drawing, describe in detail as follows:
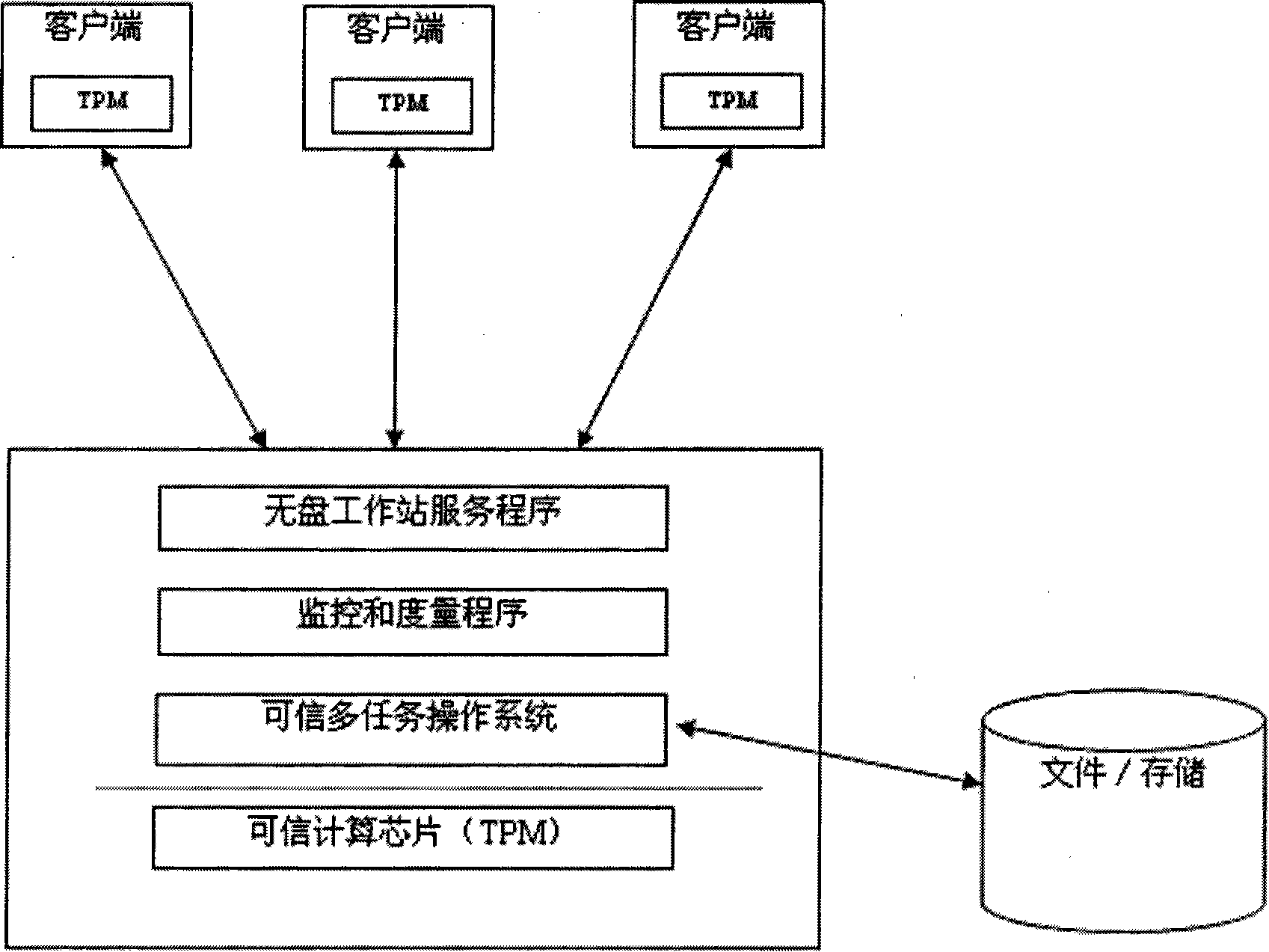
[0032] like figure 1 As shown, it describes the architecture of the trusted network system of the present invention. Several client computers and one server computer are connected to form a local area network through network devices such as hubs, routers, and switches. The server is equipped with a trusted computing chip, installed with a trusted multi-tasking operating system, running monitoring and measurement programs, and a diskless workstation program; the client is also equipped with a trusted computing chip, using a diskless workstation, that is, it does not have local storage capabilities ( including mobile storage).
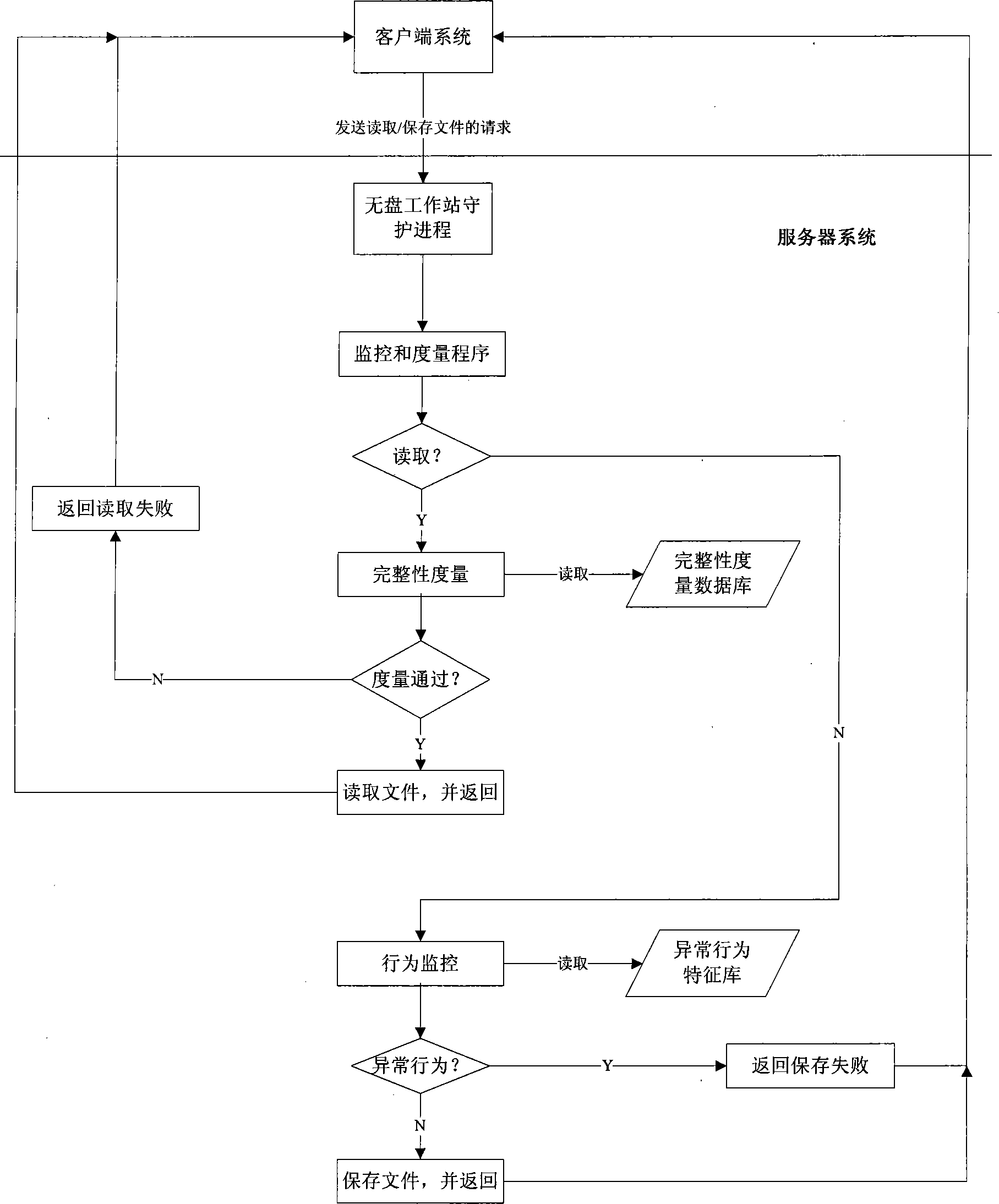
[0033] The trusted multitasking operating system can meet the overall requirements of TCG and TCM specifications, support TPM and TCM chips, realize the integrity measureme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com